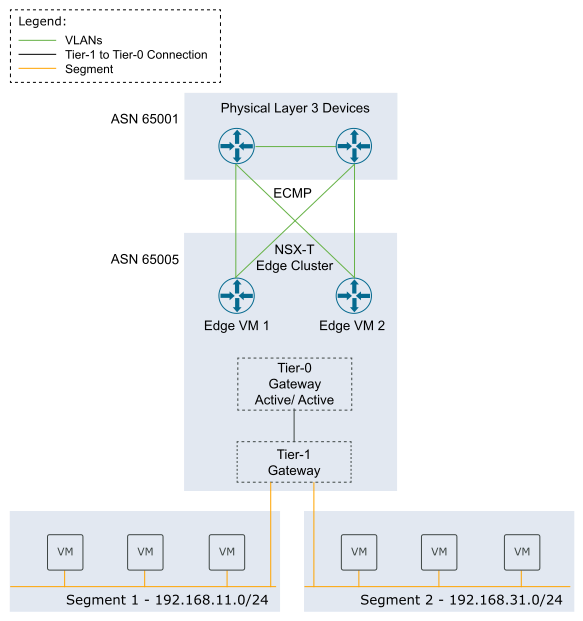
Deploy an NSX Edge cluster to provide north-south routing and network services to a workload domain.
After you create an NSX Edge cluster, you can use SDDC Manager to expand or shrink it by adding or deleting NSX Edge nodes.
This procedure describes how to use SDDC Manager to create an NSX Edge cluster with NSX Edge node virtual appliances. If you have latency intensive applications in your environment, you can deploy NSX Edge nodes on bare-metal servers. See Deployment of VMware NSX-T Edge Nodes on Bare-Metal Hardware for VMware Cloud Foundation 4.0.x.
Prerequisites
Procedure
- In the navigation pane, click Inventory > Workload Domains.
- In the Workload Domains page, click a domain name in the Domain column.
- Select Actions > Add Edge Cluster.
- Verify the prerequisites, select Select All, and click Begin.
- Enter the configuration settings for the NSX Edge cluster and click Next.
Setting Description Edge Cluster Name Enter a name for the NSX Edge cluster. MTU Enter the MTU for the NSX Edge cluster. The MTU can be 1600-9000. ASN Enter an autonomous system number (ASN) for the NSX Edge cluster. Tier-0 Router Name Enter a name for the tier-0 gateway. Tier-1 Router Name Enter a name for the tier-1 gateway. Edge Cluster Profile Type Select Default or, if your environment requires specific Bidirectional Forwarding Detection (BFD) configuration, select Custom. Edge Cluster Profile Name Enter an NSX Edge cluster profile name. (Custom Edge cluster profile only) BFD Allowed Hop Enter the number of multi-hop Bidirectional Forwarding Detection (BFD) sessions allowed for the profile. (Custom Edge cluster profile only) BFD Declare Dead Multiple Enter the number of number of times the BFD packet is not received before the session is flagged as down. (Custom Edge cluster profile only) BFD Probe Interval (milliseconds) BFD is detection protocol used to identify the forwarding path failures. Enter a number to set the interval timing for BFD to detect a forwarding path failure. (Custom Edge cluster profile only) Standby Relocation Threshold (minutes) Enter a standby relocation threshold in minutes. (Custom Edge cluster profile only) Edge Root Password Enter and confirm the password to be assigned to the root account of the NSX Edge appliance. Edge Admin Password Enter and confirm the password to be assigned to the admin account of the NSX Edge appliance. Edge Audit Password Enter and confirm the password to be assigned to the audit account of the NSX Edge appliance. NSX Edge cluster passwords must meet the following requirements:- At least 12 characters
- At least one lower-case letter
- At least one upper-case letter
- At least one digit
- At least one special character (!, @, ^, =, *, +)
- At least five different characters
- No dictionary words
- No palindromes
- More than four monotonic character sequence is not allowed
- Specify the use case details and click Next.
Setting Description Use Case - Select Kubernetes - Workload Management to create an NSX Edge cluster that complies with the requirements for deploying vSphere with Tanzu. See Workload Management. If you select this option, you cannot modify the NSX Edge form factor or Tier-0 service high availability settings.
- Select Application Virtual Networks to create an NSX Edge cluster that complies with the requirements deploying vRealize Suite components. See Deploying Application Virtual Networks.
Note: Management domain only.
- Select Custom if you want an NSX Edge cluster with a specific form factor or Tier-0 service high availability setting.
Edge Form Factor - Small: 4 GB memory, 2 vCPU, 200 GB disk space. The NSX Edge Small VM appliance size is suitable for lab and proof-of-concept deployments.
- Medium: 8 GB memory, 4 vCPU, 200 GB disk space. The NSX Edge Medium appliance size is suitable for production environments with load balancing.
- Large: 32 GB memory, 8 vCPU, 200 GB disk space. The NSX Edge Large appliance size is suitable for production environments with load balancing.
