Before you can do anything in Workspace ONE UEM, you must first log in to the console.
Before you can log in to the Workspace ONE UEM console, you must have the Environment URL and log in credentials. How you obtain this information depends on your type of deployment.
- SaaS Deployment – Your Account Manager provides your Environment URL and user name/password. The URL is not customizable, and generally follows the format of awmdm.com.
- On-premises – The on-premises URL is customizable and follows the format awmdm.<YourCompany>.com.
Your Account Manager provides the initial setup credentials for your environment. Administrators who create more accounts to delegate management responsibility can also create and distribute credentials for their environment.
After your browser has successfully loaded the console Environment URL, you can log in using the User Name and Password provided by your Workspace ONE UEM administrator.
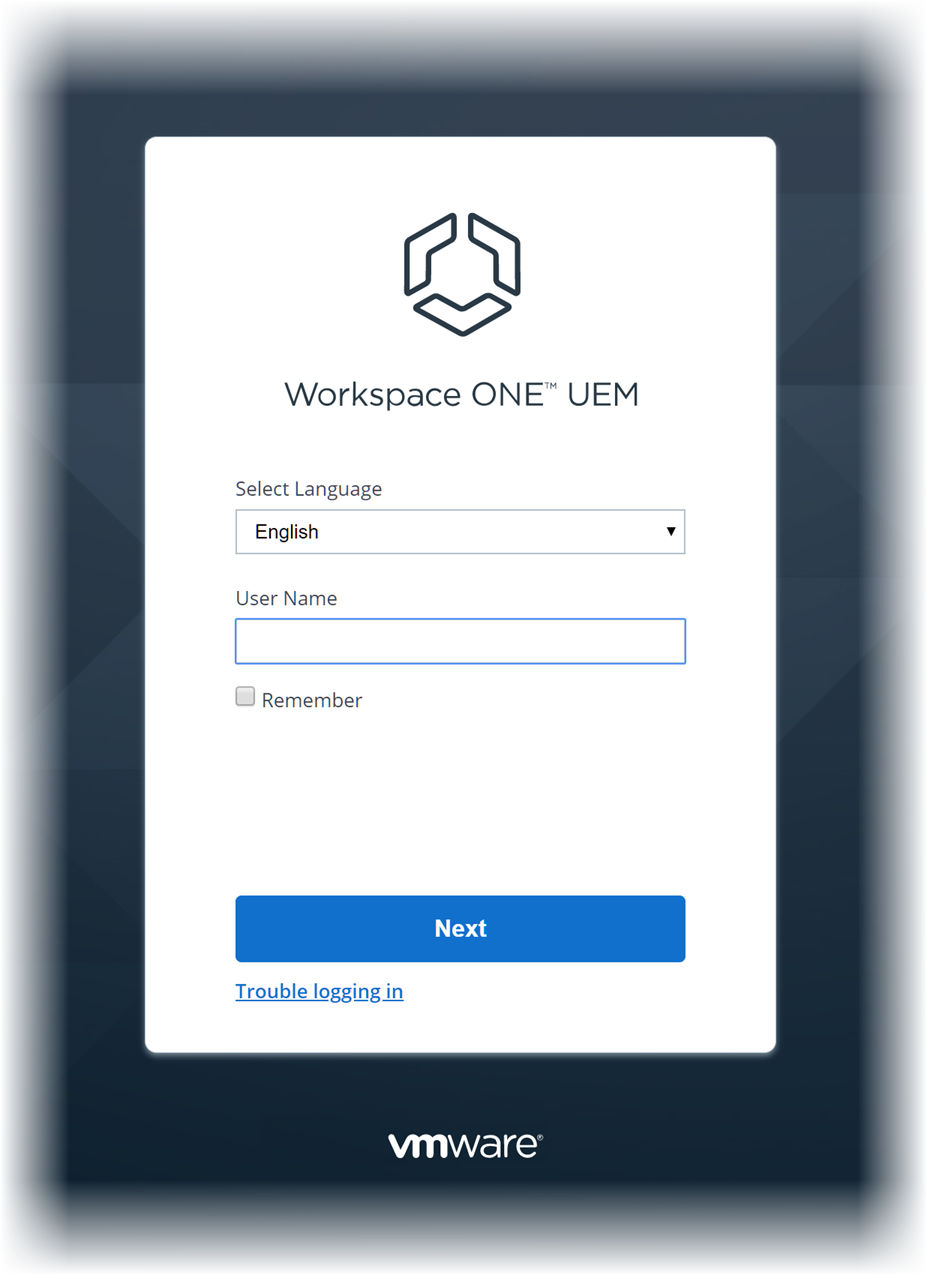
- Enter your User Name.
