You can deploy the patch by using the CLI or the VMware Telco Cloud Automation UI.
Deploy the Patch Bundle on your Cluster Using the CLI
- Login to the Deployment Host and create a directory called Patch under /root directory.
- Download the patch bundle in the Deployment Host under the /root/patch directory.
- Extract the downloaded bundle and installer. For procedure, see Extract the Downloaded Package and Installer topic.
- Navigate to the deployment directory where the patch was extracted.
cd $TCSA_WORK_SPACE/tcx-deployer/scripts/deployment/
The deploy.settings file in the Patch must be updated with the values from the deploy.settings file which was used to deploy the Base GA build.
- Download and launch the Deployment Container. For procedure, see Download and Launch the Deployment Container section.
Note: Ensure that you set workspace to the following directory path.
export TCSA_WORK_SPACE=/root/patch
- Run ./tcx_app_deployment.sh from the Deployment Container.
Manually check the VMware Telco Cloud Service Assurance Patch deployment status using the following command:
root [ ~/tcx-deployer/scripts ]# kubectl get tcxproduct
Alternatively, you can run the following command to check the Patch deployment status:root [ ~/tcx-deployer/scripts ]# kubectl get apps
For all the apps, the reconcilation status must be successful.
- To verify if the correct image is selected, run the following command:
kubectl describe app <app name>
The image parameter and image tag must point to the patchedimgpkgbundles with their corresponding tags.
Note: After the patch is deployed, you can view the patch versions in the
About page of VMware Telco Cloud Service Assurance UI.
Deploy the Patch Bundle on your Cluster Using the VMware Telco Cloud Automation UI
To deploy the patch using the VMware Telco Cloud Automation UI, perform the following steps:
- Download the patch bundle in the Deployment Host under the /root/patch directory.
- Extract the downloaded bundle and installer. For procedure, see Extract the Downloaded Package and Installer topic.
- Download and launch the Deployment Container. For procedure, see Download and Launch the Deployment Container section.
Note: Ensure that you set workspace to the following directory path.
export TCSA_WORK_SPACE=/root/patch
- Run the installer script to push new artifacts to the registry.
root [ ~/tcx-deployer/scripts ]# python3 tcx_install.zip initialize-all-and-push-artifacts --initialize-cluster --cloud tca --product tcsa --kubeconfig /root/.kube/tca-test --artifacts-path /root/tcx-deployer --registry-url <your-registry-url> --registry-username <your-registry-username> --registry-password <your-registry-password> --registry-ca-certs /root/tcx-deployer/haas-wgt1-97-120.eng.vmware.com.crt
- Run the merge-product-yaml-files.sh script as described in Generate a Single Merged YAML File required for patch deployment and copy the resulting merged_yamls.yaml file to your local machine.
Note: Retain the same footprint value used during initial deployment.
- Update the values for the parameters in the merged_yamls.yaml which is generated in step 5 as shown in the following screenshot:
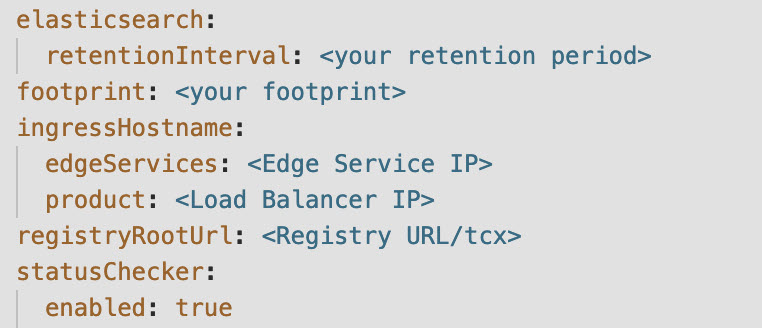
Set them to the same values used during initial VMware Telco Cloud Service Assurance deployment.
