As announced on August 4, 2023, VMware Aria Automation for Secure Clouds is transitioning to the VMware Tanzu Guardrails brand and product line. You can review this page for status updates on the transition and announcements for the latest Tanzu Guardrails features.
November 2, 2023 - What's New
VMware Aria Automation for Secure Clouds
As previously announced, VMware Aria Automation for Secure Clouds has become part of VMware Tanzu Guardrails (formerly Aria Guardrails). Existing customers can continue to use VMware Aria Automation for Secure Clouds and receive Customer Success support until the end of their existing subscription term. Existing customers also now have access to VMware Tanzu Guardrails and new feature updates will happen in Tanzu Guardrails. For any further inquiries, please contact your Customer Success Manager.
-
Remediation Worker Group Image Upgrade – Action Required
We made changes to our remediation worker image due to a recent security update. If you are currently using a remediation worker, please follow the steps below to pull the latest image version and restart the worker by November 30th, 2023.
-
Stop the existing worker and delete the older worker image from the registry by running the following command:
docker rmi vmware/vss-remediation-workerIf the image is being used by any running container, stop and delete the container using the following command:
docker stop <container_id> docker rm <container_id> -
Run the following command to pull the latest image:
docker pull vmware/vss-remediation-worker:latestThe following steps are only required if you need to reference the worker startup script or secret. If you have this information, you can restart the worker using the previous startup script.
-
Go to Settings > Remediation Worker Group and select the worker group and view the “Properties” tab to re-deploy the worker. Click on the “regenerate key” button to get the latest key and save it for later use.
-
Copy the startup script and replace the VSS_CLIENT_SECRET value with the key retrieved in the previous step.
-
When Step 4 is completed, start the worker using the script.
If you have any questions or need further support, reach out to your Customer Success Manager.
-
-
Microsoft Entra ID ("Azure AD") Support - Public Beta
VMware Aria Automation for Secure Clouds is introducing support for Microsoft Entra ID (formerly known as “Azure AD”) to provide you with visibility into your Entra ID resources and manage risks and misconfigurations with new rules aligning to the Azure v2.0 CIS benchmark. After onboarding your Microsoft Entra ID tenant to our platform, you will be able to view Users, Groups, Principals, and Service Principals in our Explore inventory. You can view the newly supported Azure IAM policies under the “Azure AD” tab in Governance > Rules and any detected misconfigurations in Findings.
Here are the new policies we support for managing Azure IAM as part of this release:
-
Azure ActiveDirectory user should have MFA enabled (RuleId-ae98266b-658b-4b35-a921-ef217451e4e7) - High
-
Azure AD Conditional Access policy should include an exclusionary geographic access policy (RuleId-12520f19-8e08-4965-a4d6-6d68c7ead51c) - High
-
Azure AD tenant should have authorization policy that enforces strict guest permission restrictions (RuleId-04782266-d857-4767-8b94-a8a828376bc3) - High
-
Azure AD tenant should have authorization policy that limits the permission to invite guest users (RuleId-68d992e8-6ece-4a64-b53e-bcc1fca7997b) - High
-
Azure AD tenant should have conditional access policy requiring MFA for all risky sign-ins (RuleId-55015749-1301-41ef-99ae-03592798e208) - High
-
Azure AD tenant should have Security defaults enabled (RuleId-a78813dd-ab5a-452b-b532-d69878cb6d1e) - High
-
Azure AD Conditional Access policy should list Trusted Locations (RuleId-469196f2-c61b-46d9-9673-e27641be679c) - Medium
-
Azure AD tenant should have conditional access policy requiring MFA (RuleId-260a4845-9b28-481d-8f50-03f93b908a13) - Medium
For more information on how to onboard your Microsoft Entra ID tenant, refer to our product documentation.
-
VMware Tanzu Hub
As part of the move to VMware Tanzu Hub, the following VMware Automation for Secure Clouds features are now available in VMware Tanzu Hub as well.
-
Extensive Findings Details - Now Available in VMware Tanzu Hub
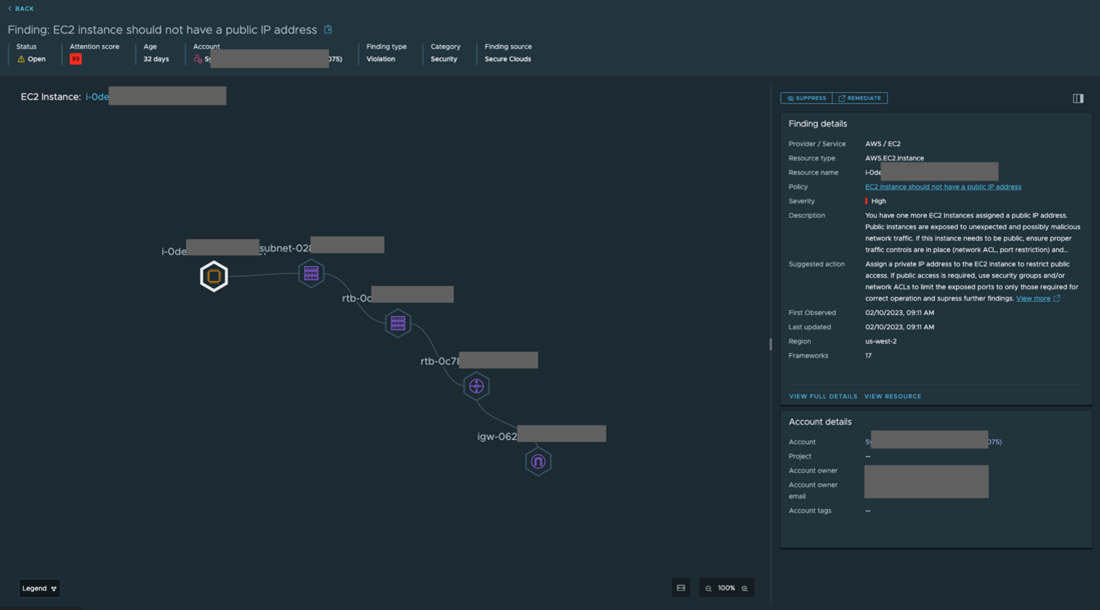
Now VMware Tanzu Guardrails provides extensive findings details by providing a dedicated details page for each finding. The finding information and available finding actions on each detail page are specific to each finding depending on its nature. In this way, you can easily understand the finding and its context, and then decide whether to share it, suppress it, or remediate it.
