While configuring your network, you must take security measures into account whether you are in a SaaS or an on-premises environment.
SaaS Configurations
With a cloud-based implementation, the Workspace ONE Assist software is delivered as a service (SaaS). The integration between your Workspace ONE UEM SaaS tenant and your Workspace ONE Assist SaaS deployment is configured for you.
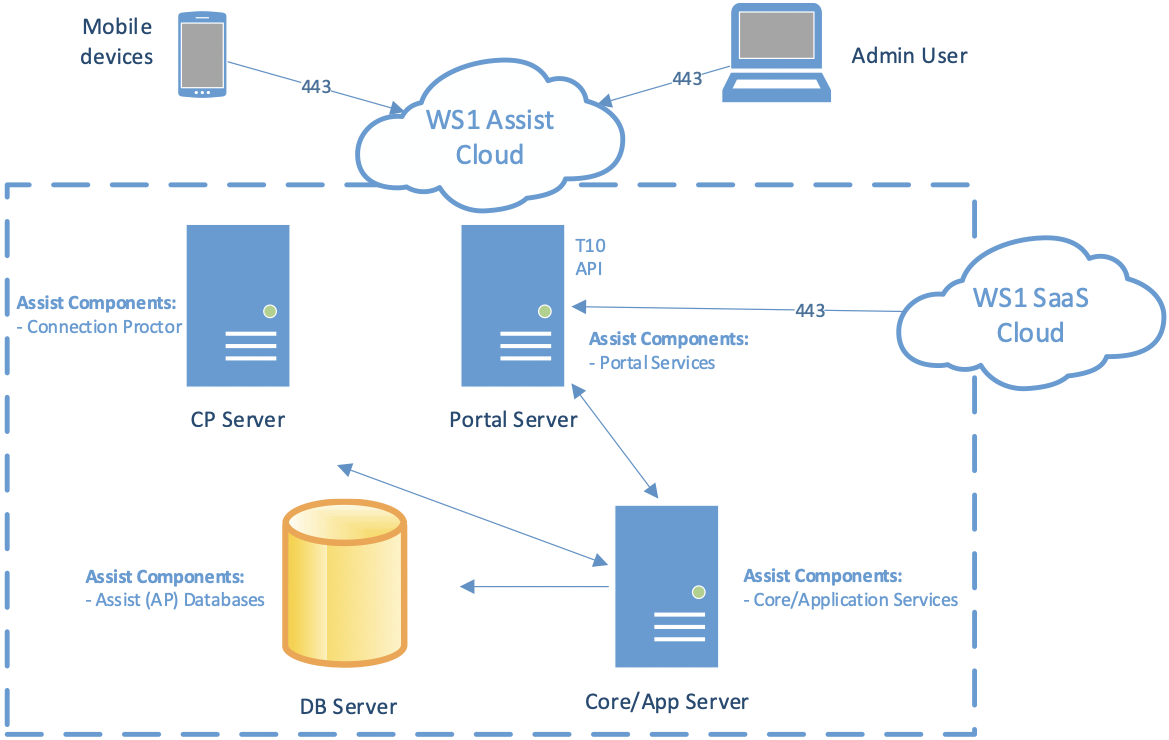
If you want your Workspace ONE Assist to run in a SaaS configuration, you must whitelist the following fully qualified domain names (FQDNs) and IP addresses.
The FQDNs and IPs are region specific, so add these to your whitelist based on your location. The port is 443.
