User Authentication Types
Before you enroll devices, each device user must have an authentic user account recognized by Workspace ONE UEM. The type of user authentication you select depends upon the needs of your organization.
Authentication Proxy
The authentication proxy delivers directory services integration across the cloud or across hardened internal networks. In this model, the Workspace ONE UEM server communicates with a publicly facing Web server or an Exchange ActiveSync Server. This arrangement authenticates users against the domain controller.
PROS
- secure method to proxy integration with AD/LDAP across the cloud.
- end users authenticate with existing corporate credentials.
- lightweight module requires minimal configuration.
CONS
- requires public facing web server or an Exchange ActiveSync server which ties into an AD/LDAP server.
- only feasible for specific architecture layouts.
- less robust solution than VMware Enterprise Systems Connector.
- cannot be used for Workspace ONE Direct Enrollment.
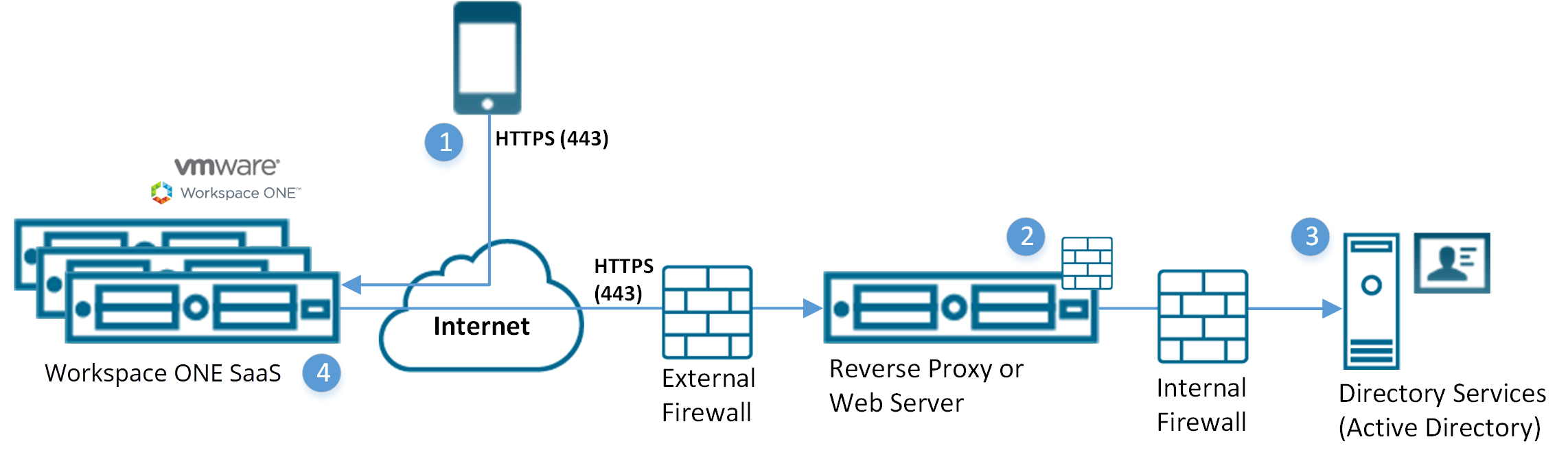
- Device connects to Workspace ONE UEM to enroll device. User enters their directory services user name and password.
- User name and password encrypted during transport.
- Workspace ONE UEM does not store the user’s directory services password.
- Workspace ONE UEM relays the user name and password to a configured Authentication Proxy endpoint that requires authentication (for example, Basic Authentication).
- The user’s credentials validate against the corporate directory services.
- If the user credentials are valid, the Workspace ONE UEM server enrolls the device.
Active Directory with LDAP Authentication and VMware Enterprise Systems Connector
The Active Directory with LDAP authentication and VMware Enterprise Systems Connector provides the same functionality as traditional AD & LDAP authentication. This model functions across the cloud for Software as a Service (SaaS) deployments.
PROS
- End users authenticate with existing corporate credentials.
- Requires no firewall changes, as communication initiates from the VMware Enterprise Systems Connector within your network.
- Transmission of credentials encrypts securely.
- Offers secure configuration to other infrastructure such as BES, Microsoft ADCS, SCEP, and SMTP servers.
- Compatible with Workspace ONE ™ Direct Enrollment.
CONS
- Requires VMware Enterprise Systems Connector to be installed behind the firewall or in a DMZ.
- Requires extra configuration.