Along with the complete finding details at your fingertips you can also explore resource and the cloud account details on which the finding was detected. A finding graph view is provided for some types of findings and can provide additional insight into related resources and how their configurations relate to the detection of the respective finding.
-
New Ways to Explore and Prioritize Findings - Now Available in VMware Tanzu Hub
VMware Tanzu Guardrails now provides two new ways to explore, prioritize, investigate, and ultimately remediate your findings with two new Finding views available on the Findings page:
-
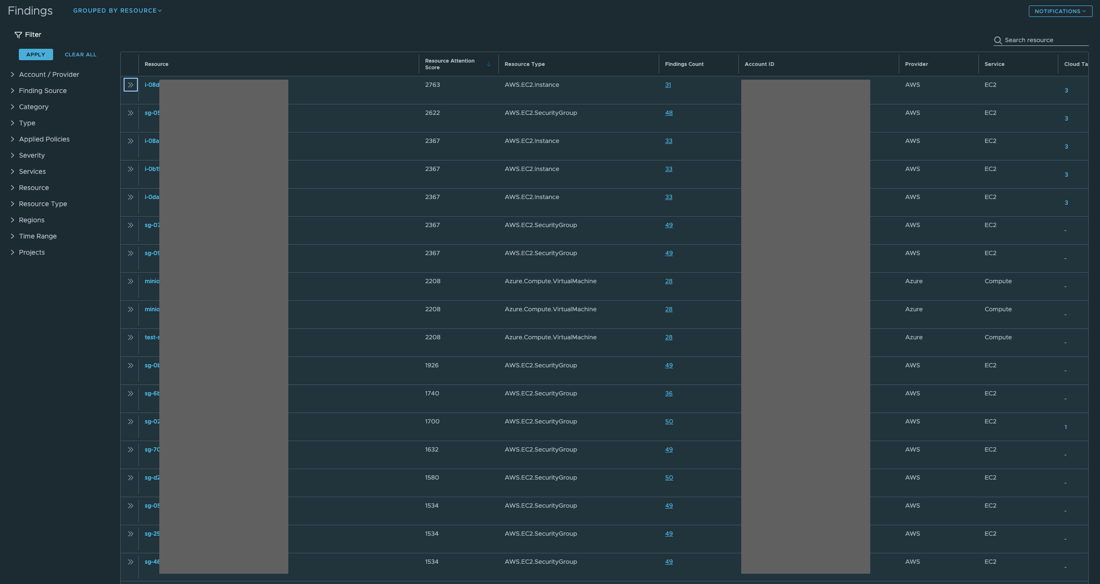
Findings grouped by resource - is an aggregate view on the findings detected for each resource with the ability to sort by resource attention score* (applied by default), findings count, age of latest detected finding, and more.
-
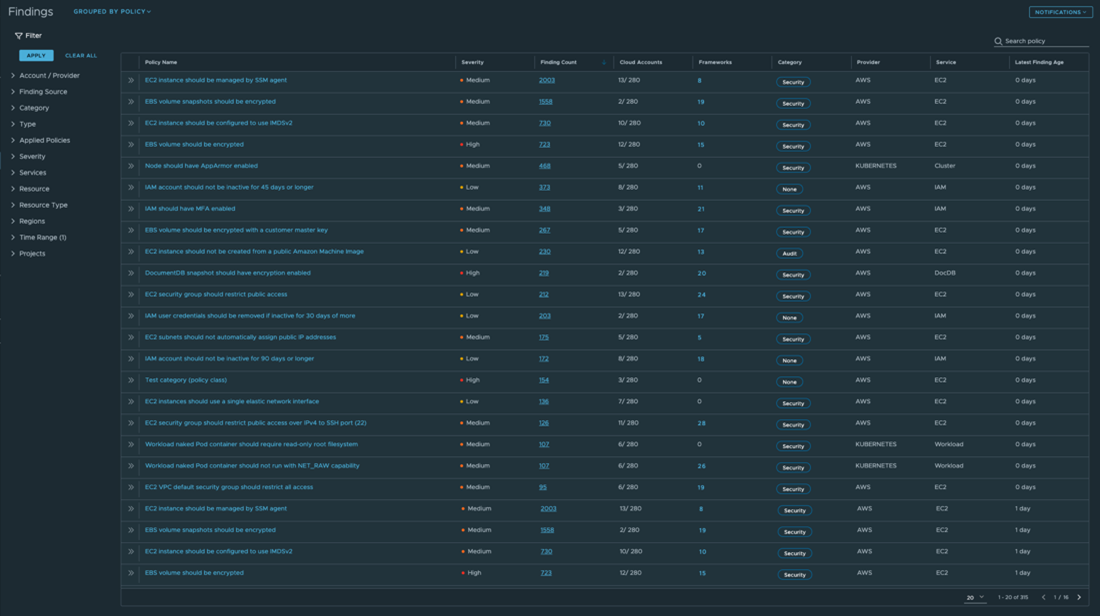
Findings grouped by policy - is an aggregate view on the findings detected for each policy or desired state with the ability to sort by finding count (applied by default), policy name, age of latest detected finding, and more.
Combining these new finding views with the many already available filtering options can make your finding prioritization easy and help you focus on the areas that need the most attention regarding your infrastructure security and compliance posture.
*resource attention score - is the sum of the findings attention score detected for the respective resource, for the findings that are matching the applied filters (if any).
