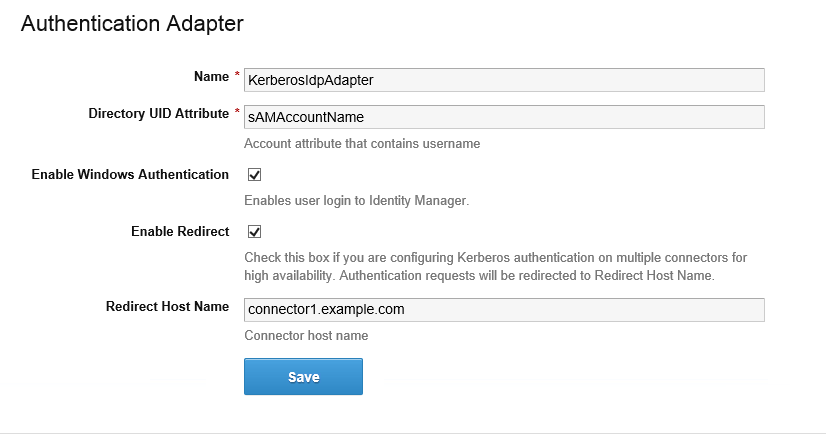
Configure and enable the KerberosIdpAdapter on the VMware Identity Manager connector. If you have deployed a cluster for high availability, configure and enable the adapter on all the connectors in your cluster.
When you configure the Kerberos authentication adapter, the VMware Identity Manager connector attempts to initialize Kerberos automatically. If the VMware IDM Connector service is not being run with sufficient privileges to initialize Kerberos, an error message appears. In this case, follow the instructions in http://kb.vmware.com/kb/2149753 to run a script to initialize Kerberos.
For more information about configuring Kerberos authentication, see the VMware Identity Manager Administration Guide.
Prerequisites
- The Windows machine on which the VMware Identity Manager connector is installed must be joined to the domain.
- You must have installed the VMware Identity Manager connector as a domain user that is part of the administrator group on the Windows machine on which the connector is installed, and you must be running the VMware IDM Connector service as a Windows domain user.
Procedure
What to do next
- Ensure that each connector on which the KerberosIdpAdapter is enabled has a trusted SSL certificate. You can obtain the certificate from your internal certificate authority. Kerberos authentication does not work with self-signed certificates.
Trusted SSL certificates are required regardless of whether you enable Kerberos on a single connector or on multiple connectors for high availability.
- Set up high availability for Kerberos authentication, if necessary. Kerberos authentication is not highly available without a load balancer.