How do I import a third-party security scan as an alternative to running an assessment
As an alternative to running an assessment on a vulnerability policy, Tanzu Salt supports importing security scans generated by a variety of third-party vendors.
Instead of running an assessment on a vulnerability policy, you can import a third-party security scan directly into Tanzu Salt and remediate the security advisories it identified using Tanzu Salt. See How do I run a vulnerability assessment for more information about running a standard assessment.
Tanzu Salt supports third-party scans from:
- Tenable
- Rapid7
- Qualys
- Kenna Security
- Carbon Black
When you import a third-party scan into a security policy, Tanzu Salt matches your minions to the nodes that were identified by the scan.
Note:
By default, all Tanzu Salt users can access the Connectors workspace. However, permission to run Vulnerability Vendor Import, as well as a Tanzu Salt license, are required for a user to successfully import vulnerabilities from a connector.
The security policy dashboard lists the advisories identified by the third-party scan, as well as whether each advisory is supported or unsupported for remediation.
Note:
If the size of your export file is large, you might need to scan a smaller segment of nodes in your network with your third-party tool. Alternatively, you could import large scans using the command line interface (CLI) or API.
After importing your scan, the policy displays a summary that you can toggle between two views:
- Supported vulnerabilities and unsupported vulnerabilities. Supported vulnerabilities are the advisories that are available for remediation using Tanzu Salt.
- Unsupported vulnerabilities are advisories that cannot be remediated using Tanzu Salt.
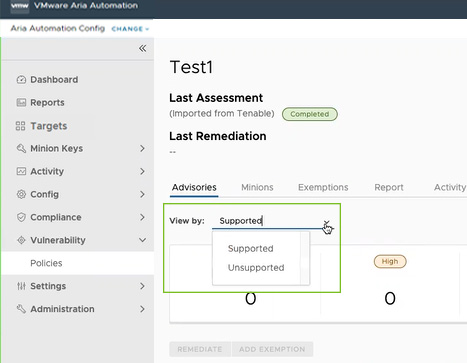