- The Workspace ONE UEM console saves the user name and the type of user (SAML or non-SAML) in the browser cache.
- If SAML user, admin is directed to SAML login.
- If non-SAML user, admin must enter a password.
- If the Remember check box is enabled, then the User Name text box is pre-populated with the last logged-in user the next time you visit your Environment URL.
- The Workspace ONE UEM console saves the user name and the type of user (SAML or non-SAML) in the browser cache.
- Enter your Password.
- If you are logging in for the first time, you are prompted for the login password. Enter it to proceed.
- If you have logged in before and you are allowing your default browser to remember user names and passwords, then the Password text box auto-completes with the password saved in the browser cache.
- Select the Log In button.
- Your default home screen (which is customizable) opens upon login. Learn how to customize your home screen by visiting Header Menu.
Password Expiration
Basic administrators are notified by email 5 days before their password expires with another email notification the day before. On-premises administrators can change this default 5-day period by navigating to while in the Global organization group. Dedicated SaaS administrators must contact support to make changes to this setting.
You can make a custom password expiration notification for your admins by navigating to and select 'Administrator' as the Category and 'Admin Password Expiry Notification' as the Type.
For information about Enrollment User Password Settings, which are managed separately from Admin Console Passwords, see the system settings page by navigating to .
Session Timeouts and Logouts
- Explicit Logout (including closing the browser and inactivity.)
- If you have configured your default browser to remember your user name and password, then upon the next log in, the browser pre-populates the user name text box with the last user to log in successfully.
- If you have configured your browser to forget user names and passwords, then the user name and type of user (SAML / non-SAML) are wiped from the browser cache.
- Session Invalidation (including load balancer issues and sessions timeouts due to admin setting.)
- Non-SAML users log back in using a saved user name and selecting the Log In button.
- SAML users can log back into the console without any clicks.
Login Lockouts
System Administrators and AirWatch Administrators can configure the Maximum invalid login attempts before admins are locked out of the console by navigating to .
You are locked out from the UEM console in two scenarios: 1) when you make failed login attempts greater than the maximum number of invalid login attempts and 2) when you answer your password recovery question incorrectly three times while trying to reset your password.
When this happens, you must either reset your password using the troubleshooting link on the login page or you must get assistance from an admin to unlock your account using the Admin List View. You receive an email notification when your account is locked and again when it becomes unlocked.
Research Account Lockout Console Events
When Basic Administrator accounts are locked out or unlocked in Workspace ONE UEM, a console event is generated. Both events generate a logging level 5 (warning) event. In addition to reviewing the basic login history directly from Account Settings, you can research Admin account lockouts or unlock console events by taking the following steps.
- Navigate to .
- Select "Warning and above" from the Severity drop-down filter at the top of the Console Event listing.
- Select "Login" from the Category drop-down filter.
- Select "Administration" from the Module drop-down filter.
- Apply more filters as you might require including Date Range.