- ingressHostname.product=<LoadBalancerIP>
- registryRootUrl=<your-registry-url/your-project-name/tcx>
- Update the statusChecker.enabled parameter. The default value is
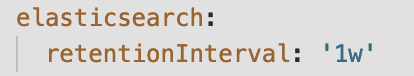
true. Set the value asfalse. - Update the retentionInterval value with the same value used during initial CNF instantiation. In the following screenshot, retention interval is set to 1w as an example.
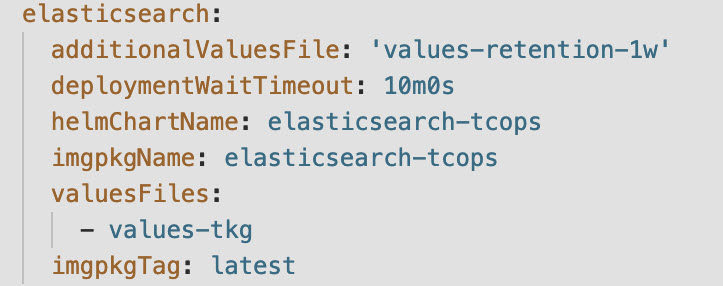
- Update the additionalValuesFile parameter in the merged_yamls.yaml file based on the retention interval value. The following screenshot is an example of a demo footprint.
- Update the following parameters in the merged_yamls.yaml file to the required footprint.
- footprint
- appSpecs.adminApi.helmOverrides.productInfo.footPrint
Note: Based on the footprint size of deployment, update the value for footprint.
- Copy the CSAR file from the patch bundle.
- After the CSAR is copied, launch VMware Telco Cloud Automation, navigate to and click Onboard Network Function. Onboard the CSAR files that are copied.
- Navigate to , click the three dots against the CNF to upgrade as part of the patch, and select Upgrade.
- In the Upgrade Revision section, select the new CSAR file that you onboarded. For example,
tcsa-upgrade. Click Next.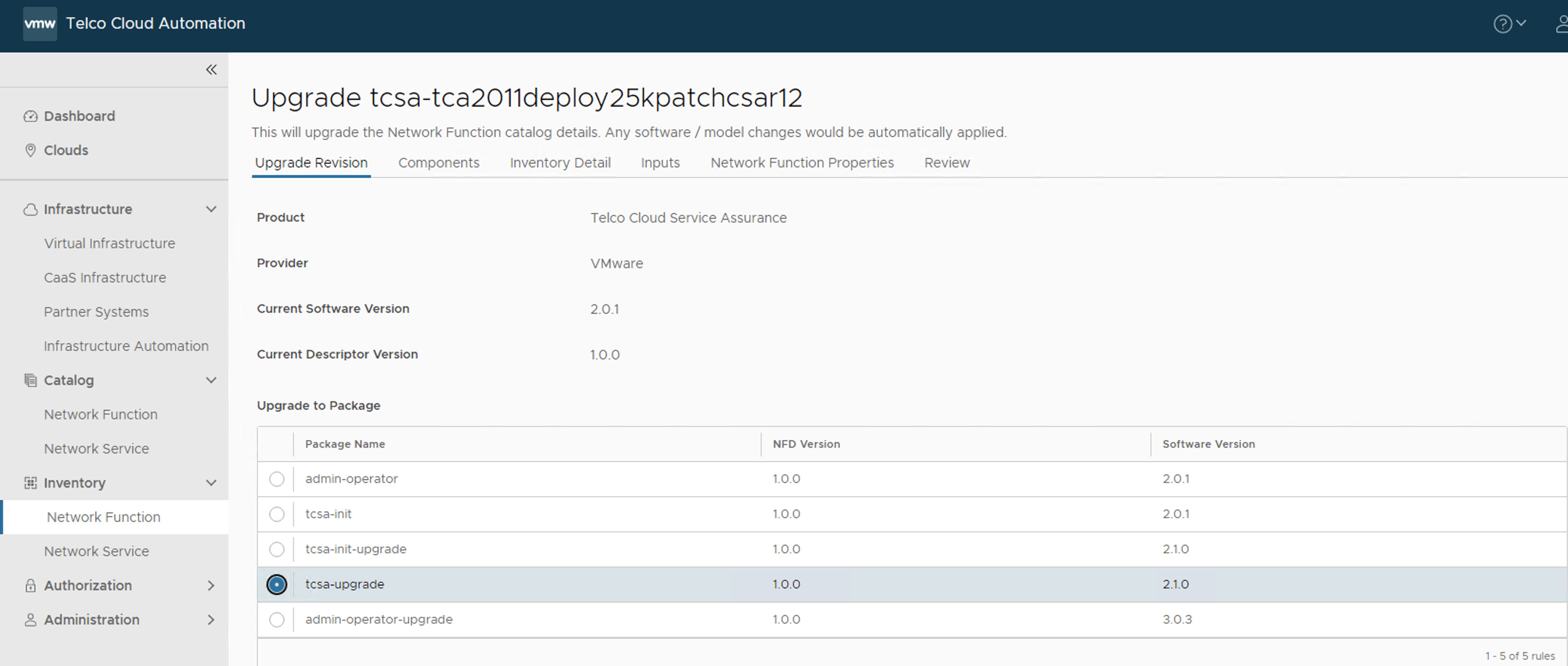
- In the Components section, click Next.
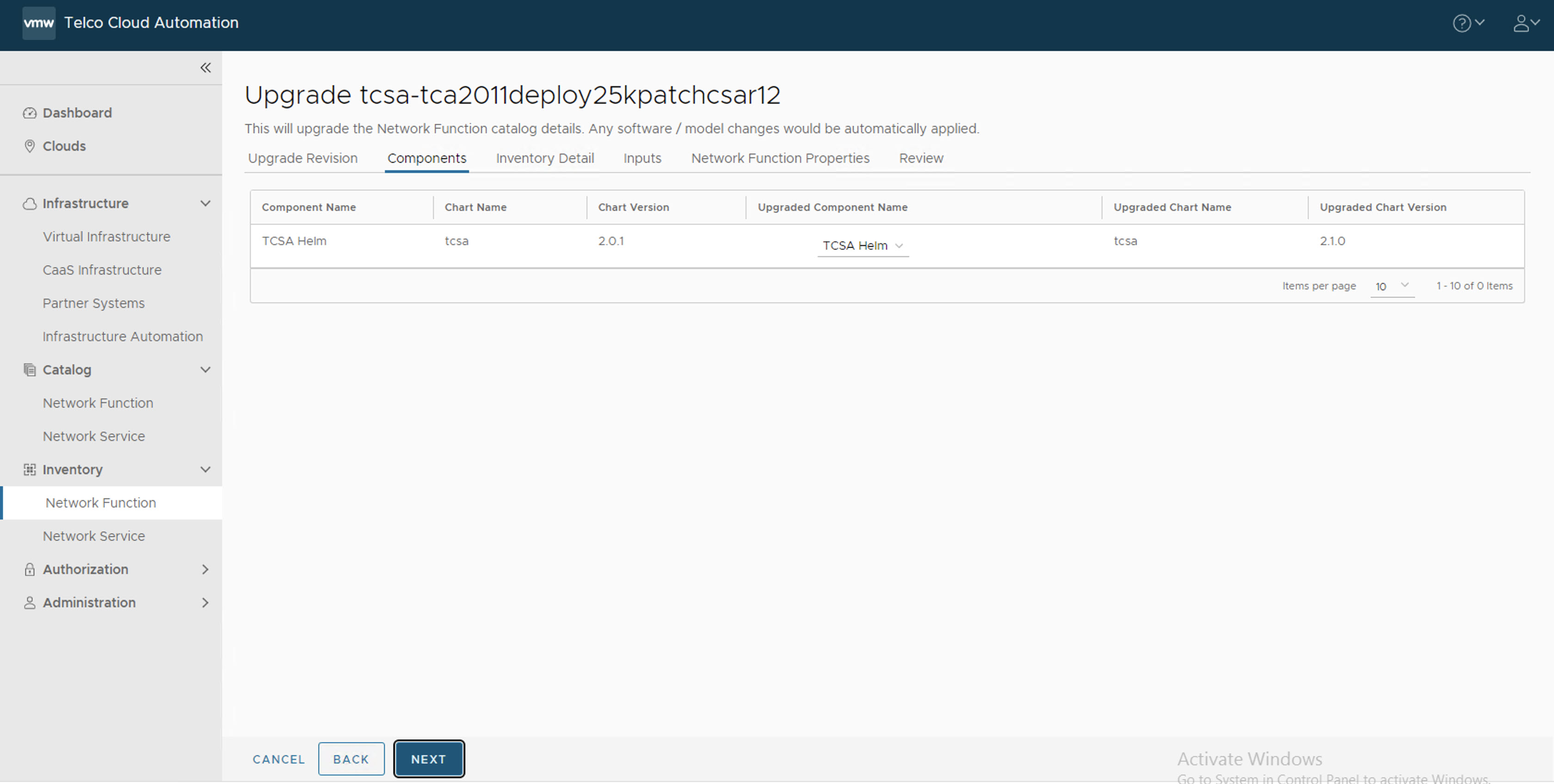
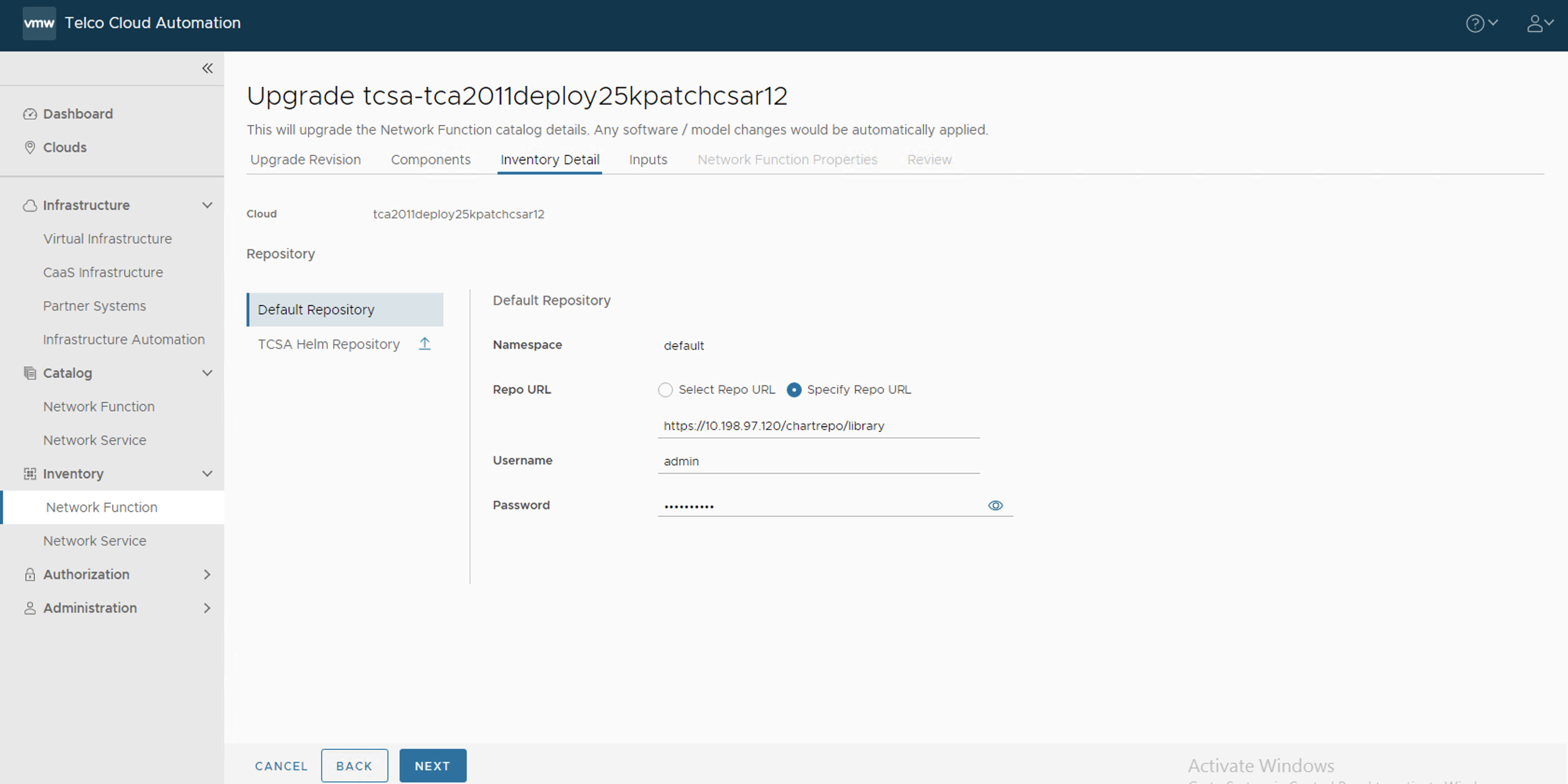
- In the Inventory Detail section, set the Namespace to default and select the default library chart repository, that is, the /chartrepo/library endpoint of the associated registry, and click Next.
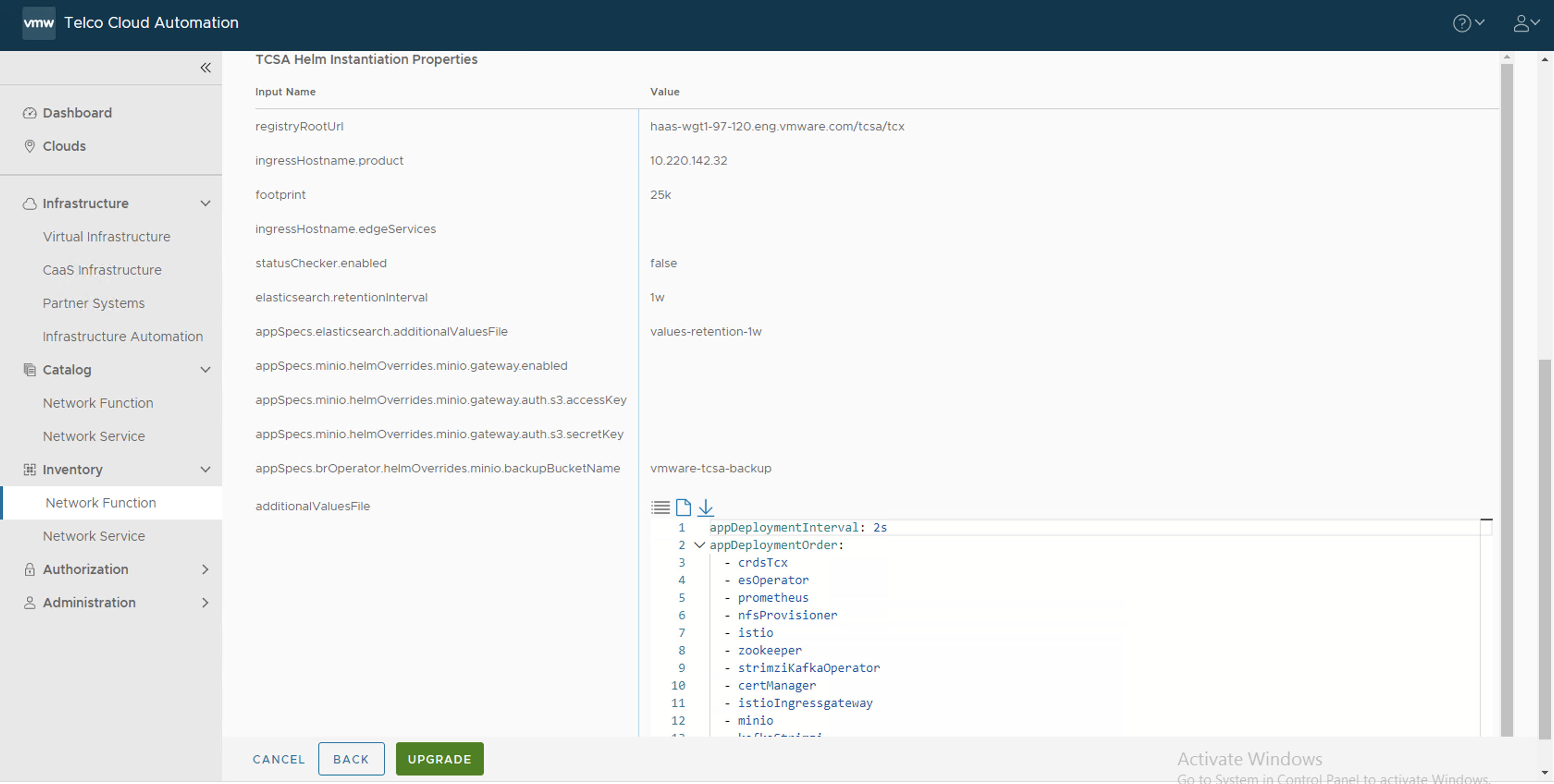
- In the Inputs section, update the following parameters:
- Set registryRootUrl to the same value as the base version.
- Set ingressHostname.product to the same value as the base version.
- Set footprint to the base footprint that you are deploying. For example, demo, 25 K, 50 K, 75 K, 100K, and so on.
- (Optional) Set ingressHostname.edgeServices to the IP address of the base version in case you want to access external Kafka.
- Set statusChecker.enabled to check the status of the
tcsaCNF.Note: The statusChecker.enabled parameter is disabled in VMware Telco Cloud Service Assurance because VMware Telco Cloud Automation does not support CNF timeouts. - Set elasticsearch.retentionInterval to the desired retention period of metrics in Elasticsearch.
Note: By default, the retention interval is 1w. The retention interval values can be 1w, 2w, 3w, 4w, 5w, 4w, or 7w.
- Set appSpecs.elasticsearch.additionalValuesFile to one of the values like values-retention-1w, values-retention-2w, values-retention-3w, values-retention-4w, values-retention-5w, values-retention-6w, or values-retention-7w.
Select the same retention period as elasticsearch.retentioninterval. For example, values-retention-1w for 1 week. This is an additional configuration required to properly configure the retention of metrics in Elasticsearch.Note: Setting the Elasticsearch retention parameters is optional. By default, the retention interval is 1w for elasticsearch.retentioninterval and values-retention-1w for appSpecs.elasticsearch.additionalValuesFile.If you want to store the backup and restore in a AWS cloud, you must enable the following parameters in the VMware Telco Cloud Automation UI:
- appSpecs.minio.helmOverrides.minio.gateway.enabled
- appSpecs.minio.helmOverrides.minio.gateway.auth.s3.accessKey
- appSpecs.minio.helmOverrides.minio.gateway.auth.s3.secretKey
- appSpecs.brOperator.helmOverrides.minio.backupBucketName
- For additionalValuesFile, upload the merged merged_yamls.yaml file.
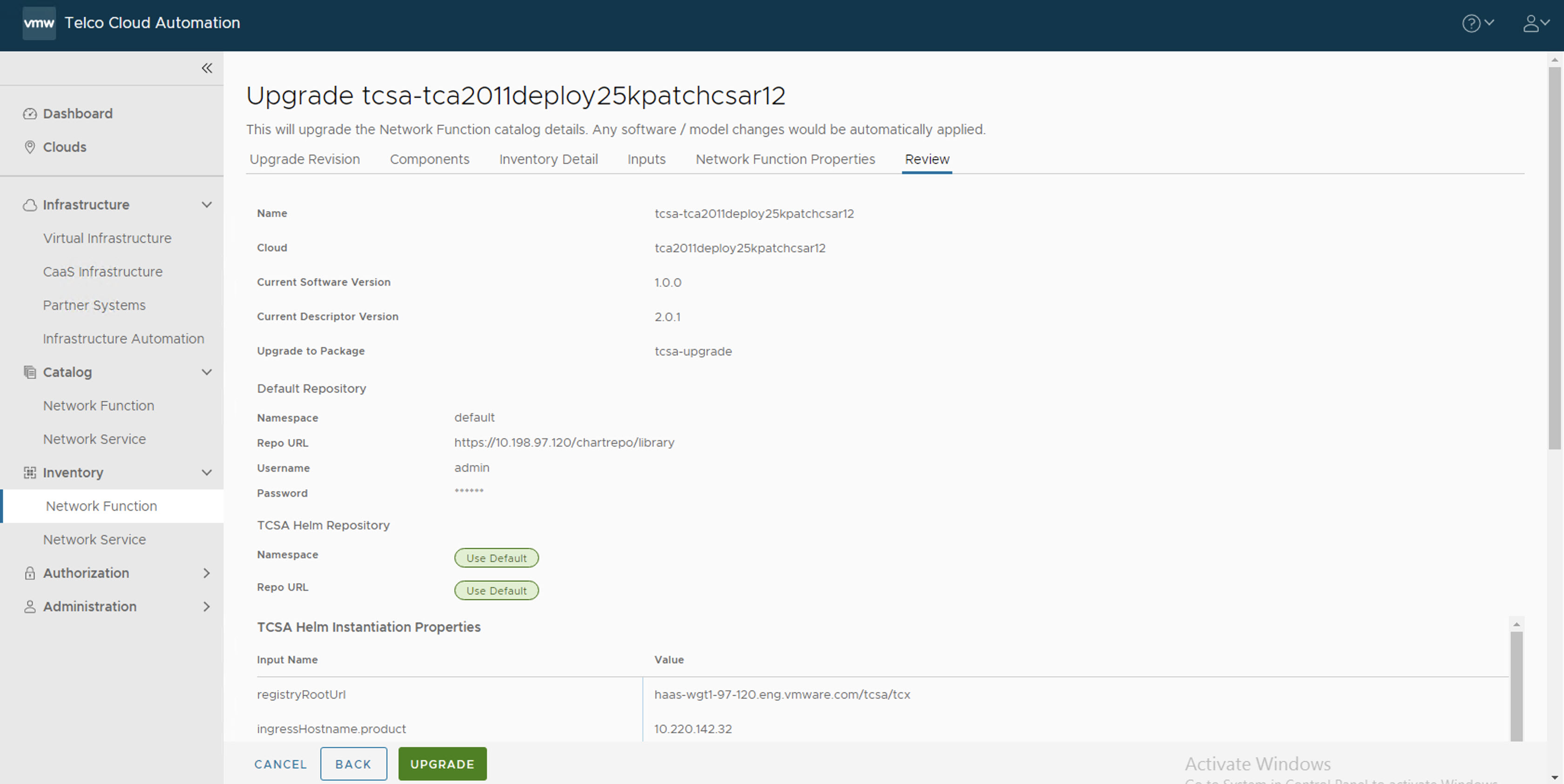
- In the Review section, click Upgrade.
 After the upgrade is successful, you can see the following status message.
After the upgrade is successful, you can see the following status message.root [ ~/tcx-deployer/scripts ]# helm list WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /root/.kube/<your-kubeconfig-file> WARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /root/.kube/<your-kubeconfig-file> NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION admin-opera-779c2-l61eo default 1 2022-11-16 23:34:24.866798654 +0000 UTC deployed admin-operator-3.0.0 3.0.0 tcsa-210-fd171-vazz4 default 3 2022-11-23 09:24:03.236292828 +0000 UTC deployed tcsa-2.1.0-1 0.0.0 tcsa-init-2-9b548-nokze default 1 2022-11-16 10:46:05.325296712 +0000 UTC deployed tcsa-init-2.1.0 1.0.0
Manually check the
VMware Telco Cloud Service Assurance patch rollback status by running the following command from deployment VM:
root [ ~/tcx-deployer/scripts ]# kubectl get tcxproduct OR root [ ~/tcx-deployer/scripts ]# kubectl get apps
For all the apps, the reconcilation status must be successful.
Note: After the patch is deployed, you can view the patch versions in the
About page of VMware Telco Cloud Service Assurance UI.