-
-
Email Notifications Available for Findings - Now Available in VMware Tanzu Hub
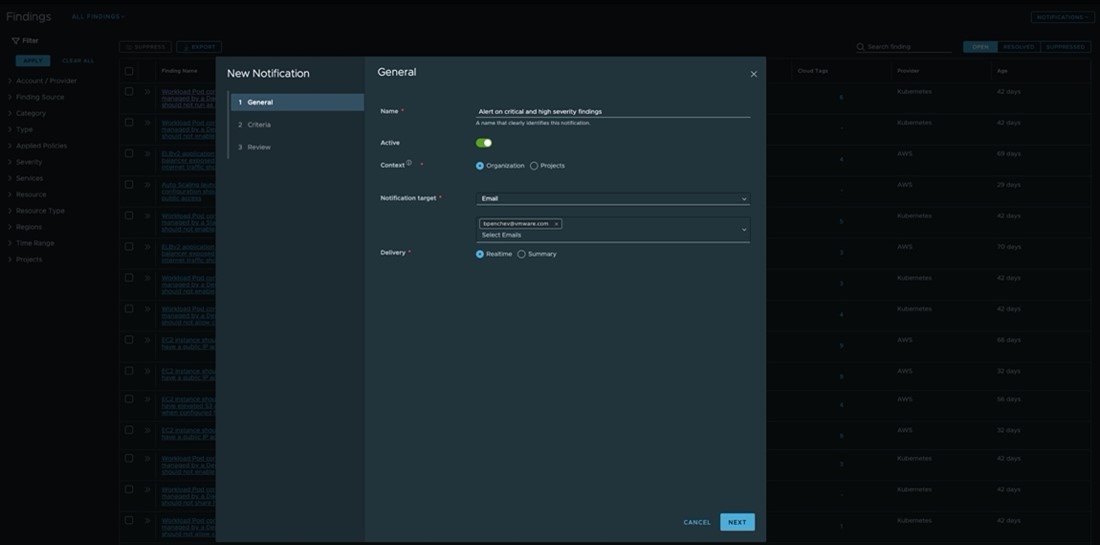
We're pleased to announce that you can now create Email Notifications that can alert you about new findings that VMware Tanzu Guardrails detects. All you need to do is just list the recipients, decide on triggering criteria and the type of the notification – realtime or summary:
-
Realtime (selected by default) - sends an email almost immediately for each newly detected finding after it is detected.
-
Summary - sends an email periodically on the newly detected findings, summarized either by Resource or by Policy. You can choose the frequency to receive the email: either hourly, daily, or a custom period. If findings do not occur that match your criteria, an email does not get sent.
The notification email content provides basic findings details in the case of realtime notifications, or a summary table on the number of new findings that were detected since the last email update for summary notifications. Email messages also contain links to the respective findings in both Tanzu Guardrails and Aria Automation for Secure Clouds - depending on which one of the two you are currently using, you can further investigate the newly detected findings in it or even in both.
-
-
Export Findings to a CSV File - Now Available in VMware Tanzu Hub
You can now export findings results from the "ALL FINDINGS" view to a CSV file with a single click. Any filters that are applied to the findings also apply to the findings data that is exported to the CSV file.
To export your findings, go to the Findings page, make sure that you are viewing ALL FINDINGS, apply any filters that you choose, and click the EXPORT button that is located above the Findings grid.
-
GCP Security Command Center Findings Source – Now Available in VMware Tanzu Hub
GCP Security Command Center is now available as a findings source in VMware Tanzu Hub.
Findings sources make it easier to correlate information between cloud resource configurations, posture misconfigurations, threats, and vulnerabilities. When configured, a findings source enables ingestion of security findings from external sources such as Amazon GuardDuty, Amazon Inspector, and Azure Defender.
Threat and vulnerability findings from the GCP Security Command Center can now be ingested and correlated, providing an additional layer of security insights and enabling security and operational teams to match cloud configurations to host vulnerabilities from one GUI or report.
You can configure GCP Security Command Center in a few short steps. You can choose which accounts to ingest findings into VMware Tanzu Hub under Set Up and Configure> Findings Sources> GCP Security Command Center. To view the findings along with other VMware Tanzu Guardrails findings, navigate to the various Findings views and choose GCP Security Command Center in the findings sources filter.
VMware Tanzu Guardrails
The following features have been released for VMware Tanzu Guardrails and are available through VMware Tanzu Hub.
-
Virtual Machine Rightsizing Recommendation from Cloud Native Sources
VMware Tanzu Guardrails can now be configured to fetch the Amazon EC2 rightsizing recommendations from AWS Cost Explorer in the AWS accounts. The AWS accounts should have recommendation enabled in the Cost Explorer. Also, Azure Virtual Machine rightsizing recommendations can be fetched into Tanzu Guardrails from Azure Advisor in the Azure subscriptions.
-
Discover and Govern Unmanaged Cloud Virtual Machines
VMware Tanzu Guardrails now offers Desired State templates to discover unmanaged cloud virtual machines (VMs) (AWS & Azure), automatically install VMware Aria Automation for Secure Hosts minion on the VM and register them to VMware Aria Automation for Secure Hosts. VMware Aria Automation for Secure Hosts can be used to perform Operating System compliance check and vulnerability management for the VMs. It reduces the security blind spots.
-
Version Control Desired State Templates and GIT Integration
Users can now manage Desired State template version in the GIT repository managed by them. The integration allows users to create Desired States by referring to the template path and the commit version in the Desired State configuration.