Manage Account Settings
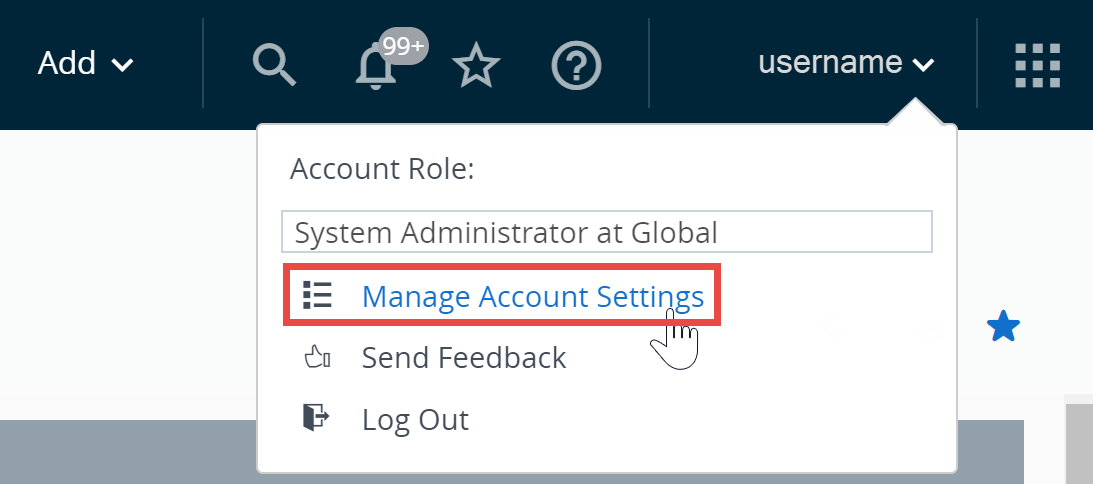
Administrators of Workspace ONE UEM have console specific account settings allowing you to configure user contact information, notification preferences, login history, and security configuration including password recovery.
Manage Account Settings: User
Ensure you can be reached by entering your personal information in the User tab including email, up to four different phone numbers, time zone, and locale.
Manage Account Settings: Notifications
Use the Notifications settings on the Account Settings page to enable or deactivate APNs Expiration alerts, select how to receive alerts, and change the email to which it sends alerts. For more information, see Configure Notifications Settings.
Manage Account Settings: Logins
Review your entire login history including login date and time, the source IP address, login type, source applications, browser make and version, OS platform, and login status.
Manage Account Settings: Security
You can reset your login password, reset the password recovery questions, and reset your four-digit security PIN.
Manage Account Settings: Password
The Password accompanies your account user name when you log into the UEM console. You can Reset this password at any time.
Manage Account Settings: Password Recovery Questions
The Password Recovery Questions are the method by which you reset your password. You must define this question together with its answer when you log in to the UEM console for the first time. You can select a new password recovery question by selecting the Reset button. This action logs out the user automatically. Upon logging back in, they are presented with the Security Settings screen where they are required to select from the list of Password Recovery Questions and supply the answer.
Admins who never selected a password recovery question and do not have a Reset button for Password Recovery Questions must have their accounts deleted and re-created. Upon logging in for the first time after their account is re-created, they are required to define a password recovery question and answer.
You are locked out from the login page when you answer a Password Recovery Question incorrectly more than three times. When this happens, you must reset your password using the troubleshooting link on the login page. Alternatively, you can get assistance from an admin to unlock your account using the Admin List View. You receive an email notification when your account is locked and again when it becomes unlocked.
Manage Account Settings: Security PIN
Establish security for the UEM console by creating a Security PIN. The PIN acts as a safeguard against accidentally wiping a device or deleting important aspects of your environment, such as users and organization groups. The Security PIN also works as a second layer of security. It presents an added point of authentication by blocking actions made by unapproved users.
When you first log in to the UEM console, you are required to establish a Security PIN.
Reset your security PIN every so often to minimize security risks.
