You can add Kerberos authentication for internal users, which requires inbound connection mode, to your deployment of outbound connection mode connectors. The same connectors can be configured to use Kerberos authentication for users coming from the internal network and another authentication method for users coming from the external network. This can be achieved by defining authentication policies based on network ranges.
The following diagram depicts Kerberos authentication in an on-premises VMware Identity Manager deployment.
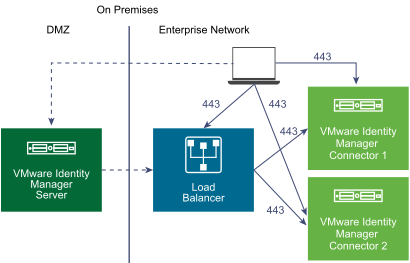
Requirements and considerations for Kerberos authentication include the following:
- Kerberos authentication can be configured regardless of the type of directory you set up in VMware Identity Manager, Active Directory over LDAP or Active Directory over Integrated Windows Authentication.
- The Windows machine on which the VMware Identity Manager connector is installed must be joined to the Active Directory domain.
- You must have installed the VMware Identity Manager connector as a domain user that is part of the administrator group on the Windows machine on which the connector is installed, and you must be running the VMware IDM Connector service as a Windows domain user.
- Ensure that you select an appropriate, user-friendly host name for the connector. The VMware Identity Manager connector host name is visible to end users when Kerberos authentication is configured.
- Each connector on which Kerberos authentication is configured must have a trusted SSL certificate. You can obtain the certificate from your internal certificate authority. Kerberos authentication does not work with self-signed certificates.
Trusted SSL certificates are required regardless of whether you enable Kerberos on a single connector or on multiple connectors for high availability.
- To set up high availability for Kerberos authentication, a load balancer is required.