October 3, 2023 - What's New
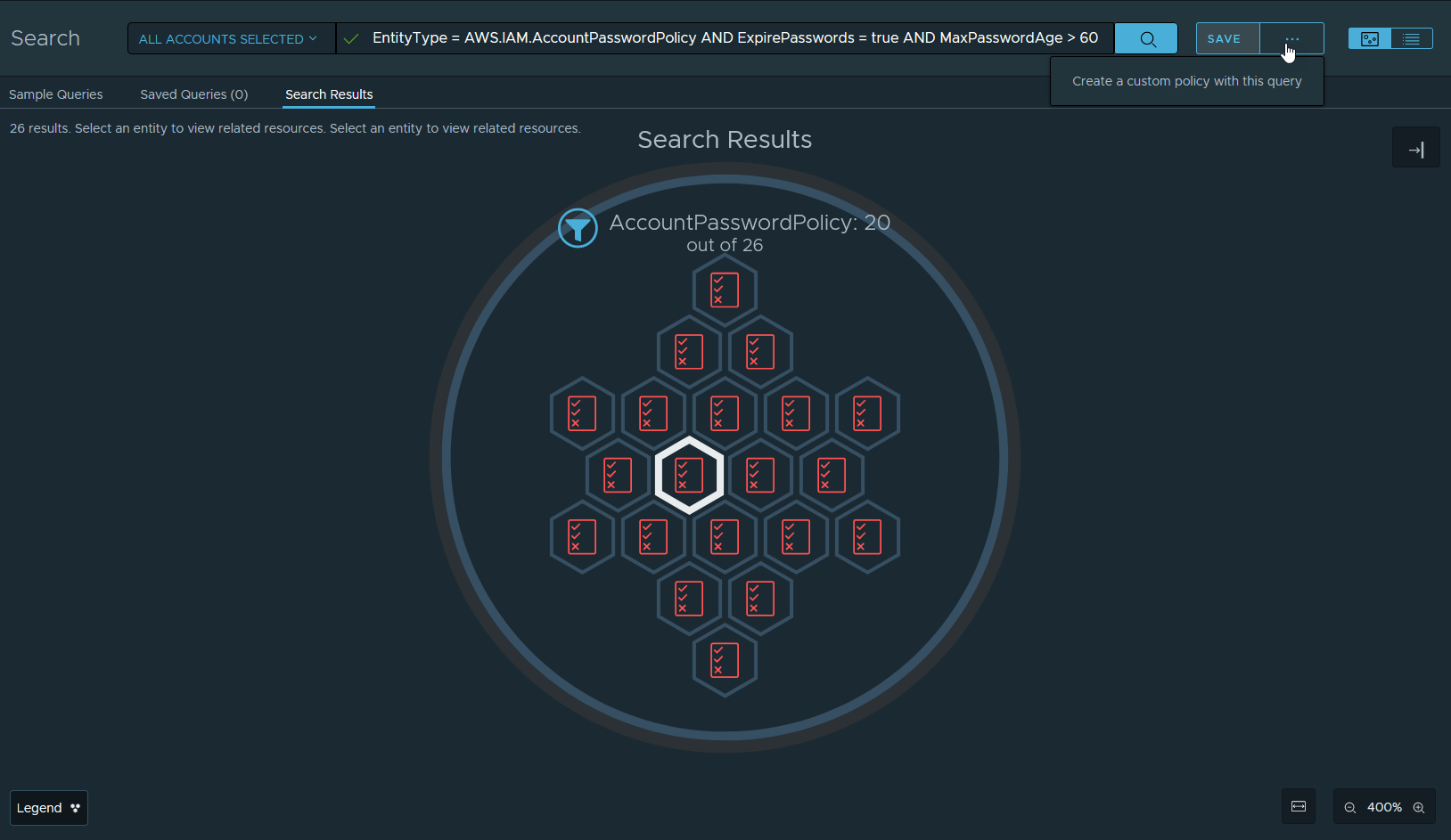
Create Custom Posture Policies with Explore Search in VMware Tanzu Hub
We are excited to announce that another VMware Aria Automation for Secure Clouds feature is available in VMware Tanzu Hub! You can now easily create a custom posture policy by saving your Explore Search SSQL query in Tanzu Hub. Using Explore Search to create new custom policies allows you to create and validate SSQL search queries to explore your cloud inventory before saving the query as a policy. For more information on creating custom posture policies, refer to the product documentation.
This update is part of the VMware Aria Automation for Secure Clouds move to the VMware Tanzu Hub platform. Stay tuned for more updates as we continue to migrate additional features over to Tanzu Hub.
July 31, 2023 - What's New
- New functionality to scale governance across cloud accounts – Now Available
- Support for Amazon DocumentDB and FSx Inventory and Rules – Now Available
New functionality to scale governance across cloud accounts – Now Available
We are excited to provide you access to new features as part of your VMware Aria Automation for Secure Clouds subscription. These features are available through access to the VMware Aria Hub > Governance tab.
To access VMware Aria Hub, login to https://console.cloud.vmware.com/and click on “Launch Service” from the VMware Aria Hub card on the page. Make sure you have access to “VMware Aria Hub”,” "VMware Aria Guardrails”, and "VMware Aria Automation for Secure Cloud”. You can check your access by checking the service roles in My Account Roles - VMware Cloud Services.
With access to these additional capabilities, you can:
-
Establish Landing Zones by creating new AWS and Azure accounts with pre-defined policies. Provision compliant accounts using Infrastructure as Code (Iac) templates which allows to set policies and enable governance tools proactively. Learn more.
-
Monitor drift from the desired state declared using IaC templates during provisioning and enforce policies: You can choose to monitor drift from the desired policy configurations or remediate drift continuously by leveraging event-driven detection and automated remediation.
-
Centralized visibility of policy violations and drift across multiple cloud accounts and policy engines: For users who are monitoring drift from the desired policy configurations in their accounts declared using policy templates, the drift alerts, and findings available in Aria Automation for Secure Clouds are now in a single dashboard. Learn more.
-
Policy management using templates: Out of the box policy templates that can be used to configure pre-defined policy configurations for your cloud accounts include bootstrap, security, network, cost, performance, and config. You can also customize templates as per the organization’s unique needs. Learn more.
For more details, refer to the product documentation.
