To install the Directory Sync, User Auth, or Kerberos Auth services, run the Workspace ONE Access connector installer on a Windows server that meets all the requirements and select the services you want to install.
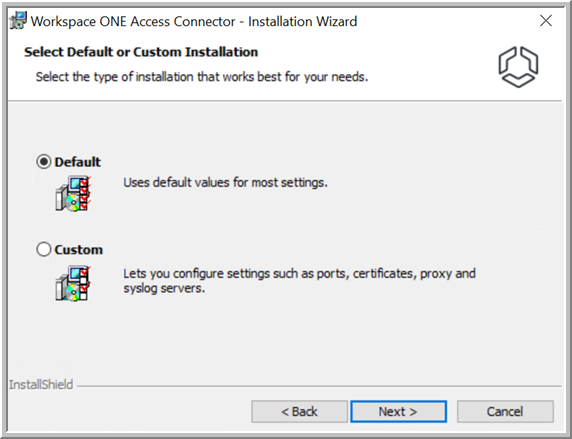
You can choose between a quick, default installation that uses default values for most settings or a custom installation that lets you configure various settings.
| Default Installation |
Custom Installation |
Uses the following default ports:
- User Auth Service: 8090
- Directory Sync Service: 8080
- Kerberos Auth Service: 443
Note: These are the ports the services run on. Inbound connectivity is required for the Kerberos Auth service port only.
|
Lets you specify custom ports for the enterprise services
Note: These are the ports the services run on. Inbound connectivity is required for the Kerberos Auth service port only.
|
| Auto-generates a self-signed certificate for the connector |
Lets you install a trusted SSL certificate for the connector (required for Kerberos Auth Service) |
|
Lets you upload trusted root certificates to the truststore
Note: If your on-premises Workspace ONE Access service instance has a self-signed certificate that you installed, you must upload its root, and, if required, intermediate certificate to establish trust between the enterprise services and the Workspace ONE Access service instance.
|
|
Lets you configure a proxy server |
|
Lets you configure a syslog server |
Regardless of the type of installation you choose, you can run the installer again later and modify all the settings as needed.
Prerequisites
- See Prerequisites for Installing the Workspace ONE Access Connector.
- As part of the installation process, you download files from the Workspace ONE Access console. You might need to use a browser other than Internet Explorer to download the files. Default Internet Explorer settings might prevent you from downloading the files.
Procedure
- Download the Workspace ONE Access connector installer and a configuration file from the Workspace ONE Access console.
- Log in to the Workspace ONE Access console as the System domain admin.
Tip: In cloud deployments, the System domain admin is the admin whose credentials you receive when you get your
Workspace ONE Access tenant. In on-premises deployments, the System domain admin is the admin user that is created when you install a
Workspace ONE Access instance.
- Navigate to the page.
- Click New.
- In the Virtual Apps Usage confirmation dialog box, review the information, then select Workspace ONE Access Connector 20.10.
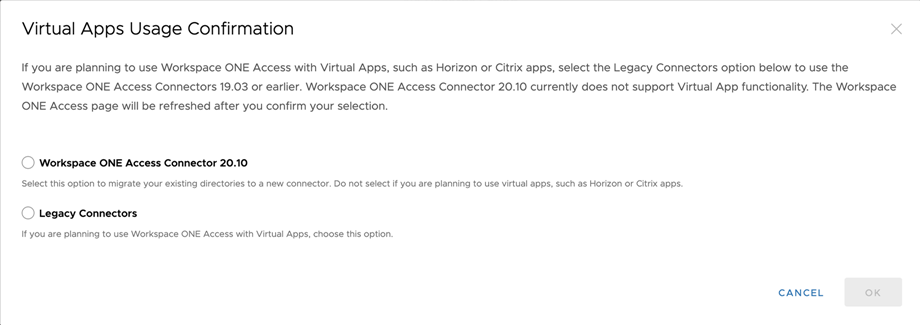
Caution: Workspace ONE Access Connector 20.10 does not support Virtual Apps (Horizon, Horizon Cloud, Citrix, and ThinApps integrations). Do not install the 20.10 connector if you plan to integrate Virtual Apps. To use Virtual Apps, select
Legacy Connectors and install connector versions 19.03.0.1 or earlier. To integrate Horizon, Horizon Cloud, or Citrix applications and desktops, use VMware Identity Manager connector (Windows) version 19.03.0.1. To integrate ThinApp packaged applications, use VMware Identity Manager connector (Linux) version 2018.8.1.0.
