This topic introduces Carbon Black Managed Detection, Carbon Black Managed Detection and Response (MDR), and Carbon Black Managed Threat Hunting (MTH). It describes the differences and benefits of each product in the Carbon Black MDR platform.
Carbon Black MDR Platform Product Comparison
The following table gives a concise breakdown of the different properties for Carbon Black Managed Detection, MDR, and MTH.
| Carbon Black Managed Detection | Carbon Black Managed Detection and Response | Carbon Black Managed Threat Hunting | |
|---|---|---|---|
| Requires | Carbon Black Cloud Endpoint Standard | Carbon Black Cloud Endpoint Standard | Carbon Black Cloud Enterprise EDR |
| Eligible Alerts¹ | CB Analytics Severity 5+ | CB Analytics Severity 5+ | Watchlist (MDR intelligence) only |
| SLO | 2 hours: Severity 8 -10 only | 2 hours: Severity 8 -10 only | N/A |
| Staffing | MDR Analyst Team 24/7 | MDR Analyst Team 24/7 | MDR Analyst Team, US business hours only |
| Communication | In-console one-way through alert notes, SIEM (API/Forwarder), and email notifications. Likely threats only. | In-console two-way through alert notes, SIEM (API/Forwarder), and email notifications. Likely threats only. | In-console two-way through Alert notes, SIEM (API/Forwarder), and email notifications. Likely threats only. |
| Reporting | Daily/Monthly | Daily/Monthly | After Threat Hunt |
| Containment | N/A | Ban hash, modify policy, quarantine endpoint | Ban hash, modify policy, quarantine endpoint |
| Proactive Hunting | N/A | N/A | Emerging Threats |
|
Note: ¹ The MDR Analyst team only reviews alerts in the "Open" Workflow state. You may not receive an MDR Determination if the alert is closed by you or an auto-closure rule before it is triaged by the MDR Analyst team.
|
|||
Managed Detection and Managed Detection and Response (MDR)
Carbon Black Managed Detection and MDR are add-ons to Carbon Black's NGAV product that validate and prioritize alerts, uncover new threats, and accelerate investigations. MDR offers the functionality of Carbon Black Managed Detection while containing the threat 24/7 and providing two-way communication with the MDR team for likely threats.
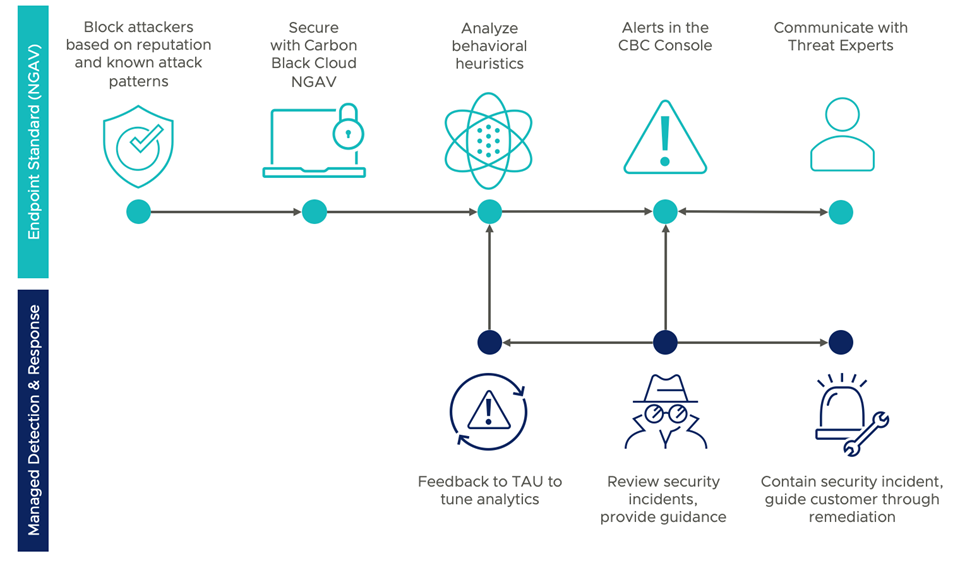
The key components of MDR are:
- Immediate action to contain security incidents:
Responding to threats allows analysts to immediately act on malicious behavior to limit and contain an incident.
- Banning malicious hashes:
Analysts can ban malicious hashes to prevent known bad binaries from running on assets in your organization.
- Policy modification:
Analysts can move impacted devices to cloned policy groups and implement any needed rules to stop an ongoing threat.
- Quarantine impacted devices:
After an analyst has confirmed malicious activity on an asset, they can quarantine the impacted asset. Quarantining the asset from other assets on the network prevents further executions of malicious actions and lateral movement.
Managed Threat Hunting (MTH)
MTH is the proactive hunting mechanism for emerging and prevalent threats for Carbon Black Cloud Enterprise EDR. MTH leverages the expertise of MDR analysts and their visibility into the overall threat landscape to carry out targeted threat hunts and investigate generated alerts.
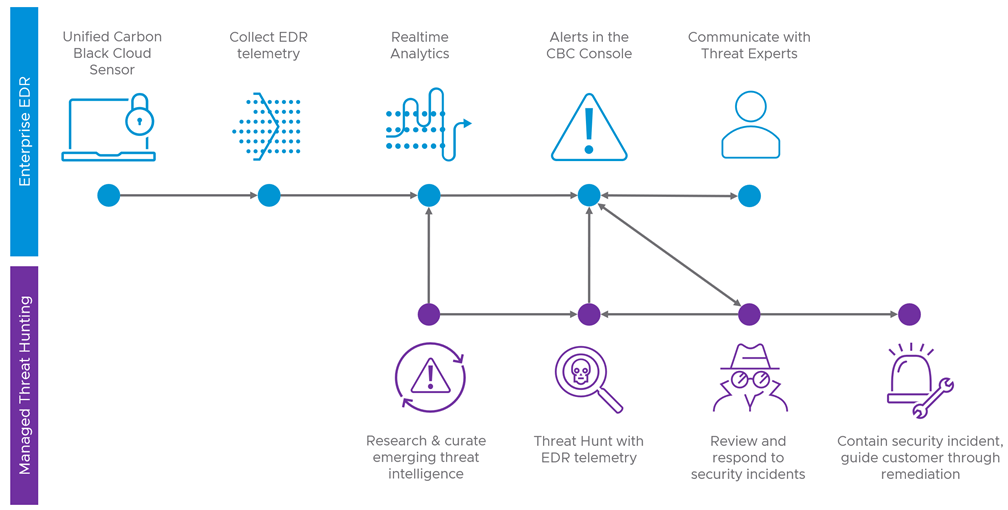
A threat hunt is when MDR analysts proactively search for emerging threats in your environment. Analysts run threat hunts when they have discovered new or evolving intelligence. This timing can vary from weekly to multiple times per day.
Upon completion of the hunt, MDR analysts notify you by email with a summary of threats found. On the Alerts page in the Carbon Black Cloud console, alerts that are discovered by a threat hunt have an MDR Threat Hunt badge and a pane that includes additional details. See Working with MDR and MTH Alerts.
As an MTH customer, you can view MDR analyst workflow actions such as investigating an alert, setting the alert determination, and adding comments. For more information about viewing analyst comments, see: MDR Platform Communications.
You can view MDR analyst containment actions such as banning hashes, modifying policy, or quarantining assets in the Audit Log. See Audit Logs.