While running the workflows through WFH, it is important that plain text passwords are not exposed to users. To achieve this, TCA 3.2 user is required to persist the passwords as a first step at AWS secret manager (if it is integrated with TCA), or WFH’s in-house secret manager. To create the secrets at WFH secret manager, run the following shell script with name create-lcm-cluster-esxi-secrets.sh on any client machine that has connectivity to TCA-M. This script is placed at /opt/vmware/scripts location inside the TCA-M virtual machine for reference. Here the secrets are for the entities TCA, vCenter, and so on.
You cannot run this script from within this TCA-M virtual machine.
Following is a snippet of the script:
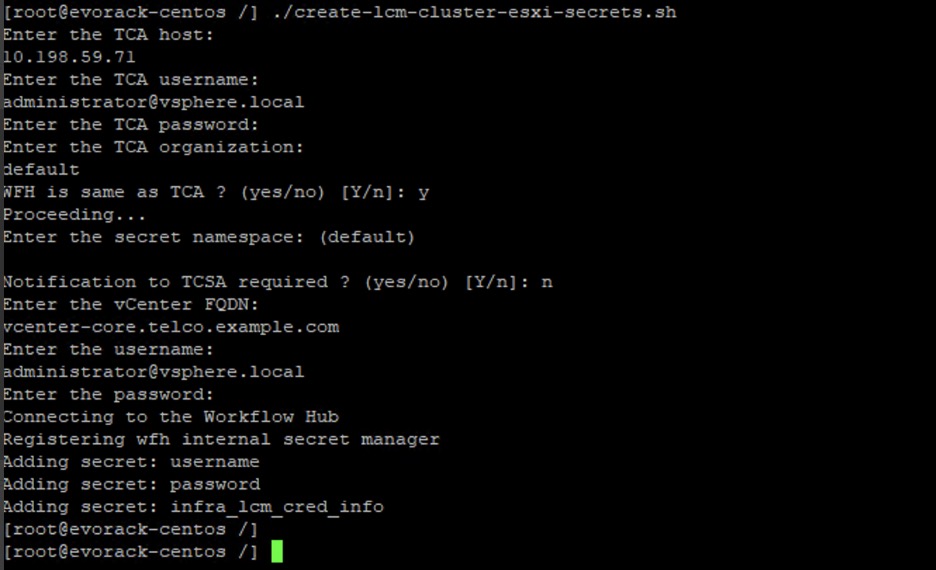
Updates and additions to the existing secret entries can be made by re-running the script. Re-enter all the credentials upon re-running the script.