When you activate ransomware recovery services and start VMs in validation, they are put into a 'Quarantined+Analysis' network, which means those VMs can only connect over the internet to integrated security and vulnerability servers on Carbon Black Cloud and to basic network services like DNS and NTP.
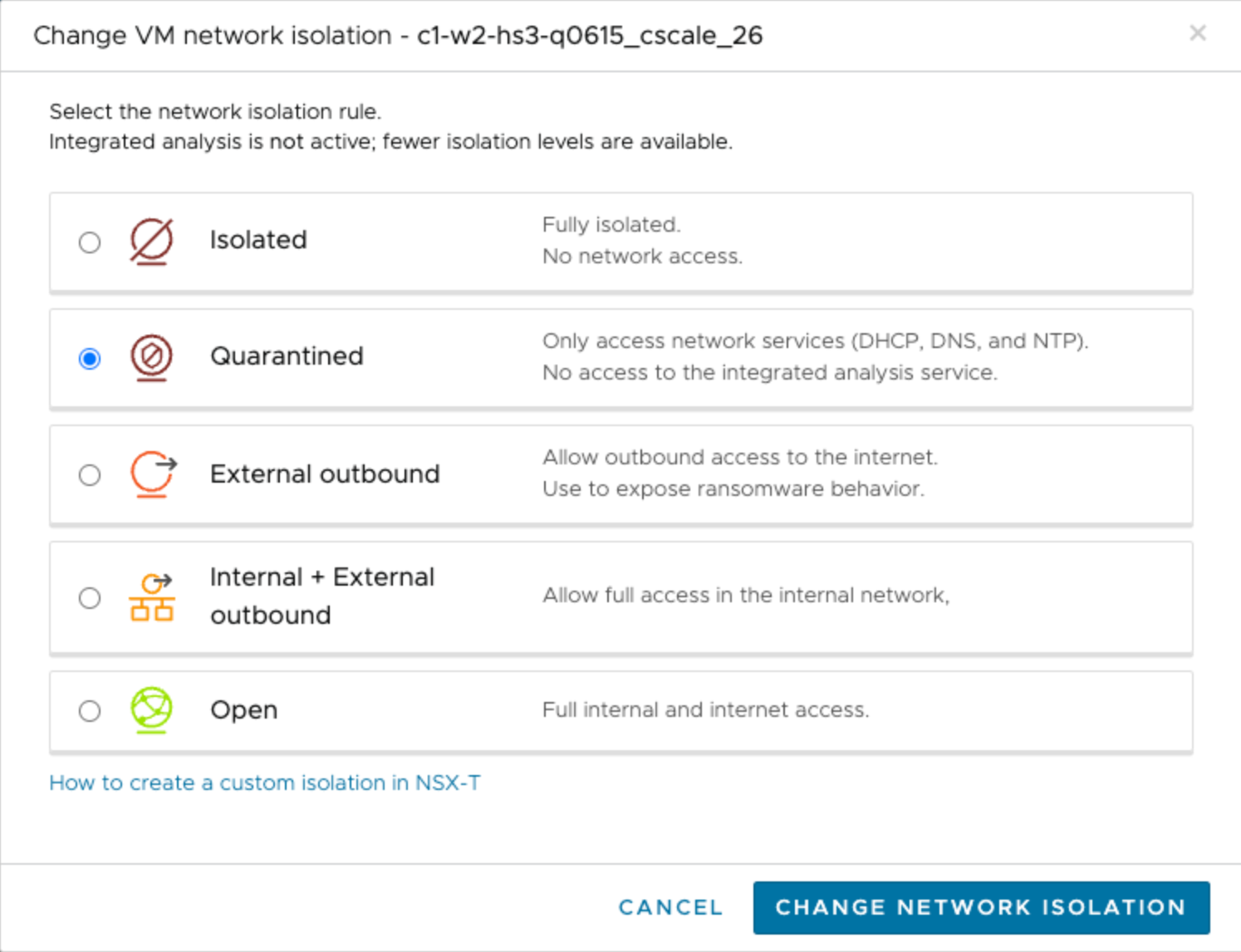
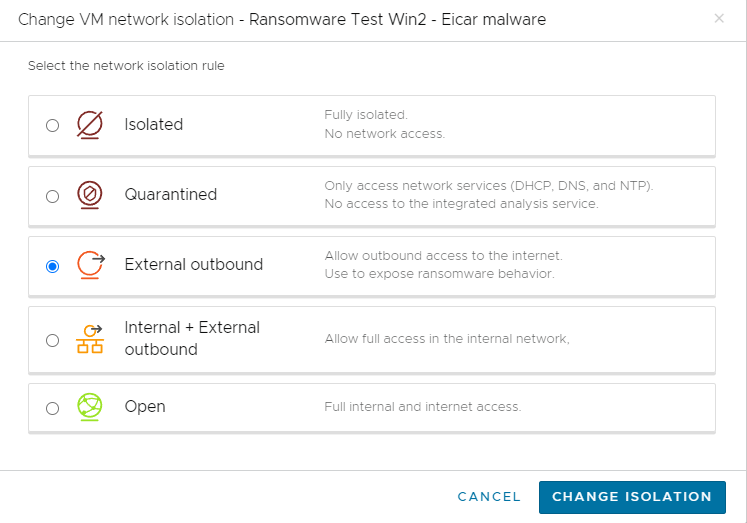
Once a VM has been moved into the validation stage, you can choose different network isolation levels for one or more VMs on the recovery SDDC, depending on your method of analysis and how much isolation you require.
