In addition to disaster recovery, you can configure a recovery plan to perform ransomware recovery operations with integrated vulnerability and security analysis.
In a recovery plan, select the 'Activate ransomware recovery' option to use the plan for ransomware recovery or ransomware recovery tests.
When you click either the Ransomware Recovery or Ransomware Test buttons in the recovery plans list, you change the plan to ransomware recovery mode, so you can start validating and recovering the VMs in the plan.
Configuring ransomware for a recovery plan requires choosing from the following options:
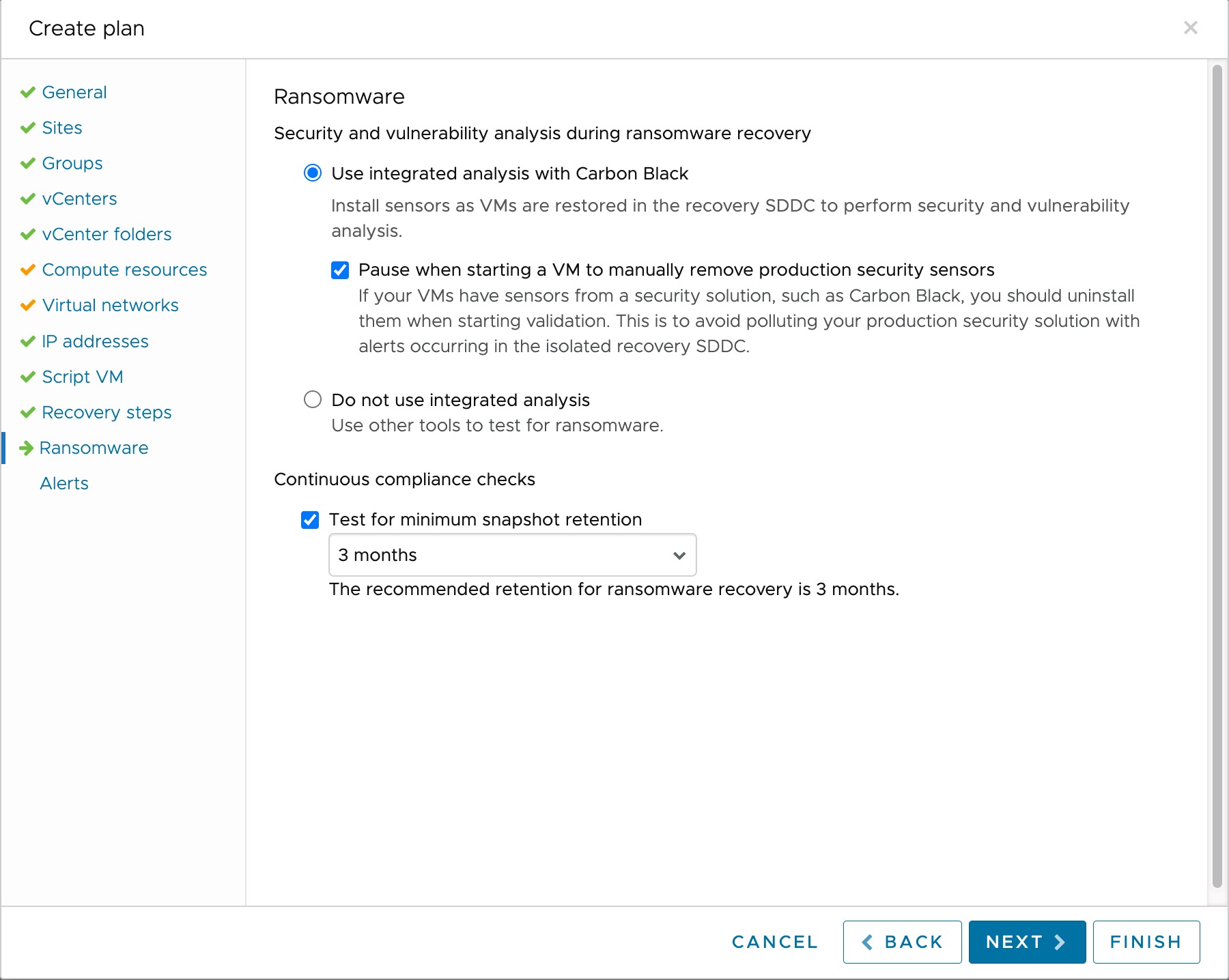
- Use integrated analysis. Enable integrated security and vulnerability analysis for VMs in the plan. When you run the plan and start VMs for recovery, VMware Live Cyber Recovery installs a security sensor on VMs, which enables ransomware analysis. For Linux VMs, you must install the security sensor manually, and uninstall any existing security sensors from the VM. For more information, see Manually Install Sensors. Integrated analysis does not trigger any additional charges.
- Pause when starting a VM to manually remove production security sensors. Pause when starting VMs during ransomware recovery so you can remove any production sensors or security software, which might interfere with VMware Live Cyber Recovery integrated analysis and impact the isolated recovery environment of the recovery SDDC. For more information, see Uninstalling Sensors.
- Do not use integrated analysis. If you want to use your own security tools for ransomware recovery on your recovery SDDC, select this option. When selected, no VMware Live Cyber Recovery security sensors are installed when you start VMs during ransomware recovery.
- Continuous compliance checks. Use this to test for protection group snapshot retention policies that are shorter than the duration you select here. For ransomware recovery, the recommneded snapshot retention is 3 months.
Preparing Linux VMs for Ransomware Recovery
Having the launcher present on Linux VMs allows VMware Live Cyber Recovery to automatically install the security sensor needed for ransomware recovery.
In this situation, the sensor is installed when you run the plan and start a VM in the validation process. For more information see Carbon Black Launcher and configure a recovery plan for ransomware recovery.
If you do not want the sensor installed automatically, see Manual Sensor Installation.