Cookie Usage (viewable by VMware Cloud Services administrators only)
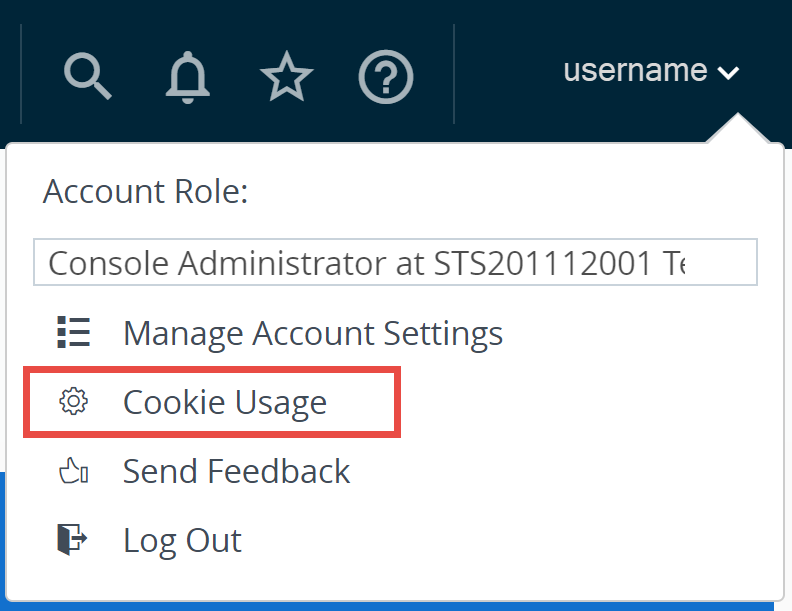
You can participate in the process of improving our services including support, recommendations, and user experience by enabling access to browser cookie-based product guides and analytics. You can opt-out by selecting Cookie Usage and deactivate the sliders for Enable Analytics and Enable Product Guides under the Pendo info card.
Restrict UEM Console Actions
In a scenario when the console for Workspace ONE UEM console is left unlocked and unattended, an extra safeguard is provided against malicious actions that are potentially destructive. You can place those actions out of reach of unauthorized users in such a scenario.
- Navigate to .
- Configure the Send Message to All setting. Enable this setting to allow a system administrator to send a message to all devices in your deployment from the Device List View. It can also be used to send a message to a specific group.
- You can require that certain UEM console actions require admins to enter a PIN. Configure the Password Protect Actions by enabling or disabling the following actions.
Note: Denoted by * below, some actions always require a PIN and as a result cannot be deactivated.
Setting Description Admin Account Delete Prevents the deletion of an admin user account in . *Regenerate VMware Enterprise Systems Connector Certificate Prevents the regeneration of the VMware Enterprise Systems Connector certificate in . *APNs Certificate Change Prevents the disabling of APNs for MDM in . Application Delete/Deactivate/Retire Prevents the deletion, deactivation, or retirement of an application in . Content Delete/Deactivate Prevents the deletion or deactivation of a content file in . *Data Encryption Toggle Prevents the Encryption of user information setting in . Device Delete Prevents the deletion of a device in . Admin security PIN is still required for bulk actions even when this setting is deactivated. *Device Wipe Prevents any attempt to perform a device wipe from the Device List View or Device Details screens. Enterprise Reset Prevents any attempt to perform an enterprise reset on a device from the Devices Details page of a Windows Rugged, Rugged Android, or QNX device. Enterprise Wipe Prevents any attempt to perform an enterprise wipe on a device from the Devices Details page of a device. Enterprise Wipe (Based on User Group Membership Toggle) Prevents any attempt to perform an enterprise wipe on a device when it is removed from a user group. This setting is an optional setting that you can configure under on the Restrictions tab. If you Restrict Enrollment to Configured Groups on this tab, you then have the added option of performing an enterprise wipe a device when it is removed from a group. *Organization Group Delete Prevents any attempt to delete the current organization group from . Profile Delete/Deactivate Prevents any attempt to delete or deactivate a profile from . Provisioning Product Delete Prevents any attempt to delete a provisioning product from . Revoke Certificate Prevents any attempt to revoke a certificate from . *Secure Channel Certificate Clear Protects from any attempt to clear an existing secure channel certificate from . User Account Delete Prevents any attempt to delete a user account from . Change in Privacy Settings Prevents any attempt to alter the privacy settings in . Delete Telecom Plan Prevents the deletion of a telecom plan in . Override Job Log Level Prevents attempts to override the currently selected job log level from . Overriding the Job Log Level is useful when a device or group of devices is having an issue. In this case, the admin can override those device settings by forcing an elevated log level to Verbose, which logs the maximum level of console activity, making it ideal for troubleshooting. *App Scan Vendor Reset/Toggle Prevents the resetting (and subsequent wiping) of your app scan integration settings. This action is performed in . Shut Down Prevents any attempt to shut down the device in . Maximum invalid PIN attempts Defines the maximum number of invalid attempts at entering a PIN before the console locks down. This setting must be between 1 and 5.