- XLarge: 64 GB memory, 16 vCPU, 200 GB disk space. The NSX Edge Extra Large appliance size is suitable for production environments with load balancing.
Tier-0 Service High Availability In the active-active mode, traffic is load balanced across all members. In active-standby mode, all traffic is processed by an elected active member. If the active member fails, another member is elected to be active. Workload Management requires Active-Active.
Some services are only supported in Active-Standby: NAT, load balancing, stateful firewall, and VPN. If you select Active-Standby, use exactly two NSX Edge nodes in the NSX Edge cluster.
Tier-0 Routing Type Select Static or EBGP to determine the route distribution mechanism for the tier-0 gateway. If you select Static, you must manually configure the required static routes in NSX Manager. If you select EBGP, VMware Cloud Foundation configures eBGP settings to allow dynamic route distribution. - Enter the configuration settings for the first NSX Edge node and click Add Edge Node.
Setting Description Edge Node Name (FQDN) Enter the FQDN for the NSX Edge node. Each node must have a unique FQDN. Management IP (CIDR) Enter the management IP for the NSX Edge node in CIDR format. Each node must have a unique management IP. Management Gateway Enter the IP address for the management network gateway. Edge TEP 1 IP (CIDR) Enter the CIDR for the first NSX Edge TEP. Each node must have a unique Edge TEP 1 IP. Edge TEP 2 IP (CIDR) Enter the CIDR for the second NSX Edge TEP. Each node must have a unique Edge TEP 2 IP. The Edge TEP 2 IP must be different than the Edge TEP 1 IP. Edge TEP Gateway Enter the IP address for the NSX Edge TEP gateway. Edge TEP VLAN Enter the NSX Edge TEP VLAN ID. Cluster Select a vSphere cluster to host the NSX Edge node. Cluster Type Select L2 Uniform if all hosts in the vSphere cluster have identical management, uplink, host TEP, and Edge TEP networks. Select L2 non-uniform and L3 if any of the hosts in the vSphere cluster have different networks.
Important: VMware Cloud Foundation does not support Edge cluster creation on L2 non-uniform and L3 vSphere clusters.First NSX VDS Uplink Click Advanced Cluster Settings to map the first NSX Edge node uplink network interface to a physical NIC on the host, by specifying the ESXi uplink. The default is uplink1. When you create an NSX Edge cluster, SDDC Manager creates two trunked VLAN port groups. The information you enter here determines the active uplink on the first VLAN port group. If you enter uplink3, then uplink3 is the active uplink and the uplink you specify for the second NSX VDS uplink is the standby uplink.
The uplink must be prepared for overlay use.
Second NSX VDS Uplink Click Advanced Cluster Settings to map the second NSX Edge node uplink network interface to a physical NIC on the host, by specifying the ESXi uplink. The default is uplink2. When you create an NSX Edge cluster, SDDC Manager creates two trunked VLAN port groups. The information you enter here determines the active uplink on the second VLAN port group. If you enter uplink4, then uplink4 is the active uplink and the uplink you specify for the first NSX VDS uplink is the standby uplink.
The uplink must be prepared for overlay use.
First Tier-0 Uplink VLAN Enter the VLAN ID for the first uplink. This is a link from the NSX Edge node to the first uplink network.
First Tier-0 Uplink Interface IP (CIDR) Enter the CIDR for the first uplink. Each node must have unique uplink interface IPs. Peer IP (CIDR) Enter the CIDR for the first uplink peer. (EBGP only) Peer ASN Enter the ASN for the first uplink peer. (EBGP only) BGP Peer Password Enter and confirm the BGP password. (EBGP only). Second Tier-0 Uplink VLAN Enter the VLAN ID for the second uplink. This is a link from the NSX Edge node to the second uplink network.
Second Tier-0 Uplink Interface IP (CIDR) Enter the CIDR for the second uplink. Each node must have unique uplink interface IPs. The second uplink interface IP must be different than the first uplink interface IP. Peer IP (CIDR) Enter the CIDR for the second uplink peer. (EBGP only) ASN Peer Enter the ASN for the second uplink peer. (EBGP only) BGP Peer Password Enter and confirm the BGP password. (EBGP only). - Click Add More Edge Nodes to enter configuration settings for additional NSX Edge nodes.
A minimum of two NSX Edge nodes is required. NSX Edge cluster creation allows up to 8 NSX Edge nodes if the Tier-0 Service High Availability is Active-Active and two NSX Edge nodes per NSX Edge cluster if the Tier-0 Service High Availability is Active-Standby.
- When you are done adding NSX Edge nodes, click Next.
- Review the summary and click Next.
SDDC Manager validates the NSX Edge node configuration details.
- If validation fails, use the Back button to edit your settings and try again.
To edit or delete any of the NSX Edge nodes, click the three vertical dots next to an NSX Edge node in the table and select an option from the menu.
- If validation succeeds, click Finish to create the NSX Edge cluster.
You can monitor progress in the Tasks panel.
Example