- US Portal Server - https://rm01.awmdm.com 52.207.131.208
- US CP Server 01 rmsession01.awmdm.com 52.207.186.27
- US CP Server 02 rmsession02.awmdm.com 34.195.109.57
- US CP Server 03 rmsession03.awmdm.com 3.224.230.18
- US CP Server 04 rmsession04.awmdm.com 52.200.22.165
- US CP Server 05 rmsession05.awmdm.com 3.221.52.58
- US CP Server 06 rmsession06.awmdm.com 18.211.168.20
-
US-Stage Portal - https://rmstage01.awmdm.com 52.44.65.104
-
CP Server 01 - rmstagesession01.awmdm.com 3.227.221.87
-
CP Server 02 - rmstagesession02.awmdm.com 34.198.201.137
-
CP Server 03 - rmstagesession03.awmdm.com 34.199.170.251
-
CP Server 04 - rmstagesession04.awmdm.com 34.232.175.250
- UK Portal Server https://rmuk01.awmdm.com 35.176.238.148
- CP Server 01rmuksession01.awmdm.com 35.177.197.211
- CP Server 02 - rmuksession02.awmdm.com 18.134.187.214
- CP Server 03 - rmuksession03.awmdm.com 18.130.62.109
- CP Server 04 - rmuksession04.awmdm.com 18.133.86.204
- Canada Portal Server https://rmca01.awmdm.com 52.60.162.133
- CP Server 01rmcasession01.awmdm.com 52.60.196.137
- CP Server 02 - rmcasession02.awmdm.com 3.97.76.95
- CP Server 03 - rmcasession03.awmdm.com 52.60.228.68
- CP Server 04 - rmcasession04.awmdm.com 52.60.238.231
- Germany Portal Server - https://rmde01.awmdm.com 52.28.212.69
- CP Server 01 - rmdesession01.awmdm.com 52.28.80.78
- CP Server 02 - rmdesession02.awmdm.com 18.198.82.223
- CP Server 03 - rmdesession03.awmdm.com 18.193.90.93
- CP Server 04 - rmdesession04.awmdm.com 18.158.119.201
- Australia Portal Server https://rmau01.awmdm.com 52.62.156.193
- CP Server 01rmausession01.awmdm.com 13.55.186.162
- CP Server 02 - rmausession02.awmdm.com 54.153.185.165
- CP Server 03 - rmausession03.awmdm.com 54.253.57.82
- CP Server 04 - rmausession04.awmdm.com 54.79.90.228
- Japan Portal Server https://rmjp01.awmdm.com 52.193.23.235
- CP Server 01 rmjpsession01.awmdm.com 52.199.112.44
- CP Server 02 - rmjpsession02.awmdm.com 54.168.82.186
- CP Server 03 - rmjpsession03.awmdm.com 52.196.79.150
- CP Server 04 - rmjpsession04.awmdm.com 54.168.192.92
- Singapore Portal Server - https://rmsg01.awmdm.com 13.250.134.26
- CP Server 01 - rmsgsession01.awmdm.com 54.151.204.98
- CP Server 02 - rmsgsession02.awmdm.com 54.179.206.192
- CP Server 03 - rmsgsession03.awmdm.com 54.255.1.80
- CP Server 04 - rmsgsession04.awmdm.com 13.214.235.227
- India Portal Server - https:// rmin01.awmdm.com 35.154.254.172 (Effective from March 28, 2024)
- CP Server 01 - rminsession01.awmdm.com 3.109.223.16 (Effective from March 28, 2024)
- CP Server 02 - rminsession02.awmdm.com 3.110.246.118 (Effective from March 28, 2024)
- CP Server 03 - rminsession03.awmdm.com 3.7.30.26 (Effective from March 28, 2024)
- CP Server 04 - rminsession04.awmdm.com 15.207.210.57 (Effective from March 28 2024)
For more information, please see the following knowledge base article, https://kb.vmware.com/s/article/82567?lang=en_US
SaaS and On-Prem Config: Additional Network Requirements to Enable Firebase Cloud Messaging (FCM)
You can configure the Android Assist agent to receive a Firebase Cloud Message (FCM) directly from the Assist server during the connection process. Together with Workspace ONE Intelligent Hub for notifications, this configuration improves the establishment speed and reliability of connections, thus minimizing request timeouts and improving the overall admin experience.
To receive FCM notifications, the following endpoints must be accessible on the end user devices.
| Destination Host | Ports | Purpose |
|---|---|---|
| fcm.googleapis.com, fcm-xmpp.googleapis.com | TCP/443, 5228-5230 | Firebase Cloud Messaging (for example Find My Device, EMM Console <-> DPC communication, like pushing configs) |
On-Prem Config: IP Address and Port Translation, Single-Server On-Prem Deployment
The Workspace ONE Assist server is required to have one static IPv4 address. This address must be accessible from the mobile device network and the network from which Workspace ONE UEM users access the Workspace ONE Assist web portal. This IP address is translated to the all-in-one server’s Portal (web) services and Connection Proctor (CP) services.
By default, web services are bound to port 443 and 80 and CP services are bound to port 8443, however, your IT team can customize these ports. If Network Address Translation (NAT) is used, one public facing static IP address is required translated to the internal IP address of the Workspace ONE Assist server.
| Port | Service |
|---|---|
| 80 * | Assist Internal Services |
| 443 * | Portal Services and T10 API |
| 8443 * | Connection Proctor Service |
* Customizable port address
On-Prem Config: IP Address and Port Translation, Medium and Multiple-Server On-Prem Deployment
Each Connection Proctor server must have its own static IPv4 address that is accessible from the device network and the user network that is translated to the CP service using port 443. The server hosting Workspace ONE Assist Web/Portal Services must also have its own static IP address that is accessible from the device network and Workspace ONE UEM user network. The portal services are bound to port 443 and 80, however, your IT team can customize these ports.
If network address translation (NAT) is used, the public facing IP addresses must be translated to the internal IP addresses of the servers accordingly.