Support for Amazon DocumentDB and FSx Inventory and Rules – Now Available
We are excited to announce support for two Amazon services, DocumentDB and FSx. You can now view DocumentDB and FSx resources in your inventory and manage any potential risks and misconfigurations for these resources using the newly published ruleset.
New DocumentDB Ruleset:
-
DocumentDB cluster should be encrypted using customer managed key (RuleId: 71a34b4b-984c-4a86-810c-57016e36bebc) - High
-
DocumentDB cluster should have encryption enabled (RuleId: 11390bea-0b54-4997-9831-96c3da024923) – High
-
DocumentDB snapshot should have encryption enabled (RuleId: ad20b451-d780-4cd8-a5d3-361529c463ac) – High
-
DocumentDB cluster backup retention period should be greater than or equal to 30 days (RuleId: 1d336634-43c4-43bd-8b91-282d6a4c142e) - Low
-
DocumentDB cluster should not have deletion protection disabled (RuleId: 89f1e1b0-bb33-42ff-8ecf-68146c13d8cd) - Low
-
DocumentDB cluster should not use a database engine default port (RuleId: f5f42879-f5f6-4658-b457-d2d0c25550fb) - Low
-
DocumentDB event notifications subscription should be configured for critical cluster events (RuleId: beb0af93-7836-4efc-843a-183c41d570cd) - Low
-
DocumentDB event notifications subscription should be configured for critical database instance events (RuleId: ee5f739e-a663-49b8-b962-125d42cb0922) - Low
-
DocumentDB event notifications subscription should be configured for critical database parameter group events (RuleId: 39b494cd-bb7c-4f4d-89dd-2e1c96f5cb73) - Low
-
DocumentDB event notifications subscription should be configured for critical database security group events (RuleId: 61293976-e499-4c15-90cb-58d9d939fd74) – Low
New FSx Ruleset:
-
FSx file system should be encrypted with a customer managed key (RuleId: 5082c609-e763-4ae3-86fd-26f98feee05b) - Medium
-
FSx file system should have automatic backups enabled (RuleId: b02d28a2-894e-4ce0-9259-1f681ca95363) - Medium
-
FSx for Lustre file system should have logging enabled (RuleID: 6e1ed4f4-85a1-44dd-aaa0-b581c9225820) - Low
-
FSx for Windows File Server file system should have audit logging enabled (RuleId: d0e431ea-7c5b-4892-9d00-7405bbec1017) - Low
June 16, 2023 - What's New
Support for FedRAMP Compliance Framework – Now Available
The FedRAMP compliance framework is now available in VMware Aria Automation for Secure Clouds. FedRAMP leverages the National Institute of Standards and Technology’s (NIST) guidelines, specifically NIST’s Special Publication [SP] 800-53 - Security and Privacy Controls for Federal Information Systems and Organization series, baselines, and test cases.
The FedRAMP Draft Rev. 5. Baselines were released on December 20th, 2021, and align with NIST’s Rev. 5 update. FedRAMP controls and enhancements were selected from the 800-53 Revision 5 catalog and FedRAMP also added standards above the NIST guidelines for low, moderate, and high systems. Controls were selected to address the unique risks of cloud computing environments, including but not limited to multi-tenancy, visibility, control/responsibility, shared resource pooling, and trust.
This release supports the following control groups:
-
Access Control
-
Audit and Accountability
-
Assessment, Authorization, and Monitoring
-
Configuration Management
-
Contingency Planning
-
Identification and Authentication
-
Incident Response
-
Risk Assessment
-
System and Services Acquisition
-
System and Communications Protection
-
System and Information Integrity
June 1, 2023 - What's New
Cloud Entitlement Management for AWS - Public Beta
We are excited to announce the public beta of Cloud Entitlement Management for AWS. With bi-directional visibility into the relationships between cloud identities, entitlements, and resources, users can now manage excess permissions and identify sensitive cloud entitlements that could lead to risky conditions such as a credential exposure across cloud infrastructure. Users are able to:
-
Visualize and categorize what human or machine identities are entitled to access a cloud resource. To view cloud entitlements by resource, you can go to Findings > Click on resource with finding> Entitlements.
-
Determine which principals have access to a specific resource and understand the cloud entitlements for that principal. To explore cloud entitlements for a principal, you can go to Explore > Entitlements.
For more information, please refer to the product documentation.
Amazon Security Lake Integration - Public Beta
Customers can now leverage the integration with the Amazon Security Lake service to conveniently correlate cloud resource misconfiguration data generated in VMware Aria Automation for Secure Clouds with logs from other platforms using the analytics tool of their choice. Customers can create alerts in VMware Aria Automation for Secure Clouds to export findings data in the Open Cybersecurity Schema Framework (OCSF) compliant format to Amazon Security Lake, which centralizes, normalizes and combines security data from multiple sources into a purpose-built data lake that is stored in customer’s AWS account.
This integration is enabled through specific configuration via our outbound S3 integration. Check out the updated product documentation for more information on how to set up the integration to the Amazon Security Lake dedicated S3 bucket.
May 9, 2023 - What's New
GCP Security Command Center Integration - Public Beta
We are excited to announce that the inbound integration for GCP Security Command Center is now available in public beta!
Inbound integrations make it easier to correlate information between cloud resource configurations, posture misconfigurations, threats, and vulnerabilities. When configured, an inbound integration enables ingestion of security findings from external sources such as Amazon GuardDuty, Amazon Inspector, and Azure Defender.
Threat and vulnerability findings from the GCP Security Command Center can now be ingested and correlated by VMware Aria Automation for Secure Clouds, providing an additional layer of security insights and enabling security and operational teams to match cloud configurations to host vulnerabilities from one GUI or report.
GCP Security Command Center can be configured in a few short steps. You can choose which accounts to ingest findings into VMware Aria Automation for Secure Clouds under Settings > Integrations > GCP Security Command Center. To view the findings along with other VMware Aria Automation for Secure Clouds findings, navigate to the various Findings views and choose “GCP Security Command Center” in the finding source filter. To learn more about the GCP Security Command Center, please see the product documentation.
