To benefit all the NSX Security features, you must deploy the NSX Management Plane in an on-premises environment.
After NSX-T is installed, configure the system for different security features. The workflow in this guide includes minimal deployment and configuration instructions required to set up the security features. For more detailed instructions for each feature, see NSX-T Data Center Installation Guide and NSX-T Data Center Administration Guide.
NSX Firewall – for all Deployment Options
NSX Firewall provides different security controls like Distributed Firewall, Distributed IDS/IPS, Distributed Malware Prevention, and Gateway Firewall as an option to provide firewalling to different deployment scenarios.
A typical data center can have different workloads like VMs, Containers, Physical Server, and a mix of NSX managed and non-managed workloads. These workloads can have a combination of a VLAN-based network or an NSX-based overlay network.
The following diagram summarizes different data center deployment scenarios and associated NSX firewall security controls, which best fits the design. You can use the same NSX Manager as a single pane of glass to define the security policies for all these different scenarios using different security controls.
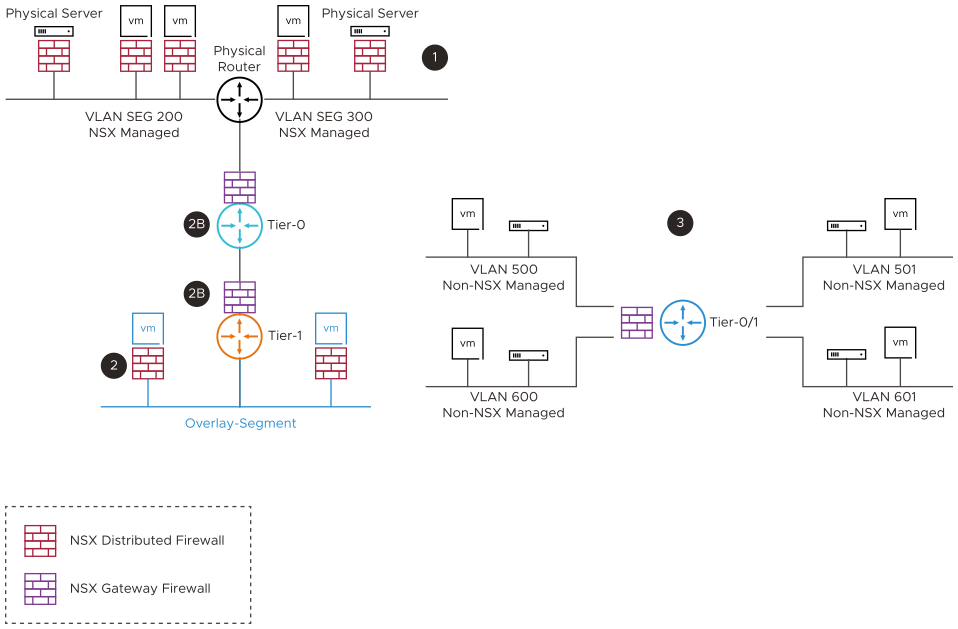
- NSX Managed Workloads with Standard VLAN based Networking:
NSX distributed firewalling capability can be used to protect NSX managed VMs and Physical Server workloads.
- NSX Managed Workloads with NSX Overlay for Networking:
- NSX Distributed Firewall can be used to protect NSX managed VMs, Containers (using NSX container plug-in), and Physical Server workloads from East-West traffic perspective. This can be used for Zone-segmentation, Application-segmentation, and Micro-segmentation with both L3-L7 firewalling and IDS/IPS capabilities.
- NSX Gateway Firewall can be used as inter-tenant/zone firewall from North-South perspective, along with the distributed firewall.
- Non-NSX Managed Workloads on Traditional VLAN based Network:
NSX gateway firewalling capability can provide the inter VLAN routing and firewalling. The Service Interface on NSX tier-1 gateway or external interface on the tier-0 gateway is used as a gateway and firewall for all the non-NSX managed VLAN workloads.
Basic Deployment Workflow
| Action | Description | Details |
|---|---|---|
| Deploy the NSX Management Plane |
|
Deploying NSX Management Plane |
| Configure for NSX Distributed Security |
|
Preparing for Distributed Security |
| Configure for NSX Gateway Security |
|
Preparing For Gateway Security |
This guide does not cover advanced features supported by NSX Firewall. For more detailed instructions for each feature, see NSX-T Data Center Administration Guide.