The management and orchestration systems for the virtualization fabric must be isolated from other networks and closely monitored to track access and changes. Security-critical functions can be separated by using a separate vSphere cluster of the ESXi hypervisor and VMs. NSX isolates security-critical functions further by implementing firewalls and applying micro-segmentation.
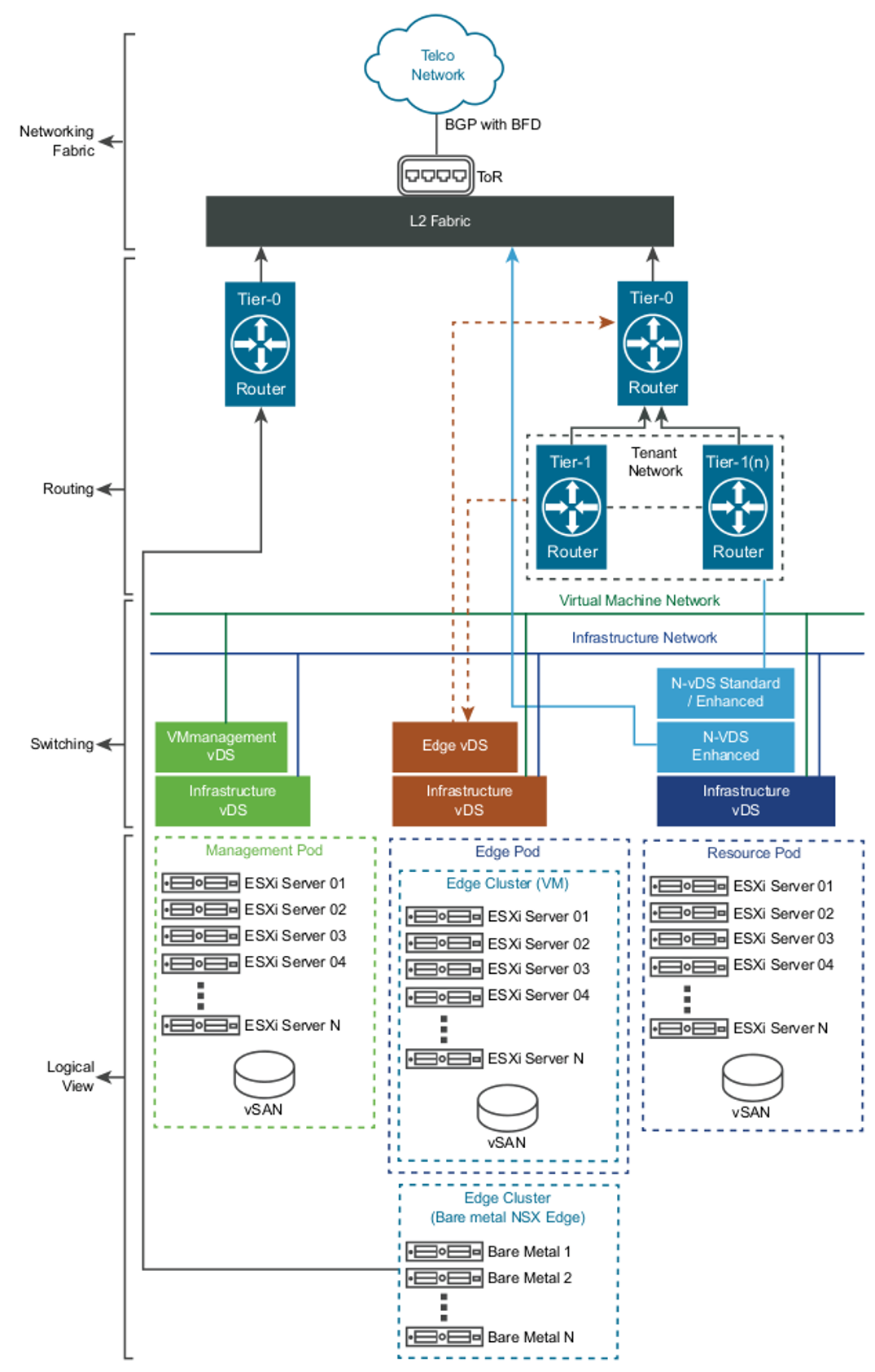
The following diagram depicts the physical representation of the compute and networking connectivity and the logical layers of the switching and routing fabric. This flexible, scalable three-pod design uses a management pod to separate administration from the virtualization fabric.
Containers alone are an inadequate security boundary. Do not use containers to separate different security-critical functions or to separate security-critical functions from other workloads or functions.
VMware components of the management plane, such as vSphere and vCenter, authenticate and authorize users with Microsoft Active Directory or LDAP. These security systems are security-critical functions. A system such as Active Directory must be installed and isolated in its own trusted security domain, not the corporate domain, for the sole purpose of identity management and Kerberos authentication for the management plane. A system that provides multi-factor authentication for the management plane is also a security-critical function. It must also be isolated in its own local, trusted security domain and not the corporate security domain.
As for the monitoring of security-critical functions, VMware Aria Operations for Logs can ingest syslog messages. VMware Aria Operations for Logs includes a built-in syslog server that is active when the VMware Aria Operations for Logs service is running. The syslog server listens on ports 514/TCP, 1514/TCP, and 514/UDP. It ingests log messages sent from other hosts. Ingested messages become searchable in VMware Aria Operations for Logs in near real time to help monitor security-critical functions. For more information, see VMware Aria Operations for Logs as Syslog Server.
To protect sensitive information gathered by VMware Aria Operations for Logs, place the server on a management network segment that is protected by a firewall from the rest of the internal network. For more information, see VMware Aria Operations for Logs Firewall Recommendations. Security controls can safeguard VMware Aria Operations for Logs. For more information, see Security Considerations for VMware Aria Operations for Logs.