May 4, 2023 - What's New
Support for AWS Budget and Cost Collectors
VMware Aria Automation for Secure Clouds is introducing new collectors for AWS Cost Explorer and AWS Budgets to support new resources in your cloud inventory. If you are using these services and want to monitor these resources for your onboarded accounts, you must add an inline policy to your IAM role with the necessary permissions. We use the SecurityAudit Policy and these actions are not currently available in the AWS managed policy.
To monitor resources in the AWS Budget service, add these permissions to an inline policy:
-
budgets:DescribeBudgetAction
-
budgets:DescribeBudgetActionsForBudget
-
budgets:ViewBudget
To monitor resources in the AWS Cost Explorer service, add these permissions to an inline policy:
-
ce:DescribeCostCategoryDefinition
-
ce:GetAnomalyMonitors
-
ce:GetAnomalySubscriptions
-
ce:GetCostCategories
-
ce:ListTagsForResource
-
ce:ListCostCategoryDefinitions
You can also find these instructions in the onboarding documentation for AWS.
March 23, 2023 - What's New
- Display of SSQL Rule Query for Native Rules
- Cloud Entitlements Management: Entitlements by Resource – Private Beta
- Support for GCP CIS Foundations Benchmark V2.0.0 Now Available
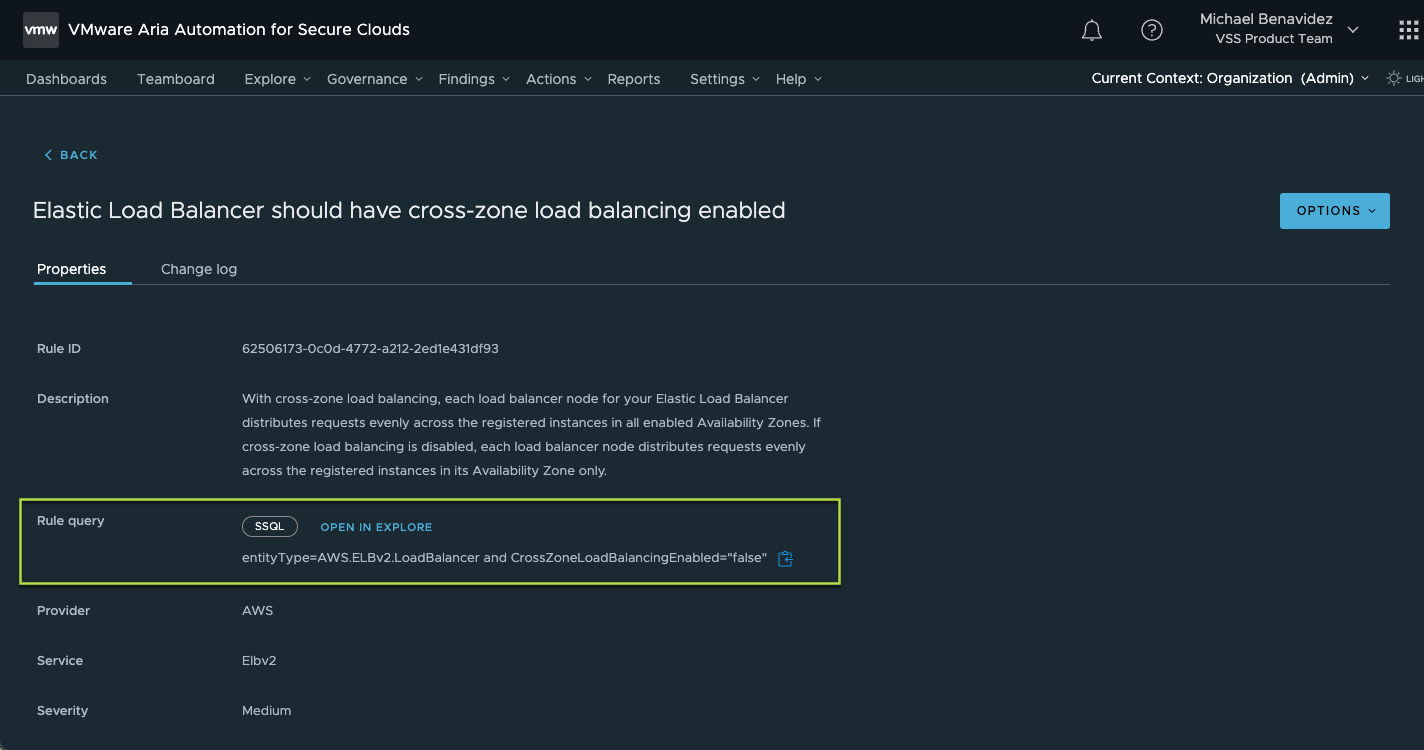
Display of SSQL Rule Query for Native Rules
The VMware Aria Automation for Secure Clouds team has been converting native SSQL rule queries from Gremlin to SSQL to help increase the transparency of our supported rules. We have converted 587 of 1195 (~50%) native rules. You can now easily view and reference the SSQL rule query for all translated native rules in the Rules detail page. To further explore the rule query, open the query in Explore to modify and save the rule as a new custom rule.
For more information on rules properties and rules management, please refer to the product documentation.
Cloud Entitlements Management: Entitlements by Resource – Private Beta
Cloud Entitlements enable principals (users and services) to access and perform actions in the cloud environment. Often these entitlements are inadvertently or unknowingly configured to be too permissive. As a result, cloud resources are misconfigured or worse become accessible by bad actors. Once configured, it may be complex to understand and troubleshoot issues in large environments.
Late last year VMware Aria Automation for Secure Clouds introduced Cloud Entitlements management to help simplify the understanding of complex cloud entitlements, enabling users to review entitlements and see the effective permissions a principal has on a resource.
