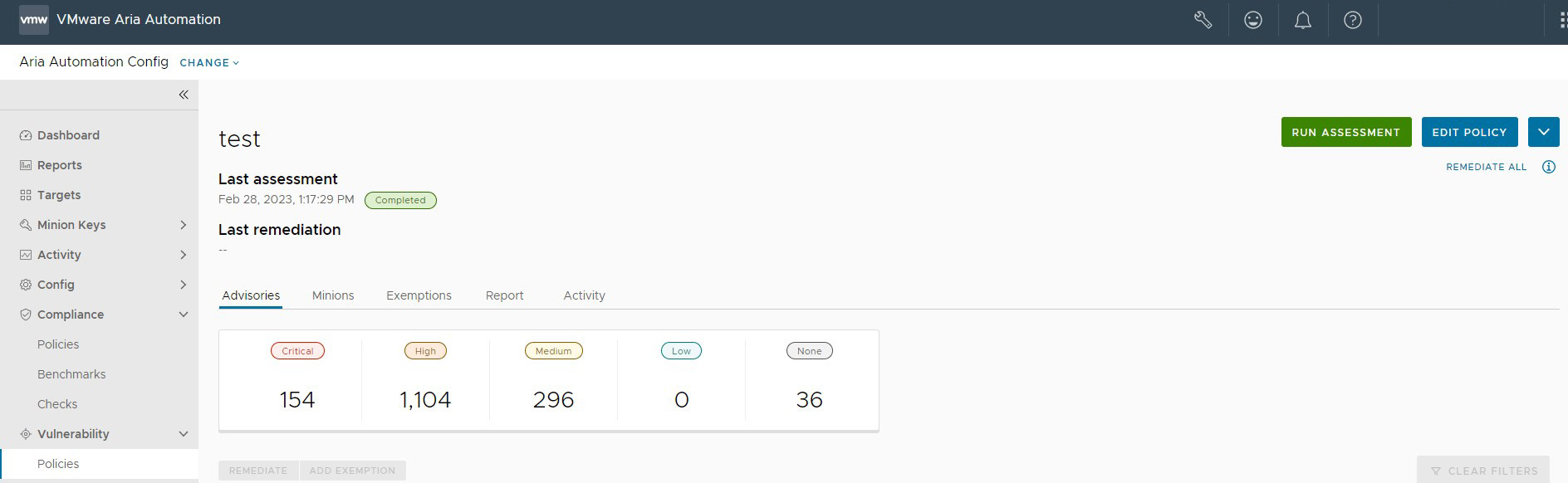
After you’ve created a policy, you can run an assessment that scans the targeted assets against the latest advisories.
From the vulnerability workspace, you can run assessments from one more policies at once by clicking the checkboxes next to each policy and clicking Run assessment.
To view policy details and then run assessment on a single policy:
Prerequisites
Before you can run a vulnerability assessment, you must have an existing vulnerability policy. For more information, see How do I create a vulnerability policy.
Procedure
Results
Automation for Secure Hosts Vulnerability scans your system against the latest advisories. During assessment, no changes are made to any of your systems. After the assessment is complete, you can remediate any advisories. You can view the status of current or past assessments by clicking a policy in the Vulnerabilty workspace and the clicking on the Activity tab. The results page lists all queued, in progress, and completed scans.