Note:
This view selector is only available for vendor imported data. Data created using Automation for Secure Hosts content won’t show this view selector.
Configuring a third-party connector
Before you can import a third-party security scan you must configure a connector. The connector must first be configured using the third-party tool’s API keys.
To configure a Tenable.io connector
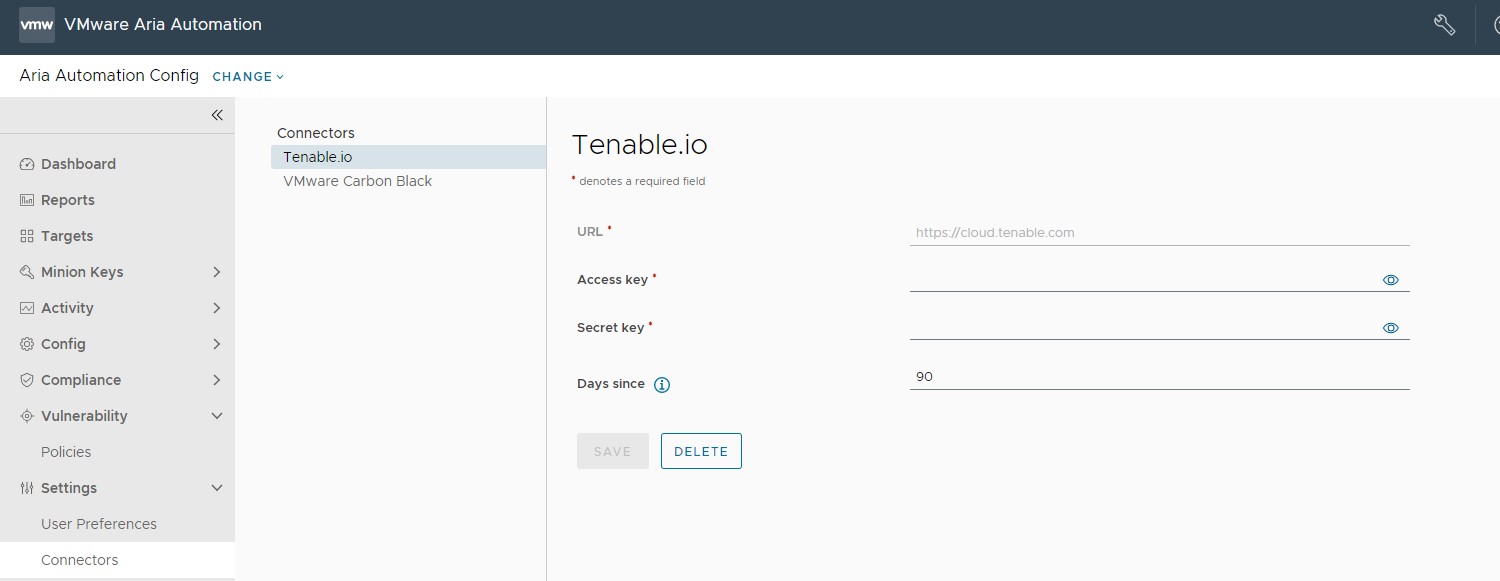
To configure a Tenable.io connector, navigate to Settings > Connectors > Tenable.io, enter the required details for the connector, and click Save.
| Connector field | Description |
|---|---|
| Secret Key and Access Key | Key pair required to authenticate with the connector API. For more information on generating your keys, see the Tenable.io documentation. |
| URL | Base URL for API requests. This defaults to https://cloud.tenable.com. |
| Days since | Query Tenable.io scan history beginning this number of days ago. Leave blank to query an unlimited period of time. When you use a connector to import scan results, Tanzu Salt uses the most recent results per node available within this period. |
Note:
To ensure your policy contains the latest scan data, make sure to rerun your import after each scan. Tanzu Salt does not poll Tenable.io for the latest scan data automatically.
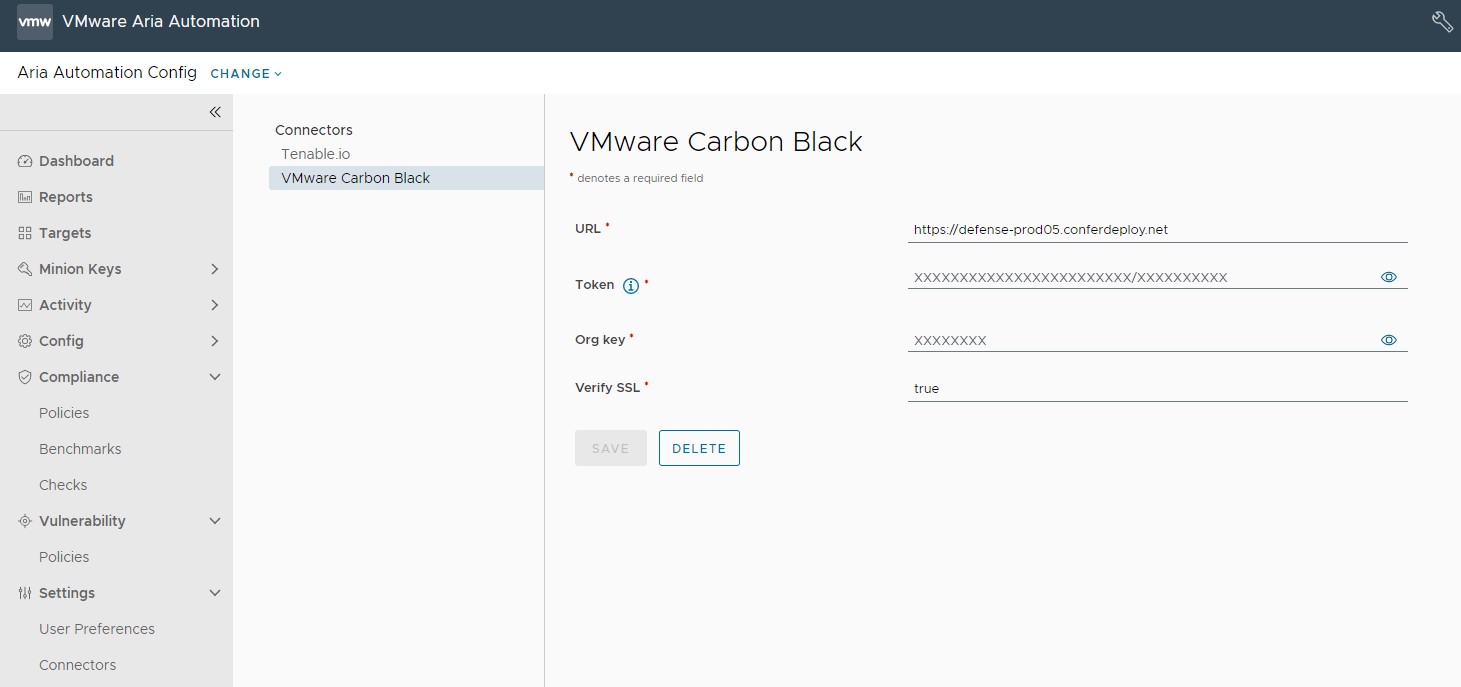
To configure a Carbon Black connector (Windows only)
To configure a Carbon Black connector, you need to enable the Device Read permission in Carbon Black Cloud and create an API token code. For more information on creating an API token code, see Vulnerability Assessment API.
Note:
Automation for Secure Hosts only supports connectors and scans from VMware Carbon Black Cloud. Automation for Secure Hosts only uses the ipv4 and Carbon Black device for matching and the risk_meter_score for display. No other information is used.