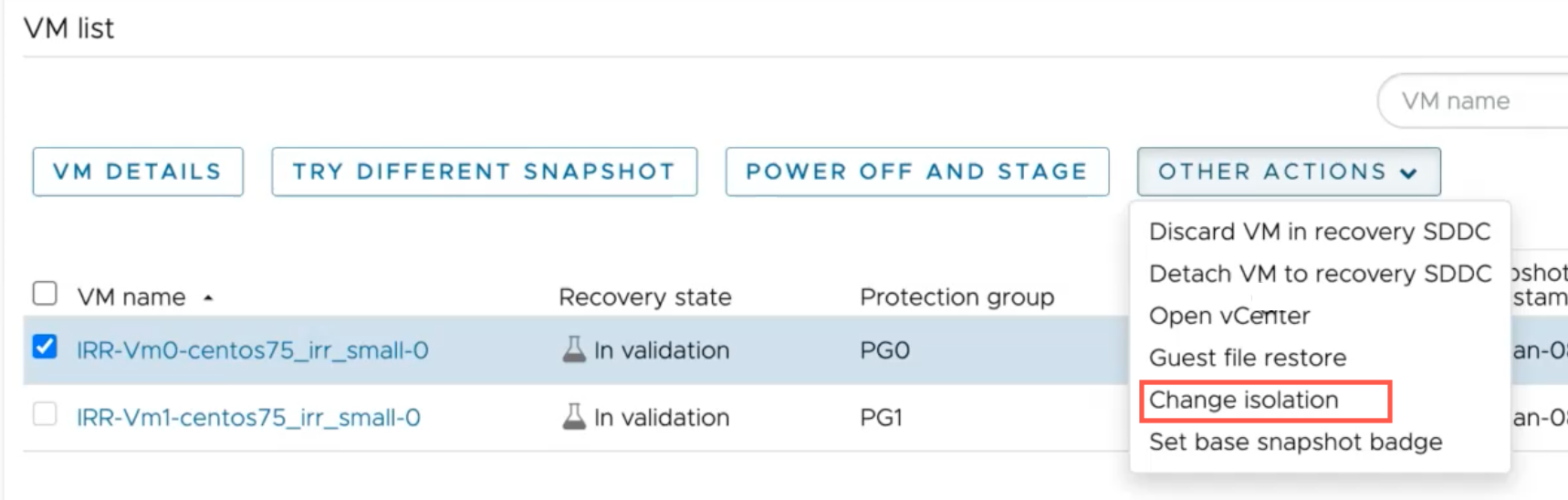
You can select multiple VMs in a running plan, and then from the Other Actions menu, select Change Isolation.
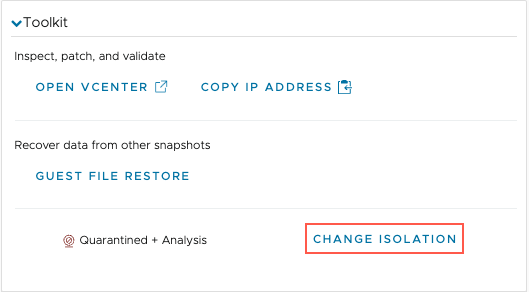
Or, you can change the network when a VM is started and in validation, by clicking Change Isolation from the Toolkit panel.