Note: The Virtual Apps Usage Confirmation dialog box appears the first time you install a new connector in your tenant. If you want to change your selection later, you can use the
Reset Virtual Apps Usage button that appears subsequently on the Connectors or Legacy Connectors page. See
Resetting Virtual Apps Usage Option in Workspace ONE Access for more information.
- Review the information in the confirmation dialog box, then click Proceed Anyway if you want to proceed.
The Add New Connector wizard appears.
- In the Add New Connector wizard, click GO TO MYVMWARE.COM.
The My VMware web page appears in a new window. Keep the wizard open as you will return to it after downloading the installer.
- Log in to https://my.vmware.com with your My VMware login and download the Workspace ONE Access Connector Installer.exe file.
- Return to the Workspace ONE Access console and click Next in the Add New Connector wizard.
- Generate the configuration file by creating a password and clicking Download Configuration File.
The password must have a minimum of 14 characters and include an uppercase character, a lowercase character, a numeric digit, and a special character. Do not use the & or % characters. All characters must be visible, printing ASCII characters.
The configuration file is used to establish communication between the enterprise services you install and the Workspace ONE Access tenant. The file is named
es-config.json by default.
Caution: The configuration file contains sensitive information such as the tenant URL, tenant ID, the client ID and client secret for each of the enterprise services, and the password hash. It is critical that you do not share the file or expose it publicly.
- After downloading the configuration file, click Next in the wizard.
- Copy the installer and configuration files to the Windows server on which you want to install the services.
- Double-click the installer file to run the Workspace ONE Access connector installation wizard.
- On the Welcome page, click Next.
The installer verifies prerequisites on the server. If .NET Framework is not installed, you are prompted to install it and to restart the server. After restarting, run the installer again to resume the installation process.
- Read and accept the license agreement, then click Next.
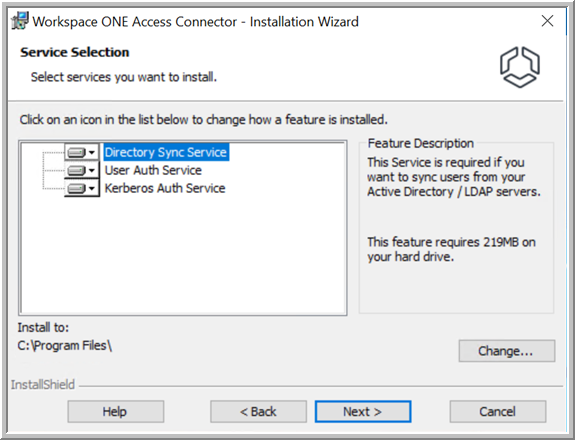
- Select the services you want to install.
By default, the services are installed in
C:\Program Files. To change the installation folder, click
Change and select the folder.
- Click Next.
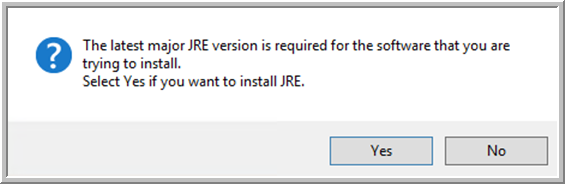
- If the latest, major version of the Java Runtime Environment (JRE™) is not already installed on the Windows server, the following pop-up appears.
Click
Yes to install JRE. The installation takes a few minutes. Existing JRE versions are not deleted when the required version is installed.
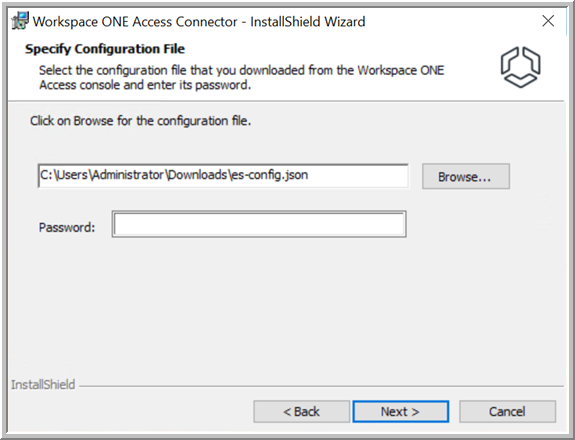
- On the Specify Configuration File page, select the configuration file that you downloaded from the Workspace ONE Access console, enter the password that you set, then click Next.
