With MDR and MTH, you can view all alerts covered by MDR and MTH on the Alerts page of the Carbon Black Cloud console.
For more information about working with alerts in Carbon Black Cloud, see Alerts and Alert Triage.
You can search for MDR and MTH alerts using the search term mdr_alert:true. These alerts have either a blue MDR or MDR Threat Hunt badge. MTH alerts are Watchlist alert types.
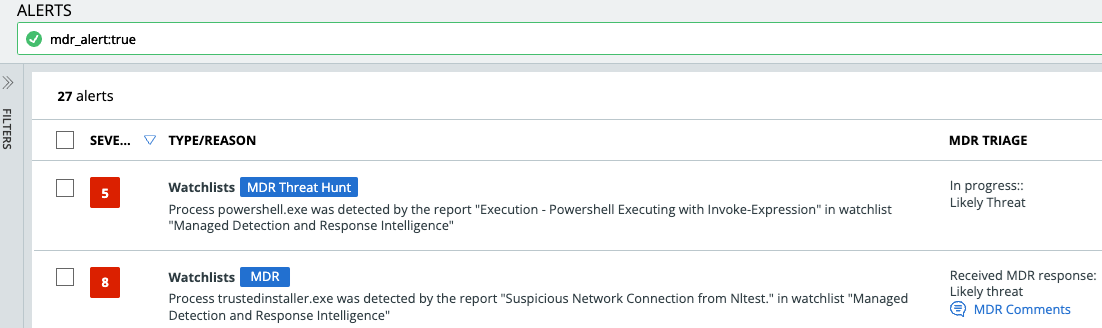
MDR and MTH Alert Types
The following alert types are covered by MD and MDR:
- CB Analytics Alerts
- Analysts can take action on likely threat alerts if they have been granted permission to do so per policy settings.
- CB Analytics alerts severity 5-10 are eligible for MDR analyst review. CB Analytics alerts severity 8-10 are triaged within 2 hours of import into the MDR analyst queue.
- Level 5-7 alerts include generic virus-like behavior, monitoring user input, potential memory scraping, and password theft.
- Alerts at level 8 or higher include ransomware, lateral movement, credential scraping, reverse command shells, and process hollowing.
- Alert severity level does not indicate that the alert is a true positive. Legitimate activity can have the same behavior as malicious activity, which can be the reason why an analyst closes a level 8 alert as a false positive.
- The MDR team treats all reviewed alerts as time-sensitive because a threat can escalate quickly at any stage of the attack. However, the team prioritizes alerts with a higher severity level.
- For more information about alert severity and target values, see Alert and Report Severity.
The following alert types are covered by MTH:
- MDR Watchlist Alerts
Analysts use an MDR curated watchlist (Managed Detection and Response Intelligence) to surface any likely threats identified in your environment as alerts, regardless of severity. Analysts can take action on these alerts if they have been granted permission to do so per policy settings.
- MDR Threat Hunt Alerts
- Analysts conduct threat hunts in your environment using specialized watchlist reports to look for new and emerging threats.
- If a threat hunt identifies activity determined to be a likely threat, an alert is created. If no threats are identified, you are still notified by email that a threat hunt was conducted in your environment.