Some isolation levels require NSX Advanced Firewall. When NSX Advanced Firewall is enabled, VMware Ransomware Recovery creates firewall rules for the various network isolation levels during recovery operations. When all recovery plans for ransomware are ended, all firewall groups and rules are deleted on the recovery SDDC.
If your SDDC does not have NSX Advanced Firewall enabled, VMware Live Cyber Recovery enables it each time you run a recovery plan for ransomware. When the last concurrent plan is deactivated, NSX Advanced Firewall is also deactivated.
Network Isolation Levels Allowed Connectivity
| Network Access Level | NSX-T Advanced Firewall required for security scanning | DHCP, DNS, NTP | Integrated Security analysis and scanning | Outbound External | Outbound East-West | Inbound External | Inbound East-West* |
|---|---|---|---|---|---|---|---|
| Isolated |
No |
||||||
| Quarantined |
No |
 |
 |
||||
|
Quarantined +Analysis
Note: Default isolation level when
NSX Advanced Firewallis enabled.
|
Yes |  |
 |
||||
|
External Outbound
Note: Default isolation level used when
NSX Advanced Firewallis not enabled.
|
No. |
 |
 |
 |
|||
| Internal Inbound |
Yes |
 |
 |
 |
|||
| Internal |
Yes |
 |
 |
 |
 |
||
| Internal + External Outbound | No |
 |
 |
 |
 |
||
| Open |
No |
 |
 |
 |
 |
 |
 |
Network Isolation with NSX Advanced Firewall On
When you activate integrated security and vulnerability analysis and turn on NSX Advanced Firewall in the Settings dialog box, and your recovery plan has ransomware recovery and integrated analysis on, VMs in the validation state are placed into the Quarantine+Analysis network isolation level.
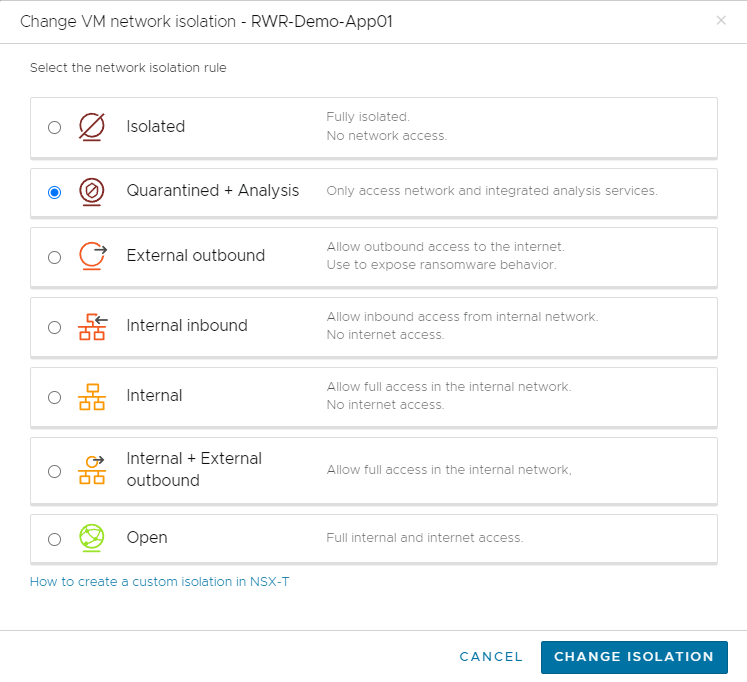
Network Isolation with NSX Advanced Firewall Off
If you activate integrated security and vulnerability analysis but turn off NSX Advanced Firewall in the Settings dialog box, and your recovery plan has ransomware recovery and integrated analysis on, VMs in the validation state are placed into the External Outbound network isolation level. This isolation level allows the sensors installed on the VMs to connect to Carbon Black Cloud.
Network Isolation with Integrated Security and Vulnerability Analysis Off
If you deactivate integrated security and vulnerability analysis from the Settings dialog box, VMs in the validation state are placed into the Quarantined network isolation level.