This topic explains a role-based access control (RBAC) remediation use-case.
The administrator must grant RBAC for remediation actions of ticketing or messaging category, while limiting a User Groups access to other remediation actions.
- Login to Keycloak UI, refer Accessing Keycloak Console.
- The administrator creates the User Group in Keycloak called the network-operator and creates a user account called network-oper in the group. For more information on the User Group creation in Keycloak, see the KB Article.
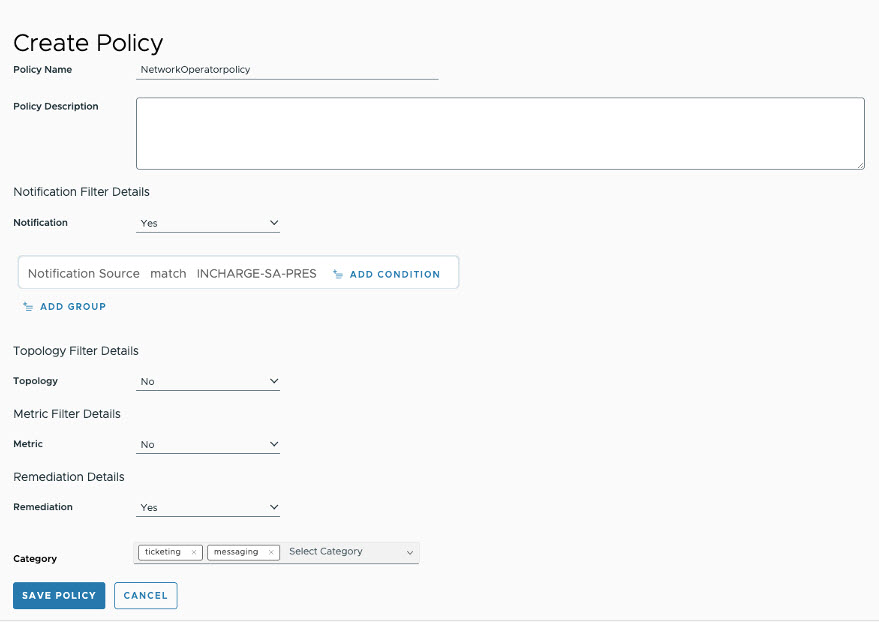
- The administrator creates an Access Policy in the VMware Telco Cloud Service Assurance that allows remediation filters having the category as ticketing and messaging. For Access Policy creation in the VMware Telco Cloud Service Assurance, see the Add Policy topic.
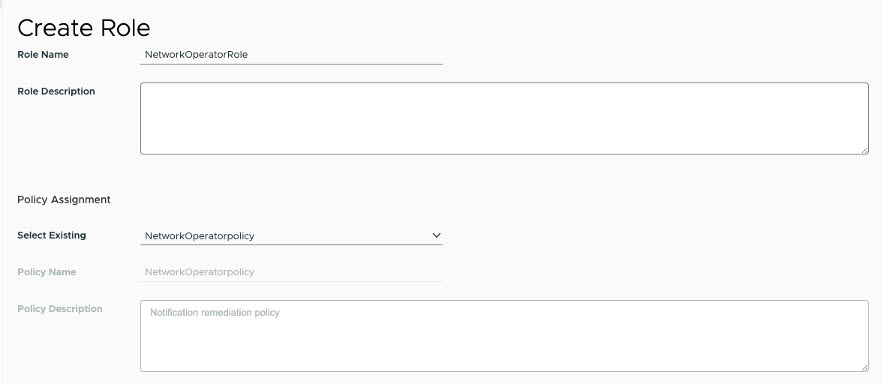
- The administrator creates an Access Role in the VMware Telco Cloud Service Assurance that allows users in this network-operator group/role to use the defined Access Policy for ticketing or messaging categories. For Access Role creation in the VMware Telco Cloud Service Assurance, see the Create a New Role topic.
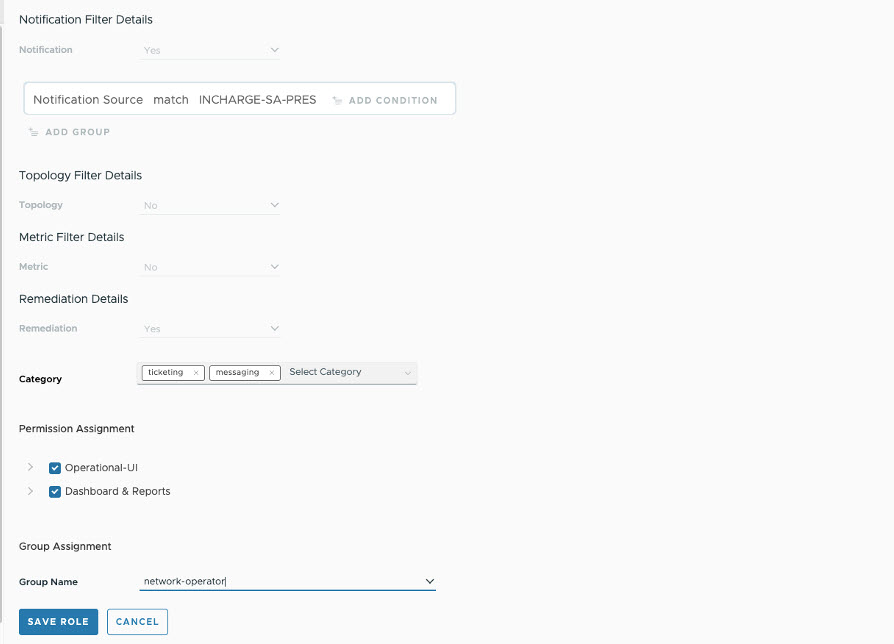
- When the user network-oper (part of the network-operator User Group) views the remediation Actions page, they can view only the pre-defined actions with ticketing or messaging category like
slack_action,servicenow_action, orjira_action. - Only the Remediation Rules with ticketing or messaging type actions are visible to the network-oper user.
- User network-oper can create new Actions of category type ticketing or messaging (not Infra/Network/Service affecting categories like infrastructure/orchestrator/api, and so on).
- User network-oper can run remediations against matching events with actions of category type ticketing or messaging (not Infra/Network/Service affecting categories like infrastructure/orchestrator/api, and so on).