Before you can configure a Carbon Black connector, you must first set up a Windows Minion Carbon Black sensor kit environment.
To set up a Carbon Black sensor kit environment:
- Launch the Tanzu Salt environment and deploy a Windows server.
- Install the Salt minion on the Windows server. For more information see, Salt Minion Installation.
- Accept the master keys in Tanzu Salt, and the minion keys from Tanzu Salt or the Salt Master.
- Install the Carbon Black sensor kit on the Windows minion. For more information, see Installing Sensors on VM Workloads.
- In Automation for Secure Hosts, define a policy with a target group that contains the Windows minion.
- After the Tanzu Salt VMan ingestion is complete, sync the Tanzu Salt Carbon Black module from the Salt master by running these commands:
salt mywindowsminion saltutil.sync_modules saltenv=sse. - On the Windows minion, set the Carbon Black device grain by running the
salt mywindowsminion carbonblack.set_device_grain.
After setting up a Carbon Black sensor kit environment, you can then configure your Carbon Black connector in Tanzu Salt by navigating to Settings > Connectors > VMware Carbon Black. Enter the required details for the connector, and click Save.
| Connector field | Description |
|---|---|
| URL | URL for API requests. |
| Token and Org Key | Key pair required to authenticate with the connector API. |
| Verify SSL | Default is set to true. |
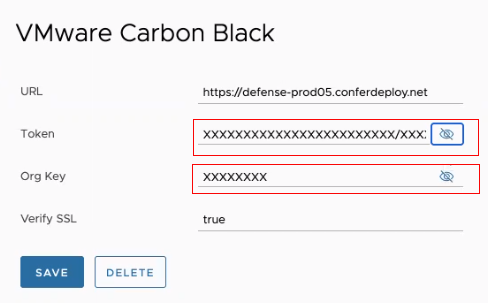
Note:
If you a delete a VMware Carbon Black connector, these fields are populated with ‘xxxx’ characters. This is to maintain the token key format of xxxxxxxxxxxxxxxxxxxxxxxx/xxxxxxx.
- Click Targets and select either All Minions or a specific minion for a policy target group.