We are excited to announce that the Entitlements Management private beta now supports Entitlements by Resource. This allows you to determine which principals have access to a specific resource. From there you can dive in and understand the entitlements for that principal. For AWS resources, you will now see cloud entitlements when searching for resources in Explore, when looking at the findings for a specific resource, or when browsing asset inventory.
If you're registered for the beta, this new capability has already been enabled for you. If you're interested in joining the beta, please request access here.

Support for GCP CIS Foundations Benchmark V2.0.0 Now Available
We are excited to announce the availability of the CIS GCP Foundations Benchmark Framework, version 2.0.0.
Updates include:
-
New rules:
-
IAM user should not have Service Account Admin and Service Account User roles assigned together (RuleId: fed8c3d8-6828-445f-ae35-e14ead6b69da) - High
-
IAM user should not have the Cloud KMS Admin role assigned together with the Cloud KMS CryptoKey Encrypter/Decrypter, Cloud KMS CryptoKey Encrypter, or Cloud KMS CryptoKey Decrypter roles (RuleId:2f05cfc2-3559-4a5d-9e07-8472f5065315) - High
-
API key should be rotated every 90 days (RuleId: 02124bf7-03ee-4b9d-8c93-749fc3d7a6b4) - Medium
-
API key usage should be restricted to APIs the application needs to access (RuleId: 804c9d6b-c7c0-4ff0-a120-9706a137d4f2) - Medium
-
API key usage should be restricted to specific hosts and applications (RuleId: cc0ea365-10b1-40ca-ae0d-bb63fd01a50a) - Medium
-
BigQuery data set should be encrypted with customer managed encryption key (RuleId:70cb49d2-35ee-4e2c-851a-0b06d5c310e8) - Medium
-
Dataproc cluster should be encrypted using customer-managed encryption key (RuleId:1d164e3a-814e-484f-b56e-32be96b4f959) - Medium
-
API key should be used only on active service (RuleId: c740729c-4d23-4a29-811c-86fe9e5be264) - Low
-
-
Updated rules:
-
BigQuery Table should be encrypted with customer managed encryption key (RuleId: 8779a3b1-4012-44c6-a8de-50d79f89021c) - Medium
-
Container scanning should be enabled (RuleId: b11f699a-f1fc-4717-b375-7b8be52ba6f5) - Medium
-
Cloud asset inventory should be enabled (RuleId: f7fd5738-991b-4697-b0a3-d5731608415c) - Low
-
March 9, 2023 - What's New
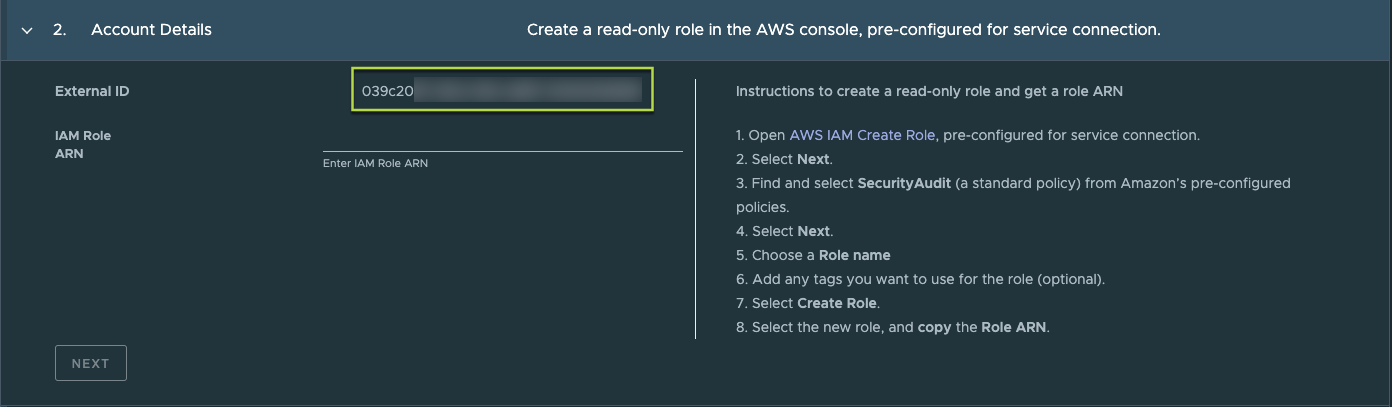
AWS Account Onboarding Update
Any newly onboarded AWS cloud accounts now have a unique external ID for each customer tenant rather than for each cloud account. To ensure that your organization’s data is protected and cannot be accessed by another tenant, you can no longer make changes your external ID. Existing AWS cloud accounts will not be impacted and there is no action required from users.
February 23, 2023 - What's New
- Attaching Kubernetes with Helm Chart - General Availability
- Support for Third-Party Rules in Alerts, Reports, and Suppressions - Now Available
Attaching Kubernetes with Helm Chart - General Availability
You can now onboard a managed or self-managed Kubernetes cluster with a Helm chart in CloudHealth Secure State. If you use a Helm chart for your Kubernetes deployments, you can select the Helm version you are using, then run a single CLI command to install the chart archive with Helm and the collector in your cluster. For more information on using a Helm chart to onboard a Kubernetes cluster, please refer to the product documentation.
Support for Third-Party Rules in Alerts, Reports, and Suppressions - Now Available
Third party rules (such as Amazon GuardDuty, Microsoft Defender for Cloud, and so on) can now be selected in the "Rules" criteria when creating an alert, suppression, or report in CloudHealth Secure State. This lets you focus an alert or suppression on any kind of finding, whether it comes from a CloudHealth Secure State native rule or a third-party source. Likewise, when scheduling or generating reports for findings you can set the criteria to target a report on findings from a specific rule or rules regardless of source.
