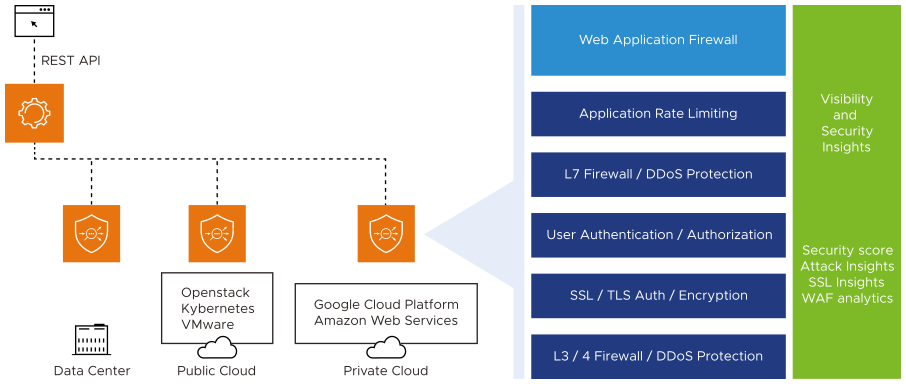
The NSX Advanced Load Balancer leverages software-defined architecture and its strategic location on the network to gain real-time application insights. The built-in WAF solution provides application security and networking teams with an elastic and analytics-driven solution, that scales and simplifies policy customization and administration through central management.
The NSX Advanced Load Balancer WAF plays an integral role in a defense-in-depth strategy that performs comprehensive threat analysis, mitigates risk, provides zero-day protection against unpublished exploits and optimizes application security.
WAF gives administrators an important point of security enforcement and intelligence. WAF protects web applications from common vulnerabilities identified by Open Web Application Security Project (OWASP), such as SQL Injection (SQLi) and Cross-site scripting (XSS), while providing the ability to customize the rule set for each application.
Core Security |
Threat Detection |
Application Protection |
|---|---|---|
OWASP Top 10 attack protection, including HTTP validation, injection, data leakage protection, automated attack blocking, and application-specific security. |
Accept-Listing rules that allow bypassing WAF for certain request properties. For example, to allow the DAST scanner IPs from WAF inspection, to exclude internal IP addresses from WAF inspection or to bypass WAF for all POST requests. |
Learning mode for application behavior and structure helps profile applications, inform decisions and automatically create positive security rules. |
Guided false positive mitigation with customizable paranoia levels that control the strictness of the policy based on the logs and analytics. |
Positive security for allowed application behavior to block anomalies. Positive model engine is called before the signature engine, reducing false positives and the time required to reach a decision about the validity of the request. |
Per-app deployment for precision protection of specific applications with different security policy levels while ensuring application performance. |
Rate-limiting per app to limit L3/L4 and L7 traffic based on parameters such as Client IP, URL and Path. |
Signatures protection against known threats through a denylist approach by analyzing every part of the incoming and outgoing requests against SQLi, XSS and other threats based on Core Rule Set (CRS). |
On-demand autoscaling to elastically scale the number of WAF instances and application servers to handle unpredictable traffic without impacting performance. |
Point-and-click policy with central control and ease of use by enabling users to create custom policies quickly and efficiently. |
Application analytics for WAF events based on historical trend information and real-time visibility into ongoing operations, application behavior analysis, and attack patterns. |
|
RBAC support to control write access to WAF profiles and policies and read access to applications, pools, and clouds. |
Feature List
The following sections describe WAF features under three broad categories:
For a concise list of all WAF features, see What are the features provided as part of WAF? in the FAQ section.
Web Security and Application Attack Protection
OWASP Top 10 attack protection, including HTTP validation, injection, data leakage protection, automated attack blocking, and application-specific security.
Positive security rules check the application traffic for allowed application behavior and block anomalous behavior. This engine is called before the signature engine, thereby reducing false positives and allowing for a quicker decision to be made about the validity of the request.
Application behavior and structure is learned and can later be reused for other analytics and to automatically create positive security rules through Application Learning.
The Allowlist defines rules for bypassing WAF for some given request properties. For example, to allow the DAST scanner IPs from WAF inspection, to exclude internal IP addresses from WAF inspection or to bypass WAF for all POST request to /upload.php, and so on.
IP geolocation
HTTP RFC compliance
File upload scanning
DAST import
Scripting for application logic flaws
API protection for JSON XML
In addition to protecting traditional HTTP Applications, WAF can also protect APIs or AJAX applications by analyzing JSON or XML payloads
Support for multiple CRS versions
Rate-limiting per application
Brute force attack protection
Basic DDOS protection
HTTP Security policies
L3-L7 security rules, including ACLs
Administration and Configuration
WAF admin RBAC support provides granular Role-Based Access Control (RBAC). Users can have write access to WAF Profiles and Policies and read access to application virtual services, pools, clouds and so on.
SSH and Web GUI access for administration.
The NSX Advanced Load Balancer platform is 100% REST API-based. So, deployment can be fully automated and all functionalities can be included in a CI/CD pipeline.
Customizable error codes and error pages.
Per-app deployment for precision protection of specific applications with different security policy levels while ensuring application performance.
Easy to deploy rules.
Easy-to-create custom rules that can be added for application-specific use cases or any other custom requirement that might arise.
Point-and-click simplicity for policies with central control.
Elastic scale with high performing, automatic scale-out architecture.
Easy to deploy exclusions.
Guided false positive mitigation with customizable paranoia levels that control the strictness of the policy based on the logs and analytics.
Built-in event and alert mechanisms.
SNMP support.
NSX Advanced Load Balancer Cloud Services provide live security threat updates, such as IP reputation, signatures and more updates are sourced from industry-leading threat analysis companies and curated through the NSX Advanced Load Balancer Cloud Services.
Logs and Analytics
Application analytics for WAF events based on historical trend information and real-time visibility into ongoing operations, application behavior analysis, and attack patterns.
Granular security insights on traffic flows and rule matches to create precise and custom policies.
Comprehensive log collection that includes pinpoint analysis of all security incidents that were blocked by WAF.
Architecture
The NSX Advanced Load Balancer WAF is built on the core design principles shown below to ensure that WAF is a simple yet comprehensive security solution.
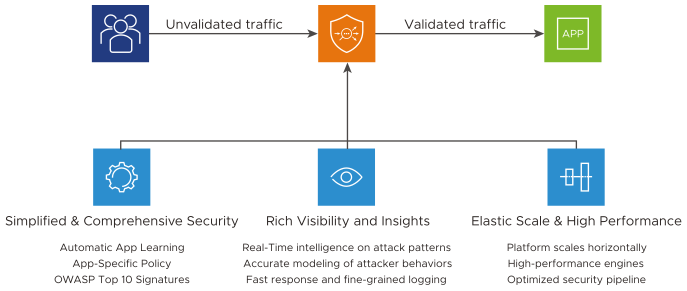
For information on WAF Process Flow, see What is WAF processing flow? in the FAQ section.