Core and application components and corresponding services can be deployed on a public facing server or in a private zone. CP services and Portal services must be able to communicate with these core and application services over of a range of ports.
| Port | Service |
|---|---|
| 80* | Portal Services on Portal Server |
| 443* | Portal Services and T10 API |
| 443* | Connection Proctor Service on CP Server. In a multiple server deployment, the CP server can have port 443. Port 8443 is not necessary since the server has 443 available. |
| 8865 | Data Tier Proxy (DTP) |
| 8866 | Messaging Entity (MSG) |
| 8867 | Data Access Proxy (DAP) |
| 8870 | Service Coordinator (SVC) |
| 12780 | Connection Proctor (CP) from Management Entity (ME) |
| 20879 | Management Entity |
* Customizable port address
Database services are deployed on the database server. The Workspace ONE Assist system connects to the database server using an IP address, hostname, or instance name. Typically, SQL database allows connections on port 1433.
On-Prem Config: Persistence for Multiple Server On-Prem Deployment
Workspace ONE Assist supports IP and SSL persistence. SSL persistence is required for connection proctor servers as the SSL termination must be made at the server level.
SSL persistence is also required for T10 service communication. An SSL certificate must be present on the T10 server since this communication cannot be offloaded.
On-Prem Config: Firewall Rules, Single-Server On-Prem Deployment
Firewall rules can be summarized based on the number of allocated IP addresses to the Workspace ONE Assist system.
| Source | Destination | Protocol | Port | Direction | Rule |
|---|---|---|---|---|---|
| Device and User Networks / Internet | CP Server | TCP/TLS/SSL | 8443 | Inbound | Accept |
| Device and User Networks / Internet | Portal Server | TCP/HTTPS | 443 | Inbound | Accept |
| Workspace ONE portal server | Portal Server (T10 Interface) | TCP/HTTPS | 443 | Inbound | Accept |
| Workspace ONE Assist server | MS SQL Database Server | TCP | 1433 | Inbound | Accept |
On-Prem Config: Firewall Rules, Multiple Server On-Prem Deployment
| Source | Destination | Protocol | Port | Direction | Rule |
|---|---|---|---|---|---|
| Device and User Networks / Internet | CP Server | TCP/TLS/SSL | 443 In a multiple server deployment, the CP server can use port 443. Port 8443 is not necessary since the server has 443 available. |
Inbound | Accept |
| Device and User Networks / Internet | Portal Server | TCP/HTTPS | 443 | Inbound | Accept |
| Workspace ONE portal server | Portal Server (T10 Interface) | TCP/HTTPS | 443 | Inbound | Accept |
| CP Server and Portal Server | Core/App Server | TCP | 8865, 8866, 8867, 8870 | Inbound | Accept |
| Core/App Server | CP Server | TCP | 12780 | Inbound | Accept |
| Core/App Server | Database Server | TCP | 1433 | Inbound | Accept |
On-Prem Config: Fully Qualified Domain Name and Site SSL/TLS Certificate, Single-Server On-Prem Deployment
The Workspace ONE Assist system requires one FQDN assigned to the static IP address which is used for Portal Services and for Connection Proctor services.
The Site SSL/TLS certificate has the following attributes in a single-server deployment:
- It is used for TLS/SSL bindings for Portal services.
- It is used in IIS for the Portal Services bound to port 443.
- It corresponds to the FQDN.
- It is used for the Connection Proctor Service bound to port 8443.
- It contains both public and private key pairs.
- It must be installed on the Workspace ONE Assist server’s personal certificate store before the Workspace ONE Assist software is installed.
Obtain your SSL/TLS certificate from a well-known certificate authority such as Comodo, GoDaddy, and so on. If you prefer a self-signed certificate, then you must establish trust between the Assist Agent and the self-signed certificate.
On-Prem Config: Fully Qualified Domain Name and Site SSL/TLS Certificate, Multiple Server On-Prem Deployment
One FQDN is assigned to the Portal server and one FQDN is assigned to each CP server deployed in the Assist system. If a single CP server is deployed, you must have 2 FQDNs. If 2 CP servers are deployed, then 3 FQDNs are required, and so on.
You can obtain a SAN or wildcard site SSL/TLS certificate used for TLS/SSL IIS bindings for the Portal Services. The same SAN or wildcard certificate can be used for the CP servers to bind the CP services. If you have a separate SSL/TLS certificate for each server, then each server must have its own certificate installed. The certificates must correspond to the FQDN assigned to the servers. The certificates must contain both private and public key pairs and they are installed on the server’s local machine certificate store.
Obtain your SSL/TLS certificates from a well-known certificate authority such as Comodo, GoDaddy, and so on. If you prefer a self-signed certificate, then you must establish trust between the Assist Agent and the self-signed certificate.