Select Password Protect Actions
Restricted Console Actions provide an added layer of protection against malicious actions that are potentially destructive to your Workspace ONE UEM console.
- Configure settings for restricted actions by navigating to .
- For each action you protect by requiring admins to enter a PIN, select the appropriate Password Protect Actions button for Enabled or Deactivated as appropriate.
This requirement provides you with granular control over which actions you want to make more secure.
Note: Some actions always require a PIN and as a result cannot be deactivated. Denoted by * following. - Set the maximum number of failed attempts the system accepts before automatically logging out the session. If you reach the set number of attempts, you must log into the Workspace ONE UEM console and set a new security PIN.
Setting Description Admin Account Delete Prevents the deletion of an admin user account in . Regenerate VMware Enterprise Systems Connector Certificate Prevents the regeneration of the VMware Enterprise Systems Connector certificate in . *APNs Certificate Change Prevents the disabling of APNs for MDM in . Application Delete/Deactivate/Retire Prevents the deletion, deactivation, or retirement of an application in . Content Delete/Deactivate Prevents the deletion or deactivation of a content file in . *Data Encryption Toggle Prevents the Encryption of user information setting in . Device Delete Prevents the deletion of a device in . Admin security PIN is still required for bulk actions even when this setting is deactivated. *Device Wipe Prevents any attempt to perform a device wipe from the Device List View or Device Details screens. Enterprise Reset Prevents any attempt to perform an enterprise reset on a device from the Devices Details page of a Windows Rugged, Rugged Android, or QNX device. >Enterprise Wipe Prevents any attempt to perform an enterprise wipe on a device from the Devices Details page of a device. Enterprise Wipe (Based on User Group Membership Toggle) Prevents any attempt to perform an enterprise wipe on a device when it is removed from a user group. This setting is an optional setting that you can configure under on the Restrictions tab. If you Restrict Enrollment to Configured Groups on this tab, you then have the added option of performing an enterprise wipe a device when it is removed from a group. *Organization Group Delete Prevents any attempt to delete the current organization group from . Profile Delete/Deactivate Prevents any attempt to delete or deactivate a profile from . Provisioning Product Delete Prevents any attempt to delete a provisioning product from . Revoke Certificate Prevents any attempt to revoke a certificate from . *Secure Channel Certificate Clear Protects from any attempt to clear an existing secure channel certificate from . User Account Delete Prevents any attempt to delete a user account from . Change in Privacy Settings Prevents any attempt to alter the privacy settings in . Delete Telecom Plan Prevents the deletion of a telecom plan in . Override Job Log Level Prevents attempts to override the currently selected job log level from . Overriding the Job Log Level is useful when a device or group of devices is having an issue. In this case, the admin can override those device settings by forcing an elevated log level to Verbose, which logs the maximum level of console activity, making it ideal for troubleshooting. *App Scan Vendor Reset/Toggle Prevents the resetting (and subsequent wiping) of your app scan integration settings. This action is performed in . Shut Down Prevents any attempt to shut down the device in . Maximum invalid PIN attempts Defines the maximum number of invalid attempts at entering a PIN before the console locks down. This setting must be between 1 and 5.
Configure Required Notes for Action
You can require administrators to enter notes using the Require Notes check box and explain their reasoning when performing certain Workspace ONE UEM console actions.
- Navigate to .
- If you require that your admins enter a note before taking any of these actions, make sure that you modify the role with the Add Note resource (permission).
For more information, see Create Administrator Role.
Setting Description Lock Device Require a note for any attempt to lock a device from Device List View or Device Details. Lock SSO Require a note for any attempt to lock an SSO session from Device List View or Device Details. Device Wipe Require a note for any attempt to perform a device wipe from Device List View or Device Details. Enterprise Reset Require a note for any attempt to enterprise reset a device from the Device Details page of a Windows Rugged or Rugged Android device. Enterprise Wipe Require a note for any attempt to perform an enterprise wipe from Device Details. Override Job Log Level Require a note before attempts to override the default job log level from . Reboot Device Require a note before a reboot attempt from . Shut Down Require a note before a shut down attempt from .