- Click Run Command and run these commands:
saltutil.sync_all,carbon_black.set_device_grain, andsaltutil.refresh_grains.
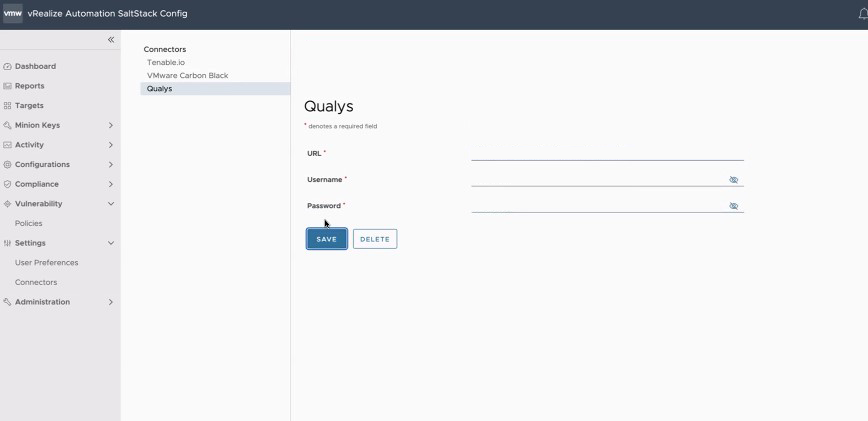
To configure a Qualys connector
To configure a Qualys connector, navigate to Settings > Connectors > Qualys, enter the required details for the connector, and click Save.
The URL, Username, and Password credentials are provided by Qualys.
How do I import a third-party scan
You can import a third-party scan from a file, from a connector, or by using the command line.
Prerequisites
Ensure that you have configured your third-party connector in the Connectors UI.
Procedure
-
In your third-party tool, run a scan and make sure to pick a scanner that is in the same network as the nodes you want to target. Then, indicate the IP addresses you want to scan. If you are importing a third-party scan from a file, export the scan in one of the supported file formats (Nessus, XML, or CSV).
-
In Tanzu Salt, make sure you have downloaded Tanzu Salt content.
-
In the Tanzu Salt workspace, create a security policy targeting the same nodes that were included in the third-party scan. Ensure the nodes you scanned in your third-party tool are also included as targets in the security policy. See How do I create a vulnerability policy for more information.
Note:
After exporting your scan and creating a policy, you can import your scan by running theraas third_party_import “filepath” third_party_tool security_policy_namecommand. For example,raas third_party_import “/my_folder/my_tenable_scan.nessus” tenable my_security_policy. It is recommended to import your scan using the CLI if the scan file is especially large. -
In the policy dashboard, click the Policy Menu drop down arrow and select Upload Vendor Scan Data.

