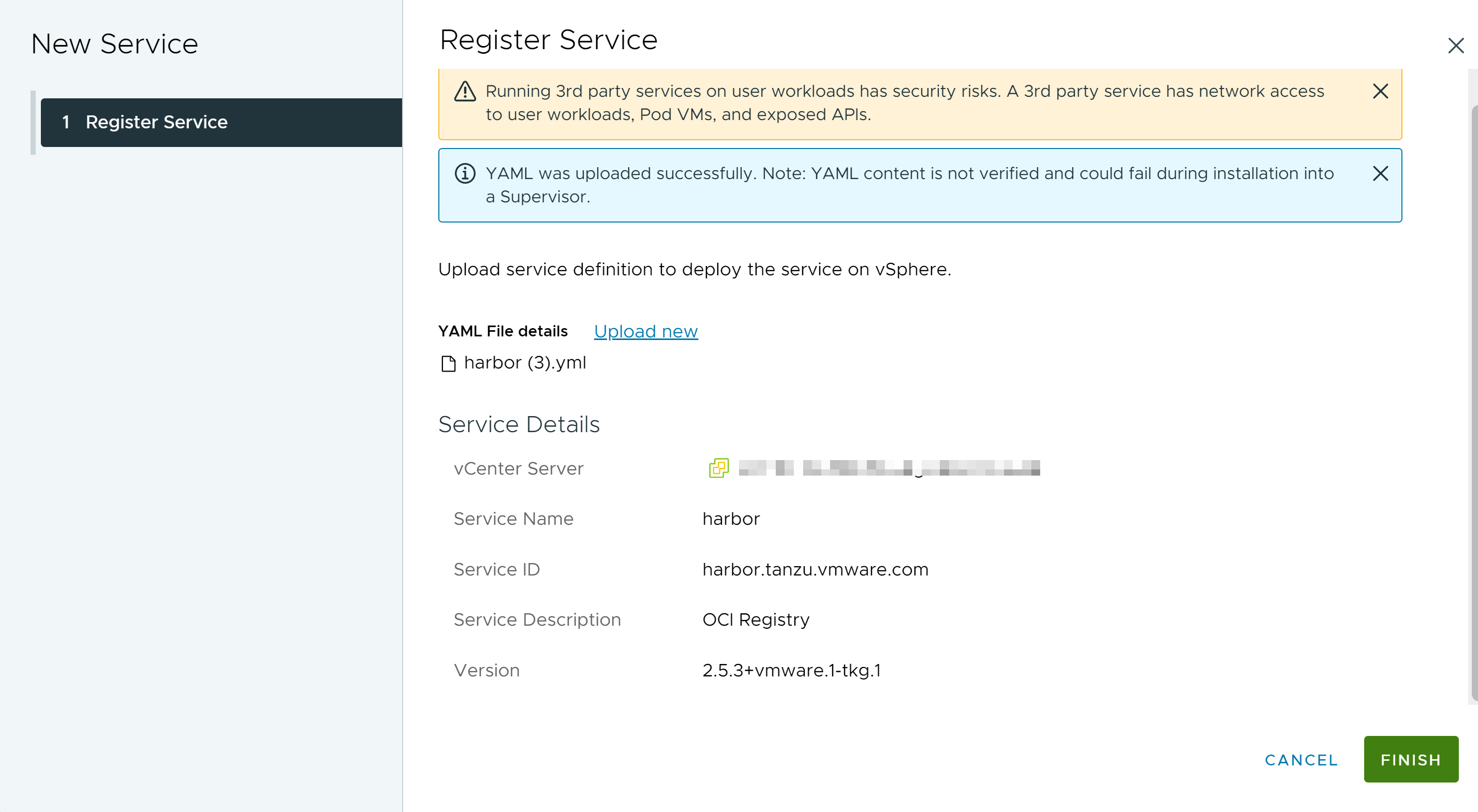
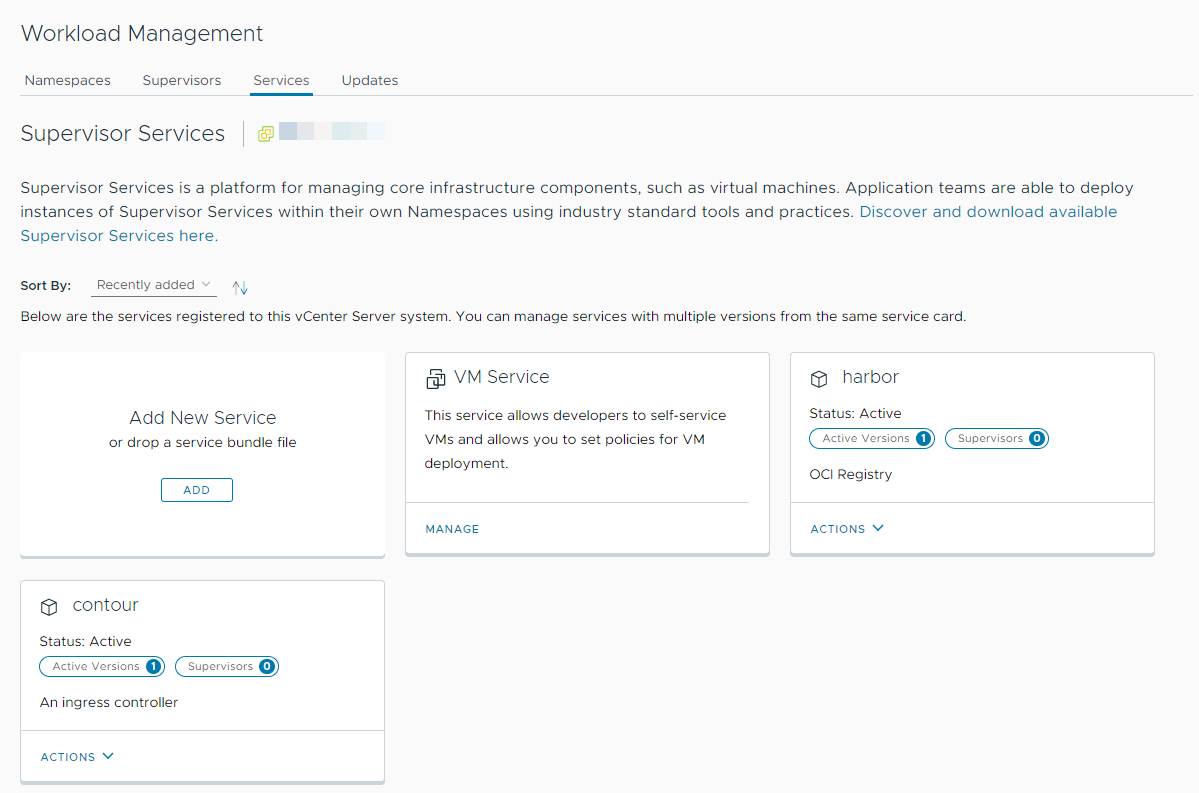
Checkout how to install and configure Harbor as a Supervisor Service. You can then use Harbor as a registry for workloads running on TKG clusters and vSphere Pods. Harbor requires Contour as ingress controller, therefore you first install the Contour Supervisor Service then you install Harbor.
Install Harbor as a Supervisor Service
You install Harbor as a Supervisor Service trough the Workload Managementt option in the vSphere Client.
Prerequisites
- Verify that you have upgraded to vCenter Server 8.0a or higher. Contour and Harbor Supervisor Services are supported with vCenter Server 8.0a and higher.
- Verify that you have the Manage Supervisor Services privilege on the vCenter Server system where you add the services.
- Install Contour as a Supervisor Service on the same Supervisor where you want to install Harbor. See Install Contour as a Supervisor Service in vSphere IaaS Control Plane.
- Designate and FQDN for accessing the Harbor admin UI.
Procedure
Results
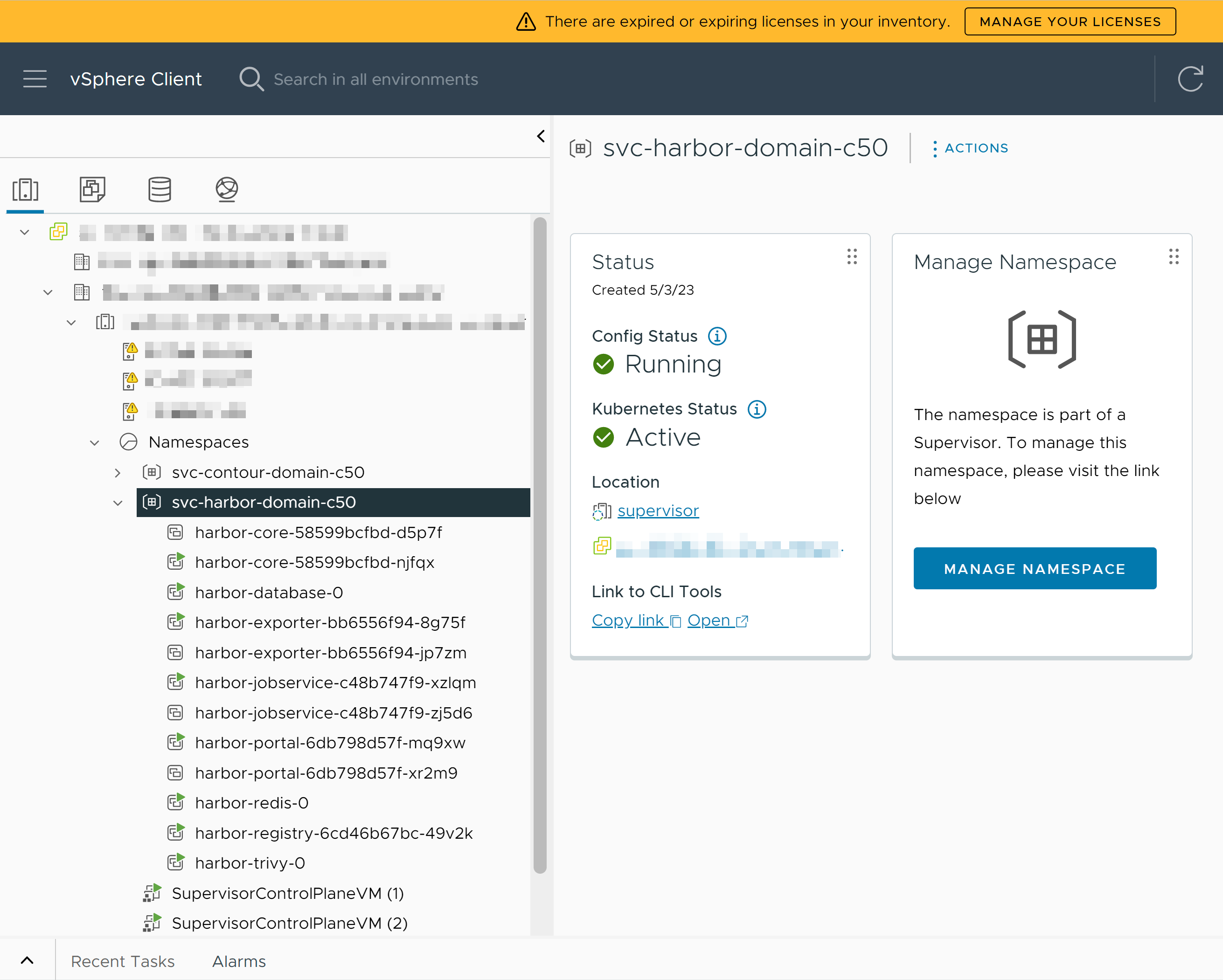
Map the Harbor FQDN to the Envoy Ingress IP Address
After Harbor is installed successfully, include a record of the Harbor FQDN mapping to the Envoy ingress IP address in an external DNS server that is configured with the Supervisor.
