In some situations, you may need to configure more granular role permissions, beyond the options available through the Tasks tab in the Roles editor. The Advanced tab provides more thorough control over tasks a role can complete.
The following steps should be completed by an experienced Salt administrator who understands your overall infrastructure.
Defining advanced permissions
- Click Administration > Roles on the side menu. Then, select the Advanced tab.
- Ensure the required role is selected in the Roles side panel.
- Select or deselect permissions as needed, choosing from Read, Run, Write, or Delete for a range of functional areas.
See Items for more on available resource types and functional areas.
Minimum recommended permissions for typical user operation are highlighted in blue, as demonstrated in the following figure.
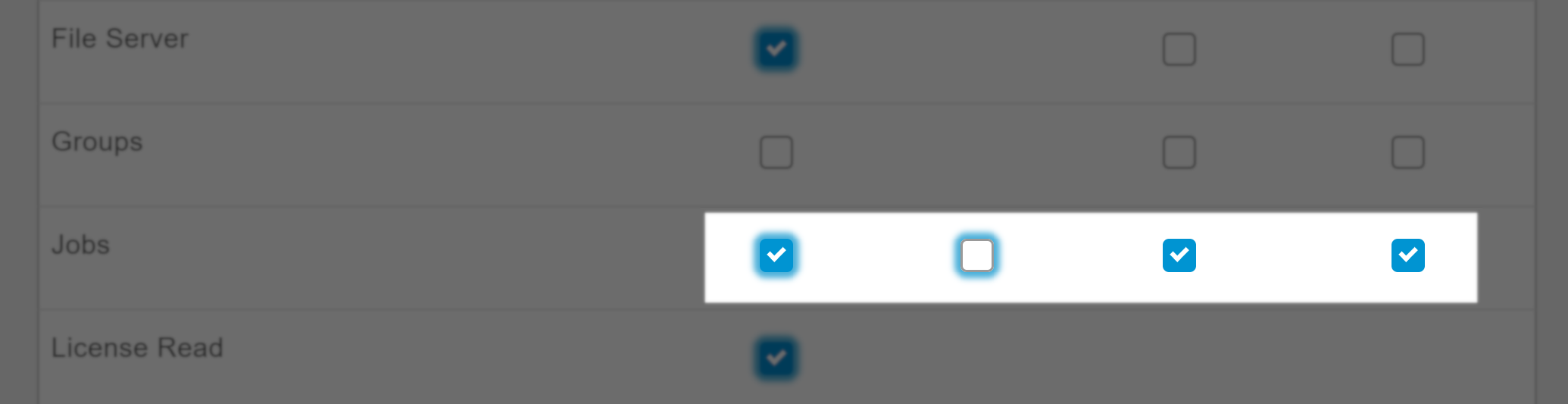
This figure shows two minimum recommended boxes on the left, one selected and the other unselected, compared with two normal boxes on the right.
- Click Save.
Permission types
| Permission |
Description |
|---|---|
| Read |
Role can view a given type of resource or functional area. For example, if you assign the role |
| Run |
Role can run a given type of operation. The type of operation permitted can vary, for instance you can assign permission to run arbitrary commands on minions, or to run commands on Salt controllers. |
| Write |
Role can create and edit a given type of resource or functional area. For example, you might assign |
| Delete |
Role can delete a given type of resource or other item in a given functional area. For example, you might assign |
Items
When setting permissions for a role in the advanced editor, the above actions can apply to the following resources or functional areas.