-
Import your scan:
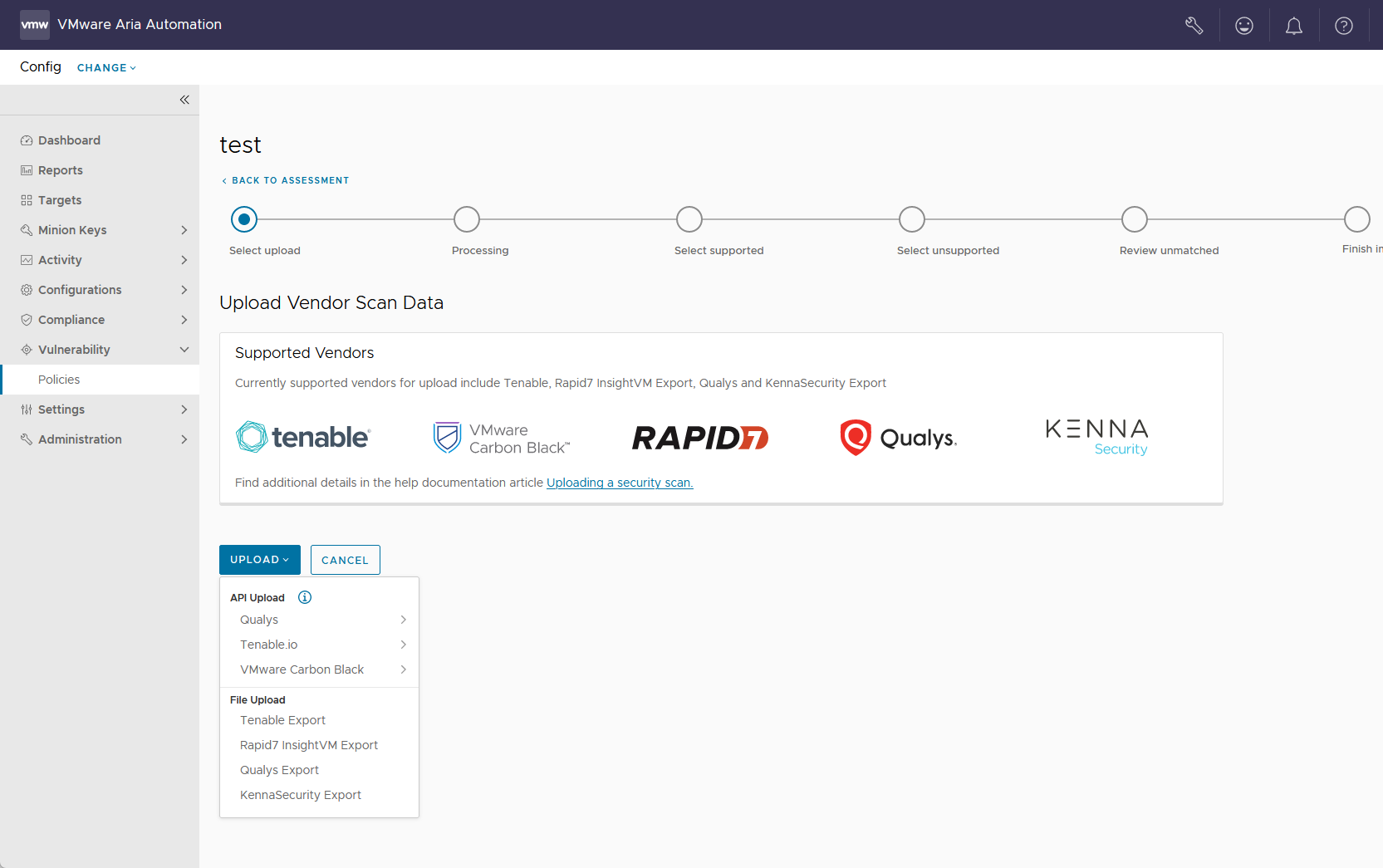
- If importing your scan from a file, select Upload > File Upload and select your third-party vendor. Then select the file to upload your third-party scan.
- If importing your scan from a connector, select Upload > API Upload and select the third-party. If no connectors are available, the menu directs you to the connectors settings workspace.
The import status timeline shows the status of your import as Tanzu Salt maps your minions to the nodes that were identified by the scan. Depending on the number of advisories and affected nodes, this process might take some time.
Note:
If you select Qualys as a third-party vendor, all scans must be in XML format. No other formats are supported. -
On the Select supported page, select the supported advisories that you want to include as part of your file import.
-
On the Select unsupported page, select the unsupported advisories that you want to include as part of your file import.
-
Review unmatched advisories for advisories that do not match a host or minion. As a result they cannot be remediated through Tanzu Salt.
-
Click Next and review a summary of what will be imported into the policy.
-
Click Finish Import to import your scan.
Results
The selected advisories are imported to Tanzu Salt and appear as an assessment in the policy dashboard. The policy dashboard also displays Imported from under the policy title to indicate that the latest assessment was imported from your third-party tool.
Note:
Assessments are only run when the scan is imported. Imported scans assessments can not be run on a schedule.
What to do next
You can now remediate these advisories. See How do I remediate my advisories for more information.