During deployment, the Workspace ONE Access instance is set up inside the internal network. If you want to provide access to the service for users connecting from outside networks, you must install a load balancer or a reverse proxy, such as Apache, Nginx, or F5, in the DMZ.
If you do not use a load balancer or reverse proxy, you cannot expand the number of Workspace ONE Access instances later. You might need to add more instances to provide redundancy and load balancing. The following diagram shows the basic deployment architecture that you can use to enable external access.
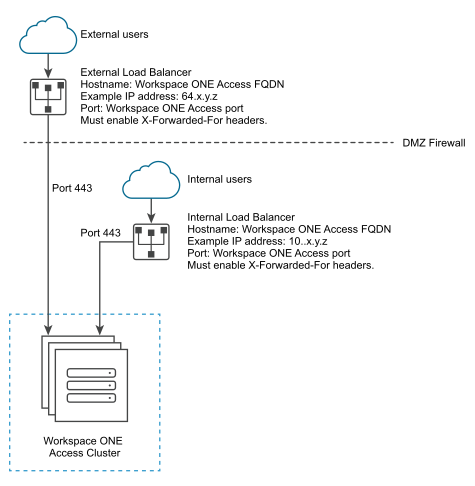
Specify Workspace ONE Access FQDN during Deployment
During the deployment of the Workspace ONE Access appliance, you enter the Workspace ONE Access FQDN and port number. These values must point to the host name that you want end users to access.
The Workspace ONE Access machine always runs on port 443. You can use a different port number for the load balancer. If you use a different port number, you must specify it during deployment. Do not use 8443 as the port number, as this port number is the Workspace ONE Access administrative port and is unique for each machine in a cluster.
Load Balancer Settings to Configure
Load balancer settings to configure include enabling X-Forwarded-For headers, setting the load balancer time-out correctly, and enabling sticky sessions. In addition, SSL trust must be configured between the Workspace ONE Access connector machine and the load balancer.
- X-Forwarded-For Headers
You must enable X-Forwarded-For headers on your load balancer. This determines the authentication method. See the documentation provided by your load balancer vendor for more information.
- Load Balancer Timeout
For Workspace ONE Access to function correctly, you might need to increase the load balancer request timeout from the default. The value is set in minutes. If the timeout setting is too low, you might see this error, “502 error: The service is unavailable”.
- Enable Sticky Sessions
You must enable the sticky session setting on the load balancer if your deployment has multiple Workspace ONE Access machines. The load balancer binds a user's session to a specific instance.
- Do not block session cookies
Do not block session cookies by adding rules to the load balancer. Adding such rules to the load balancer can result in inconsistent behavior and failed requests.
- WebSocket support
The load balancer must have WebSocket support to enable secure communication channels between connector instances and the Workspace ONE Access nodes.
- Ciphers with forward secrecy
Apple iOS App Transport Security requirements apply to the Workspace ONE app on iOS. To enable users to use the Workspace ONE app on iOS, the load balancer must have ciphers with forward secrecy. The following ciphers meet this requirement:
ECDHE_ECDSA_AES and ECDHE_RSA_AES in GCM or CBC mode
as stated in the iOS 11 iOS Security document:
"App Transport Security provides default connection requirements so that apps adhere to best practices for secure connections when using NSURLConnection, CFURL, or NSURLSession APIs. By default, App Transport Security limits cipher selection to include only suites that provide forward secrecy, specifically ECDHE_ECDSA_AES and ECDHE_RSA_AES in GCM or CBC mode."