Welcome to the VMware Live Cyber Recovery pre-deployment checklist.
Introduction
To get started using VMware Live Cyber Recovery, use this checklist to track and manage all the information you need to successfully deploy and use VMware Live Cyber Recovery.
VMware Live Cyber Recovery does not support organization level IP Allow List authentication policies. If IP Allow Lists are enabled in your organization, it might prevent you from configuring an API token in the VMware Live Cyber Recovery UI, or connecting a cloud file system to a recovery SDDC. If your organization leverages the organization level IP Allow List feature, contact support prior to deployment for assistance.
Longer Lead-Time Items
- Open firewall ports. You need to open firewall ports to allow for communication between your production sites and VMware Live Cyber Recovery components. This pre-requisite for production sites can take some time, so we recommend you do this first. View details about firewall port requirements here.
- Set up AWS account, Virtual Private Cloud (VPC), and Subnet. An AWS account must be linked to your VMware Cloud organization before you can deploy a new SDDC. Your AWS VPC subnet, and AWS account also must meet certain requirements, which you can view here.
Prior to Buying the Service
- Protected VM subscriptions. The number of virtual machines being replicated using the service, regardless of whether the virtual machines are currently powered on in the recovery site.
- Protected capacity subscriptions. The sum of the logical (used) storage size of all protected virtual machines and all incremental cloud backups (snapshots) you choose to retain. If you are intending to only use VMware Live Site Recovery, then you do not need to buy a protected capacity subscription. Protected capacity subscriptions only apply to VMware Live Cyber Recovery.
Prior to Activating First Recovery Region
Decide what regions you’d like to recover your production site workloads to.
- The recovery region is the location where you want to deploy the VMware Live Cyber Recovery Orchestrator and cloud file system.
- If you already have a subscription created, or are planning on creating one in the future, be sure that the subscription region matches your recovery region location.
Prior to Deploying First Cloud File System
It is important that your cloud file system is deployed in the correct location. Make sure you have the following information prior to deployment.
| Item | Value |
|---|---|
| (If unsure, allow automatic selection) |
|
| (If applicable) |
|
| (If applicable, should match cloud file system AZ ID) |
|
| (If applicable) |
|
| (If applicable, should not match cloud file system AZ ID) |
- If you are unsure of the AZ ID to deploy your cloud file system to, allow automatic selection. Using auto-select prevents selecting the wrong AZ, which requires support assistance to change.
- Your recovery SDDC AZ ID must match your cloud file system AZ ID.
- Your production site SDDC AZ ID must not match cloud file system AZ ID.
- Your AWS VPC must be in the same AWS region and AZ as where you deploy your cloud file system. As a best practice, create a subnet in every AWS AZ you want to use before you deploy a cloud file system. For more information about VPCs and subnets, see here.
Prior to Setting Up First Protected Site
Does your protected site meet the following resource requirements?
| Site Resource | Value |
|---|---|
| |
Version 7.0 or later |
| |
Version 7.0 U3 or later |
| |
8 GHz (reserved) |
| |
12 GiB (reserved) |
| |
100 GiB virtual disk |
- How do other components of your production site measure up to these requirements? Refer to the VMware Interoperability Matrix.
- If you plan to use ransomware recovery or take quiesced snapshots, make sure those VMs have the latest versions of VMware Tools installed on them.
- All protected VMware Cloud on AWS SDDCs must reside in the same VMware Cloud Organization as VMware Live Cyber Recovery.
- VMware Live Cyber Recovery does not support an internet proxy server between the cyber onnector and the cloud.
Firewall ports
You also need to open firewall ports to allow for communication between your production sites and VMware Live Cyber Recovery components.
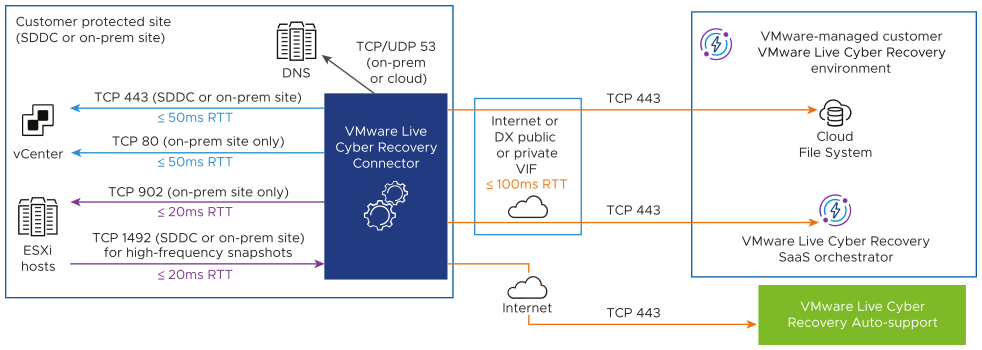
| Protocol | Port | Source | Destination | Service Description | Classification |
|---|---|---|---|---|---|
| Protected site | |||||
| TCP | 443 | Cyber Recovery connector | vCenter Server (on-premises site or SDDC) |
vCenter Server web service | Outbound |
| TCP | 80 | Cyber Recovery connector | vCenter Server (on-premises site only) |
vCenter Server web service | Outbound |
| TCP | 902 | Cyber Recovery connector | ESXi Management IP address (on-premises site only) |
Reading/writing vdisks | Outbound |
| TCP | 1492 | ESXi hosts | Cyber Recovery connector (For on-premises sites. For VMware Cloud on AWS SDDCs, this outbound rule for ESXi hosts is already configured.) |
For high-frequency snapshots, reading/writing vdisks. | Inbound |
| VMware Live Cyber Recovery Components | |||||
| TCP | 443 | Cyber Recovery connector | Cloud file system |
Encrypted tunnel for data transfers and metadata operations | Outbound |
| TCP | 443 | Cyber Recovery connector | Orchestrator | Management service | Outbound |
| TCP | 443 | Cyber Recovery connector | VMware auto-support server | Support service | Outbound |
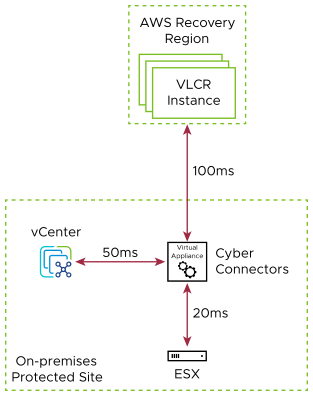
To ensure optimum performance and behavior, we recommend not to exceed the round trip latencies shown in the following diagram.