If the configuration file is in the same folder as the installer and has the default name
es-config.json, it appears in the text box automatically.
- Select between Default and Custom installation.
- If you selected Default installation, follow these steps.
- (Kerberos Auth service only) On the Specify Service Account page, specify the user name and password of the domain user account to use to run the Kerberos Auth service.
Enter the
User name in the format
DOMAIN\Username, such as
EXAMPLE\administrator. Alternatively, click
Browse and select the domain and user.
If you are unable to locate domains or users when you click Browse, type them in the text box in the format specified above.
Important: The Kerberos Auth service only supports the following special characters in the domain user account password:
@!*. If the password contains any other special characters, Kerberos Auth service installation fails.
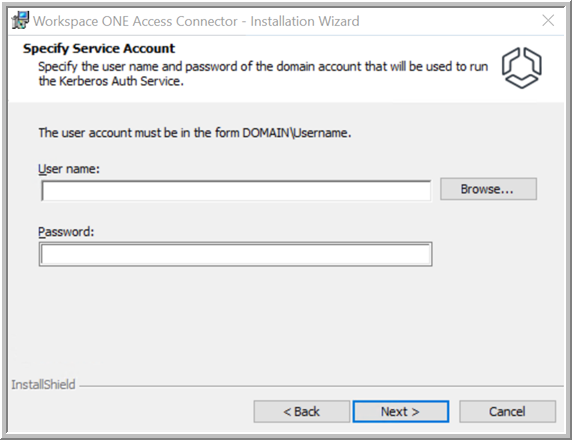
Note: The Specify Service Account page appears only if you are installing the Kerberos Auth service.
- Click Next.
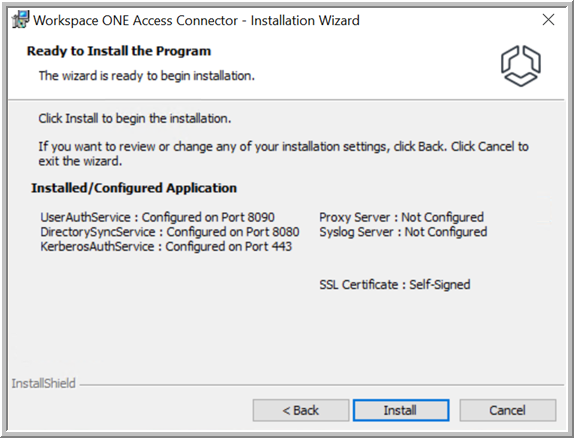
- In the Ready to Install the Program page, review your selections, then click Install.
The installation takes a few minutes.
- If you selected Custom installation, follow these steps.
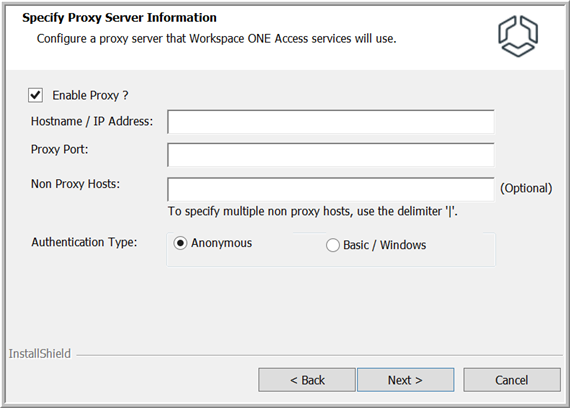
- In the Specify Proxy Server Information page, enter a proxy server, if required.
The enterprise services access Web services on the Internet. If your network configuration provides Internet access through an HTTP proxy, you must enter a proxy server.
You can also specify a list of non-proxy hosts, hosts that should be reached directly without going through the proxy server.
- Select the Enable Proxy check box.
- Enter the host name, specified as a fully qualified domain name (FQDN), or IP address of the proxy server.
- Enter the proxy server port.