TKG clusters, vSphere Pods, and the Supervisor must be able to resolve the Harbor FQDN to be able to pull images from the registry.

Establishing Trust with the Harbor Supervisor Service
Once Harbor is installed, you must configure trust between the Supervisor and Harbor to use it as registry for vSphere Pods. TKG clusters that are on the same Supervisor as Harbor have trust established with Harbor automatically. To use Harbor as a registry for TKG clusters that run on different Supervisors, you must configure trust between Harbor and these TKG clusters.
Establish Trust Between Harbor and Supervisor
- Extract the Harbor CA from the Harbor UI or by using the TLS secret on the Supervisor control plane. You can get the Harbor ca.cert in the Harbor admin UI at .
- Add the Harbor CA to the image-fetcher-ca-bundle ConfigMap in the kube-system namespace. You must be logged in with a vCenter Single Sign-on administrative account and have permission to edit the image-fetcher-ca-bundle.
- Configure the KUBE_EDITOR environment variable as described here:
- Edit the ConfigMap using the following command:
kubectl edit configmap image-fetcher-ca-bundle -n kube-system
- Append the contents of the Harbor ca.cert file to the ConfigMap beneath the existing Supervisor certificate. Make sure not to change the Supervisor certificate.
apiVersion: v1 data: ca-bundle: |- -----BEGIN CERTIFICATE----- MIIC/jCCAeagAwIBAgIBADANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwprdWJl ... qB72tWi8M5++h2RGcVash0P1CUZOHkpHxGdUGYv1Z97Wl89dT2OTn3iXqn8d1JAK aF8= -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDKDCCAhCgAwIBAgIQBbUsj7mqXXC5XRhqqU3GiDANBgkqhkiG9w0BAQsFADAU ... 5q7y87vOLTr7+0MG4O01zK0dJYx2jVhZlsuduMYpfqRLLewVl0eGu/6vr2M= -----END CERTIFICATE----- kind: ConfigMap metadata: creationTimestamp: "2023-03-15T14:28:34Z" name: image-fetcher-ca-bundle namespace: kube-system resourceVersion: "713" uid: 6b7611a0-25fa-40f7-b4f5-e2a13bd0afe3 - Save the edits made to the file. As a result kubectl reports:
configmap/image-fetcher-ca-bundle edited
Establishing Trust Between Harbor and TKG Cluster Running on Different Supervisors than Harbor
TKG clusters running on Supervisors different than the one where Harbor is installed must have network connectivity with Harbor. These TKG clusters must be able to resolve the Harbor FQDN.
To establish trust between Harbor and the TKG clusters, extract the Harbor CA from the Harbor UI or by using the TLS secret on the Supervisor control plane, then follow the steps listed at Integrate a TKG 2 Cluster with a Private Container Registry.