| Resource type / Functional area |
Description |
See also |
|---|---|---|
| All Minions Commands |
Run commands on the All Minions target. The All Minions target can vary based on the combination of minions the role has permission to access. |
|
| Admin |
Grants administrative privileges in the SaltStack Config user interface only. Be aware that this does not include administrative access to the API (RaaS). As a best practice, use caution when granting this level of access to a role. |
See Built-in roles default settings for a detailed explanation of the Administrative user privileges. |
| Audit Log |
The audit log is a record of all activity in SaltStack Config that includes details of each user’s actions. |
See rpc_audit or contact an administrator for assistance. |
| Commands |
A command is the task (or tasks) executed as part of a job. Each command includes target information, a function, and optional arguments. |
|
| File Server |
The file server is a location for storing both Salt-specific files, such as top files or state files, as well as files that can be distributed to minions, such as system configuration files. |
|
| Groups |
Groups are collections of users who share common characteristics, and need similar user access settings. |
|
| Jobs |
Jobs are used to run remote execution tasks, apply states, and start Salt runners. |
|
| License |
Your license includes usage snapshots, as well as details such as number of Salt controllers and minions licensed for your installation, and when the license expires. |
See rpc_license, or contact an administrator for assistance. |
| Salt Controller Configuration |
The Salt controller configuration file contains details about the Salt controller (formerly called the Salt master), such as its Salt controller ID, publish port, caching behavior, and more. |
|
| Salt Controller Resources |
The Salt controller is a central node used to issue commands to minions. |
|
| Metadata auth |
The AUTH interface is used for managing users, groups, and roles through the RPC API. |
See rpc_auth, or contact an administrator for assistance. |
| Minion Resources |
Minions are nodes running the minion service, which can listen to commands from a Salt controller and perform the requested tasks. |
|
| Pillar |
Pillars are structures of data defined on the Salt controller and passed through to one or more minions, using targets. They allow confidential, targeted data to be securely sent only to the relevant minion. |
|
| Returner Data |
Returners receive the data minions return from executed jobs. They allow for the results of a Salt command to be sent to a given data store such as a database or log file for archival. |
|
| Roles |
Roles are used to define permissions for multiple users who share a common set of needs. |
|
| Runner Commands |
A command is the task (or tasks) executed as part of a job. Each command includes target information, a function, and optional arguments. Salt runners are modules used to execute convenience functions on the Salt controller. |
|
| Compliance Assessment |
An assessment is an instance of checking a collection of nodes for a given set of security checks, as specified in a SaltStack SecOps Compliance policy. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Compliance Policy |
Compliance policies are collections of security checks, and specifications for which nodes each check applies to, in SaltStack SecOps Compliance. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Compliance Remediation |
Remediation is the act of correcting noncompliant nodes in SaltStack SecOps Compliance. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Compliance Content Ingest - SaltStack |
Ingesting SaltStack SecOps Compliance content is to download or update the SaltStack SecOps Compliance security library. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Compliance Content Ingest - Custom |
Custom Compliance content allows you to define your own security standards, to supplement the library of security benchmarks and checks built into SaltStack SecOps Compliance. Ingesting custom content is to upload custom checks and benchmarks. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Compliance Custom Content |
Custom Compliance content allows you to define your own security standards, to supplement the library of security benchmarks and checks built into SaltStack SecOps Compliance. |
SaltStack SecOps Compliance - Note: A SaltStack SecOps license is required. |
| Schedules |
Schedules are used to run jobs at a predefined time or specific interval. |
|
| SSH Commands |
Secure Shell (SSH) commands run on minions that do not have the minion service installed. |
|
| Target Groups |
A target is the group of minions, across one or many Salt controllers, that a job’s Salt command applies to. A Salt controller can also be managed like a minion and can be a target if it is running the minion service. |
|
| Users |
Users are individuals who have a SaltStack Config account with your organization. |
|
| Vulnerability Assessment |
A vulnerability assessment is an instance of scanning a collection of nodes for vulnerabilities as part of a SaltStack SecOps Vulnerability policy. |
SaltStack SecOps Vulnerability - Note: A SaltStack SecOps license is required. |
| Vulnerability Policy |
A vulnerability policy is comprised of a target and an assessment schedule. The target determines which minions to include in an assessment and the schedule determines when assessments will be run. A security policy also stores the results of the most recent assessment in SaltStack SecOps Vulnerability. |
SaltStack SecOps Vulnerability - Note: A SaltStack SecOps license is required. |
| Vulnerability Remediation |
Remediation is the act of patching vulnerabilities in SaltStack SecOps Vulnerability. |
SaltStack SecOps Vulnerability - Note: A SaltStack SecOps license is required. |
| Vulnerability Content Ingest |
SaltStack SecOps Vulnerability content is a library of advisories based on the latest Common Vulnerabilities and Exposures (CVE) entries. Ingesting SaltStack SecOps Vulnerability content is to download the latest version of the content library. |
SaltStack SecOps Vulnerability - Note: A SaltStack SecOps license is required. |
| Vulnerability Vendor Import |
SaltStack SecOps Vulnerability supports importing security scans generated by a variety of third-party vendors. This permission allows a user to import vulnerability scan results from a file, or through a connector. By default, all SaltStack Config users can access the Connectors workspace. However, permission to run Vulnerability Vendor Import, as well as a SaltStack SecOps Vulnerability license, are required for a user to successfully import vulnerabilities from a connector. |
Connectors, SaltStack SecOps Vulnerability - Note: A SaltStack SecOps license is required. |
| Wheel Commands |
Wheel commands control how the Salt controller operates, and are used to manage keys. |
Resource access in the API
Access to the following resource types must be defined using the API (RaaS):
- Files in the file server
- Pillar data
- Authentication configuration
All other resource types, (excluding jobs, targets, and those listed above) do not require any specific resource access settings.