- If you want to specify any non-proxy hosts, hosts that should be reached directly without going through the proxy server, enter the FQDN or IP address in the Non Proxy Hosts text box. Use the following format, with each entry separated by |:
host1|host2
- If the proxy server requires authentication, select Basic/Windows and enter the user name and password for the proxy server.
- Click Next.
- On the Specify Syslog Server page, if you want to use one or more external syslog servers to store application-level event messages, select the Enable Syslog option and enter each syslog server's IP address or FQDN, and port.
To specify a single syslog server, use the following format:
host:port
To specify multiple syslog servers, use the following format:
host:port,host:port,host:port
where host is the fully qualified domain name or IP address of the syslog server and port is the port number. For example:
syslog1.example.com:54
or
syslog1.example.com:514,syslog2.example.com:601,syslog3.example.com:163
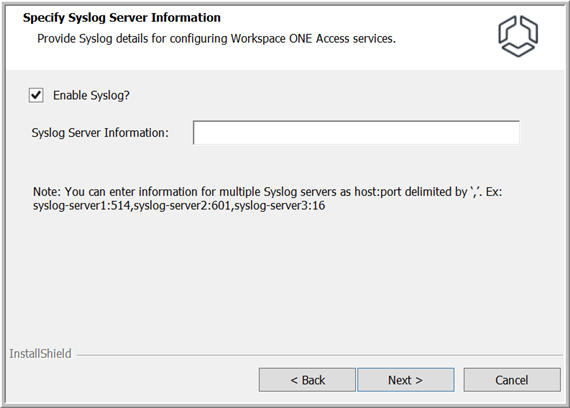
Note: Only application-level events are exported to syslog servers. Operating system events are not exported.
- Click Next.
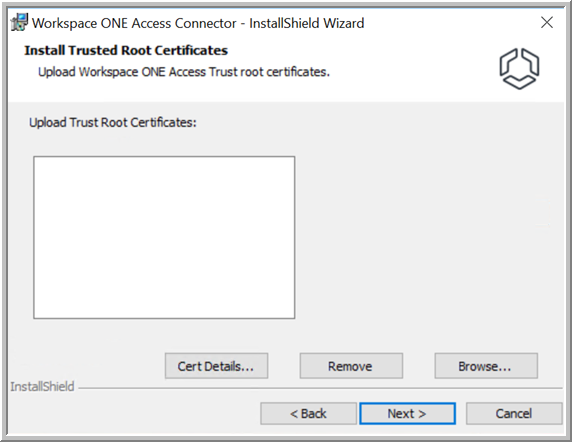
- On the Install Trusted Root Certificates page, upload root or intermediate CA certificates to the truststore, if required.
The connector will be able to establish secure connections to servers and clients whose certificate chain includes any of these certificates. Scenarios for uploading certificates to the truststore include:
- (On-premises installations only) If your on-premises Workspace ONE Access service instance has a self-signed certificate that you installed, you must upload its root, and, if required, intermediate certificate to establish trust between the enterprise services and the Workspace ONE Access service instance.
- (Kerberos Auth service only) If you deploy multiple instances of the Kerberos Auth service behind a load balancer, you must install the load balancer's root CA certificate on the connector instances to establish trust between the connectors and the load balancer.
You can also upload trusted root certificates later, after installation.
- Click Next.
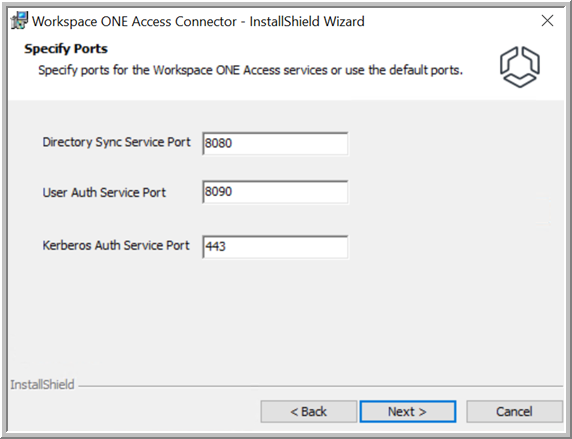
- Review the default ports that the enterprise services run on, and specify different ports if these ports are being used by other applications.