To set up your protected sites, you’ll need the following information, which slightly varies from setting up an SDDC protected site.
On-Premises Protected Site
- Determine whether to use public internet/Direct Connect (DX) Public VIF or Direct Connect Private VIF for your Cyber Recovery connector to cloud connection. The connection is responsible for the replication and recovery of snapshots. If you plan to use a Direct Connect Private VIF, here’s what you need to configure.
- Select a time zone for your protection group schedules.
| On-premises vCenter | Value |
|---|---|
| |
|
| |
VMware Cloud on AWS SDDC Protected Site
| VMC on AWS Protected SDDC item | Value |
|---|---|
|
|
|
| |
|
| |
| VMC on AWS vCenter item | Value |
|---|---|
| |
You need the following information per-connector:
| Item | Value |
|---|---|
| |
|
| |
|
| |
|
| (if not DHCP) |
|
|
|
|
| |
- How many sites are managed by a single vCenter? If there are multiple physical locations per vCenter, contact VMware support.
- Your total protected capacity should match what was purchased in your term subscription (if applicable).
- If you are purchasing a subscription to avoid on-demand overages, your total protected capacity should not exceed what was purchased in your term subscription (subscriptions are optional but offer better commercial terms for long-term use).
- Does your protected site exceed 1000 VMs? If so, you might experience some responsiveness issues with the VMware Live Cyber Recovery UI. These issues might include slow loading of pages when previewing protection group VM membership, creating and editing Recovery Plans, and during plan compliance checks. Does your total protected VMs exceed 2500 per-Orchestrator? Refer to the Configuration Maximums tool to check.
- Except for lab environments, we recommend at least two Cyber Recovery connectors per site for redundancy and for load balancing.
Prior to Recovery SDDC Creation or Attachment
An AWS account must be linked to your VMware Cloud organization before you can deploy a new SDDC. Find instructions about linking your AWS account here.
- Subnet must be in an AWS AZ where VMC on AWS is available.
- Subnet must exist in the connected AWS account.
- AWS account being linked must have sufficient capacity to create a minimum of 15 ENIs per SDDC, in each region where an SDDC is deployed.
- More requirements are located here.
- We recommend that you dedicate a /26 CIDR block to each SDDC and do not use that subnet for any other AWS services or EC2 instances.
- If your AWS account is not yet connected to your VMC organization, we recommend using the VMware Cloud console to create your recovery SDDC for a smoother experience. You can attach this SDDC to your VMware Live Cyber Recovery instance in the VMware Live Cyber Recovery UI.
You can choose whether to leave your recovery SDDCs always on (such as for a Pilot Light deployment), or launch more recovery SDDCs as needed for testing or failover purposes. You can also specify the number of hosts for your recovery SDDC. During deployment, be ready to provide the following information:
| recovery SDDC Item | Value |
|---|---|
| |
|
| |
- If you are planning on purchasing Pilot Light hosts, you must purchase a separate VMware Cloud on AWS reserved instance subscription.
- Internal/Site isolated networks, which are not accessible from outside (public) or other sites (private).
- External networks, which are accessible from the internet (public) without VPN.
- Stretched networks between sites, which are accessible from other sites (internal) or from VPN into the SDDC.
| Protected Site Network | SDDC Network | Network Type |
|---|---|---|
|
|
Additional Suggested Items
To enable others in your organization appropriate access to the VMware Live Cyber Recovery UI, you need to invite them to your VMware Cloud organization with proper credentials and role assignment.
| CSP Org ID | User Email | VMware Live Cyber Recovery Role |
|---|---|---|
|
|
|
|
|
|
|
|
The user invitation process requires that you assign roles to your users within your organization. Here is a full list of VMware Live Cyber Recovery user roles.
Additional Resources
Thank you for following the pre-deployment checklist. Contact technical services if you run into any issues.