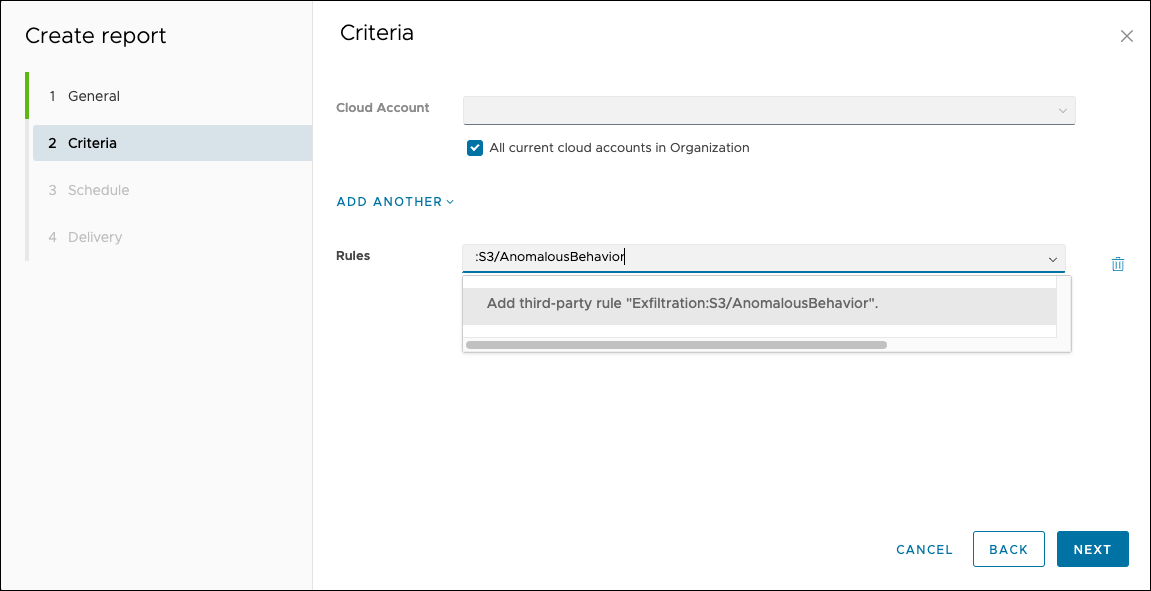
Note that third-party rules don't have predictive text or validation by CloudHealth Secure State when entered as criteria, so you must verify the text matches what is defined by the provider.
For more information, see the product documentation on third-party findings.
February 7, 2023 - What's New
- Support for PCI DSS 4.0 - Now Available
- Support for MITRE ATT&CK Cloud and MITRE ATT&CK Containers 11.0 - Now Available
- Exporting Rules to CSV file
Support for PCI DSS 4.0 - Now Available
The PCI DSS 4.0 compliance framework is now available in CloudHealth Secure State. Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance payment card account data security. PCI DSS provides a baseline of technical and operational requirements designed to protect account data. While specifically designed to focus on environments with payment card account data, PCI DSS can also be used to protect against threats and secure other elements in the payment ecosystem. PCI DSS 4.0 was released on March 31st, 2022, and PCI DSS v3.2.1 will continue to be supported until the next version is released or until it's retired on March 31, 2024.
Updates in the new PCI DSS 4.0 framework include:
-
New controls and updated content to all controls.
-
"Cardholder data" is changed to "account data" to align with usage and intent.
Support for MITRE ATT&CK Cloud and MITRE ATT&CK Containers 11.0 - Now Available
We are excited to announce the availability of the MITRE ATT&CK Cloud 11.0 and MITRE ATT&CK Containers 11.0 frameworks in CloudHealth Secure State. These frameworks have been mapped to controls for AWS, Azure, GCP, and Kubernetes rules.
As part of the overall upgrade to MITRE ATT&CK Enterprise version 11.0, the following changes have been made:
-
Updated descriptions for several controls.
-
In MITRE ATT&CK Containers, the control Scheduled Task/Job (T1053.001) was replaced with Scheduled Task/Job-At (T1053.002) to better reflect adversary behavior.
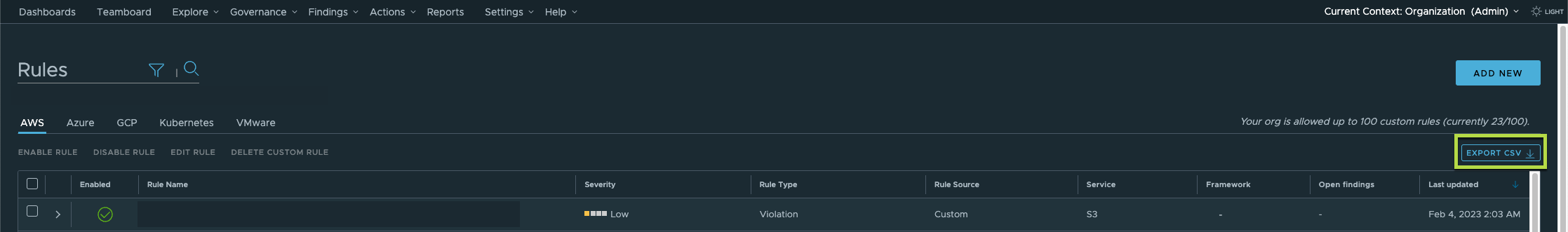
Exporting Rules to CSV file
You can now directly export your rules view to a CSV file with a single click. Any filters applied to your rules data will be retained in the exported CSV file. To export your rules, you can go to the Governance > Rules page in the CloudHealth Secure State client UI and click the Export CSV button at the top right.
January 26, 2023 - What's New
ServiceNow ITSM Integration - Private Beta
We're excited to announce that the ServiceNow integration for IT service management (ITSM) is in private beta. Now you can easily send CloudHealth Secure State findings to ServiceNow as new incidents where they can be tracked and resolved to existing incident workflows. Furthermore, similar to the existing Jira Cloud integration, you can customize the incident template for your integration by changing, removing, or adding more fields from your organization's incident template. For more information, review the documentation.
Please contact your Technical Account Manager if you'd like to participate in the private beta.