Inbound connectivity is required for the Kerberos Auth service port only. It is not required for the User Auth or Directory Sync service ports.
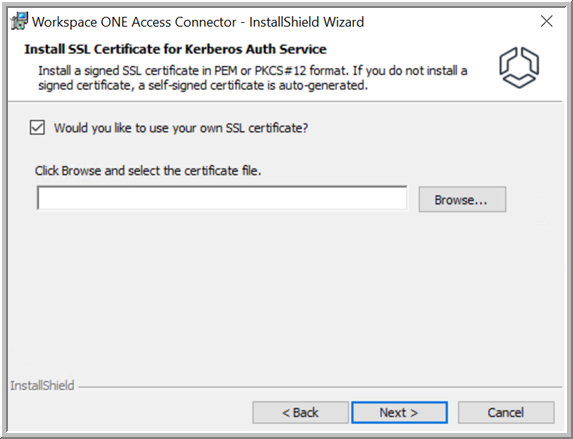
- (Kerberos Auth service only) On the SSL Certificate for Kerberos Auth Service page, select the certificate to use for the connector server.
A trusted SSL certificate signed by a public or internal CA is required for the Kerberos Auth service. If you do not upload a trusted SSL certificate during installation, a self-signed certificate is auto-generated. You can upload a trusted SSL certificate later.
- To upload a trusted SSL certificate, select the Would you like to use your own SSL certificate? check box, click Browse, and select the certificate file.
The certificate file must be in PEM or PFX format. If you upload a PEM file, also upload the private key. If you upload a PFX file, also specify the certificate password. For information about certificate requirements, see Uploading an SSL Certificate for the Workspace ONE Access Connector (Kerberos Auth Service Only).
- To use the auto-generated, self-signed certificate, deselect the Would you like to use your own SSL certificate? check box.
Note: If you use the Workspace ONE Access generated self-signed certificate, you will need to add the root certificate generated by Workspace ONE Access to clients' truststores. You can get the root certificate,
root_ca.per, from
INSTALLDIR\Workspace ONE Access\Kerberos Auth Service\conf after installation.
While you can use the self-signed certificate for testing purposes, trusted SSL certificates signed by a public or internal CA are recommended for production usage.
- Click Next.
- (Kerberos Auth service only) On the Specify Service Account page, specify the user name and password of the domain user account to use to run the Kerberos Auth service.
Enter the
User name in the format
DOMAIN\Username, such as
EXAMPLE\administrator. Alternatively, click
Browse and select the domain and user.
If you are unable to locate domains or users when you click Browse, type them in the text box in the format specified above.
Important: The Kerberos Auth service only supports the following special characters in the domain user account password:
@!*. If the password contains any other special characters, Kerberos Auth service installation fails.

Note: The Specify Service Account page appears only if you are installing the Kerberos Auth service.
- In the Ready to Install the Program page, review your selections, then click Install.
The installation takes a few minutes.
- After installation finishes successfully, verify that the services are running on the Windows server.
Service names:
- VMware Directory Sync Service
- VMware User Auth Service
- VMware Kerberos Auth Service
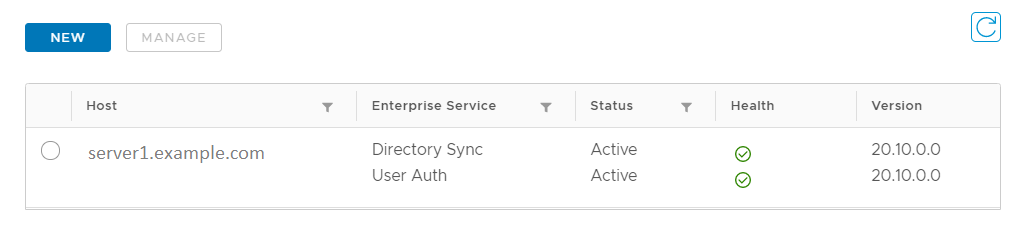
- Go to the Workspace ONE Access console and refresh the page to verify that the new services appear and are in Active state.
If the installation fails, delete both the installer and the configuration file that you downloaded from the
Workspace ONE Access console, then start the installation process again.
Results
After successful installation, the enterprise services that you installed are registered with the Workspace ONE Access tenant and appear on the Connectors page in the Workspace ONE Access console.
For example: