As an alternative to running an assessment on a vulnerability policy, SaltStack SecOps Vulnerability supports importing security scans generated by a variety of third-party vendors.
Instead of running an assessment on a vulnerability policy, you can import a third-party security scan directly into SaltStack Config and remediate the security advisories it identified using SaltStack SecOps Vulnerability. See How do I run a vulnerability assessment for more information about running a standard assessment.
- Tenable
- Rapid7
- Qualys
- Kenna Security
- Carbon Black
You can import a third-party from a file, from a connector, or by using the command line.
Prerequisites
Before you can import a third-party security scan you must configure a connector. The connector must first be configured using the third-party tool's API keys.
To configure a Tenable.io connector:
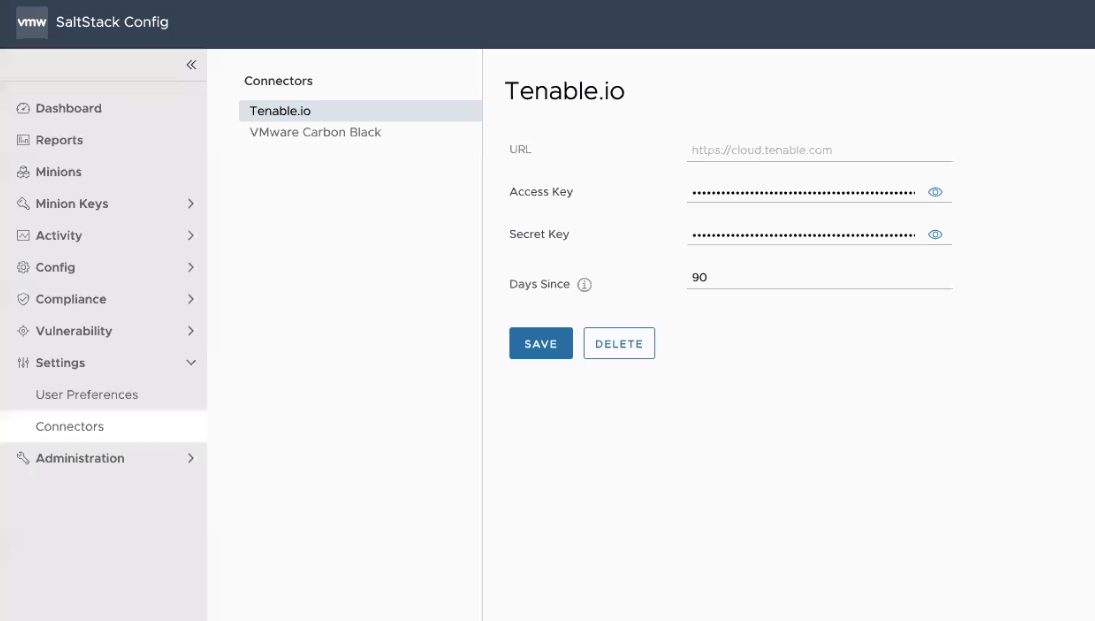
| Connector field | Description |
|---|---|
| Secret Key and Access Key | Key pair required to authenticate with the connector API. For more information on generating your keys, see the Tenable.io documentation. |
| URL | Base URL for API requests. This defaults to https://cloud.tenable.com. |
| Days since | Query Tenable.io scan history beginning this number of days ago. Leave blank to query an unlimited period of time. When you use a connector to import scan results, SaltStack SecOps Vulnerability uses the most recent results per node available within this period.
Note: To ensure your policy contains the latest scan data, make sure to rerun your import after each scan.
SaltStack SecOps Vulnerability does not poll Tenable.io for the latest scan data automatically.
|
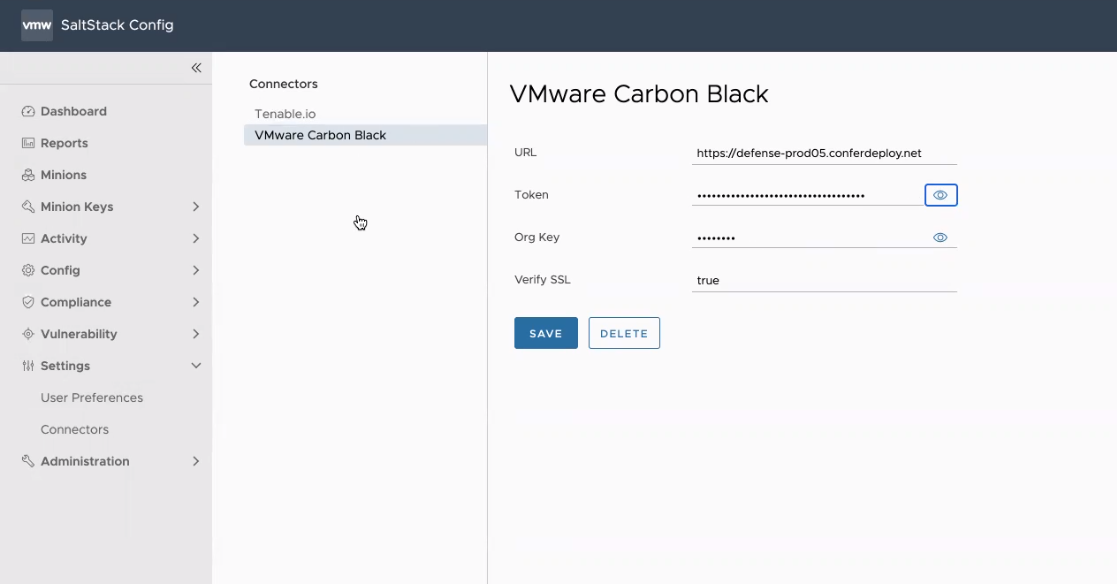
To configure a Carbon Black connector (Windows only):
Before you can configure a Carbon Black connector, you must first set up a Windows Minion Carbon Black sensor kit environment.
- Launch a Saltstack Config environment and deploy a Windows server.
- Install the Salt minion on the Windows server. For more information see, Salt Minion Installation.
- Accept the master keys in SaltStack Config, and the minion keys from SaltStack Config or the Salt Master.
- Install the Carbon Black sensor kit on the Windows minion. For more information, see Installing Sensors on VM Workloads.
- In SaltStack SecOps, define a policy with a target group that contains the Windows minion.
- After the SaltStack Config VMan ingestion is complete, sync the SaltStack Config Carbon Black module from the Salt master by running these commands:
salt mywindowsminion saltutil.sync_modules saltenv=sse. - On the Windows minion, set the Carbon Black device grain by running the
salt mywindowsminion carbonblack.set_device_grain.
| Connector Field | Description |
|---|---|
| URL | URL for API requests |
| Token and Org Key | Key pair required to authenticate with the connector API.
Note: If you a delete a VMware Carbon Black connector, these fields are populated with 'xxxx' characters. This is to maintain the token key format of 'xxxxxxxxxxxxxxxxxxxxxxxx/xxxxxxx'
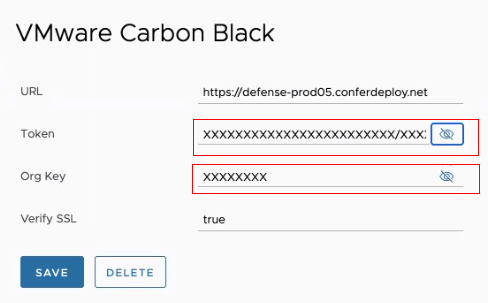
|
| Verify SSL | Default is set to true. |
- Click Minions and select either All Minions or a specific minion for a policy target group.
- Click Run Command and run these commands:
saltutil.sync_all,carbon_black.set_device_grain, andsaltutil.refresh_grains.
Procedure
Results
What to do next
You can now remediate these advisories. See How do I remediate my advisories for more information.