SaaS Deployment Model
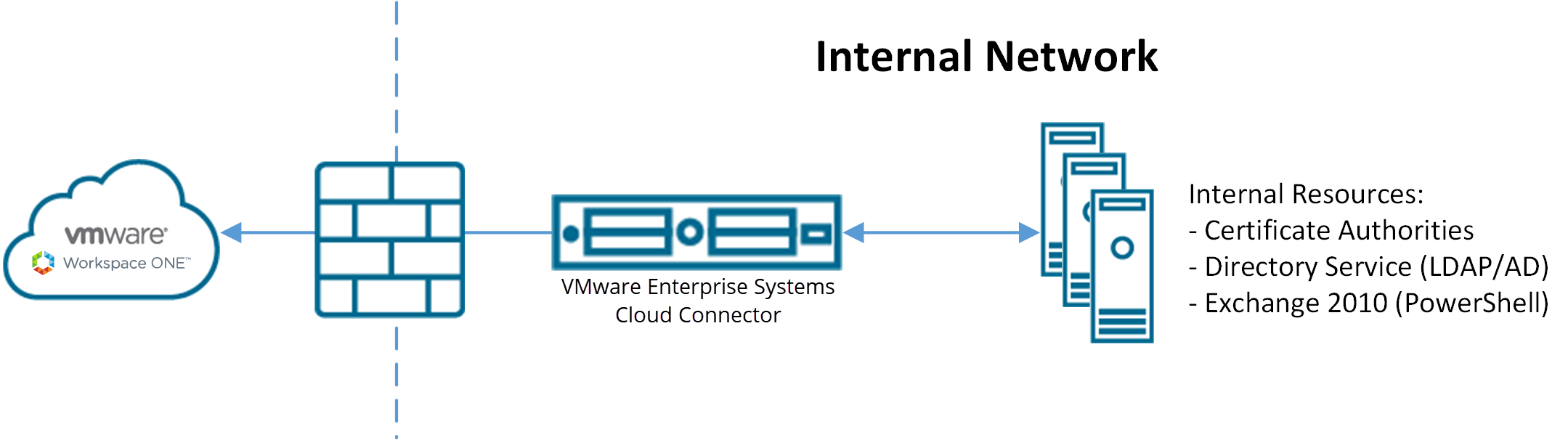
On-premises Deployment Model

SAML 2.0 Authentication
The Security Assertion Markup Language (SAML) 2.0 Authentication offers single sign-on support and federated authentication. Workspace ONE UEM never receives any corporate credentials.
If an organization has a SAML Identity Provider server, use SAML 2.0 integration. Ensure that the Identity Provider returns the objectGUID attribute as part of the SAML response.
PROS
- Offers single sign-on capabilities.
- Authentication with existing corporate credentials.
- Workspace ONE UEM never receives corporate credentials in plain text.
- Compatible with Workspace ONE Direct Enrollment when paired with a SAML Directory User.
- Only Administrators can use multi-domain environments.
CONS
- Requires corporate SAML Identity Provider infrastructure.
- Incompatible with Workspace ONE Direct Enrollment when paired with a SAML Basic User.
-
Configuring SAML with Workspace ONE Access as IDP with Local Basic User feature enabled does not support the authentication of Basic Users.

- Device connects to Workspace ONE UEM for enrollment. The UEM server then redirects the device to the client specified identity provider.
- Device securely connects through HTTPS to client provided identity provider and user enters credentials.
- Credentials encrypted during transport directly between the device and the SAML endpoint.
- Credentials validate against directory services.
- The identity provider returns a signed SAML response with the authenticated user name.
- The device responds back to the Workspace ONE UEM server and presents the signed SAML message. The user authenticates. For more information, see Set Up Directory Services Manually and scroll down to the SAML section.
-
SaaS apps are not available to SAML administrators who authenticate using Workspace ONE Access.
SaaS App Functionality for SAML Admins
SaaS applications, as well as other Workspace ONE Access policies and functions, are unavailable to you if you are a SAML administrator who authenticates using Workspace ONE Access. You will see the following error message when you navigate to the SaaS Apps page.
Check that your administrator account exists in both UEM and IDM systems and that the domain in Workspace ONE UEM exactly matches the same account’s domain in VMware Identity Manager.
To restore SaaS app accessibility, you must log into Workspace ONE UEM using basic authentication and you must also enable Workspace ONE Access at your organization group.
Token-based Authentication
The Token-based authentication offers the easiest way for a user to enroll their device. With this enrollment setting, Workspace ONE UEM generates a token, which places within the enrollment URL.
For single-token authentication, the user accesses the link from the device to complete an enrollment and the Workspace ONE UEM server references the token provided to the user.
For added security, set an expiration time (in hours) for each token. Setting an expiration minimizes the potential for another user to gain access to any information and features available to that device.
You can also decide to implement two factor authentication to take end-user identity verification a step further. With this authentication setting, the user must enter their user name and password upon accessing the enrollment link with the provided token.
PROS
- Minimal work for an end user to enroll and authenticate their device.
- Secure token use by setting expiration.
- User does not need credentials for single-token authentication.
CONS
- Requires either Simple Mail Transfer Protocol (SMTP) or Short Message Service (SMS) integration to send tokens to device.
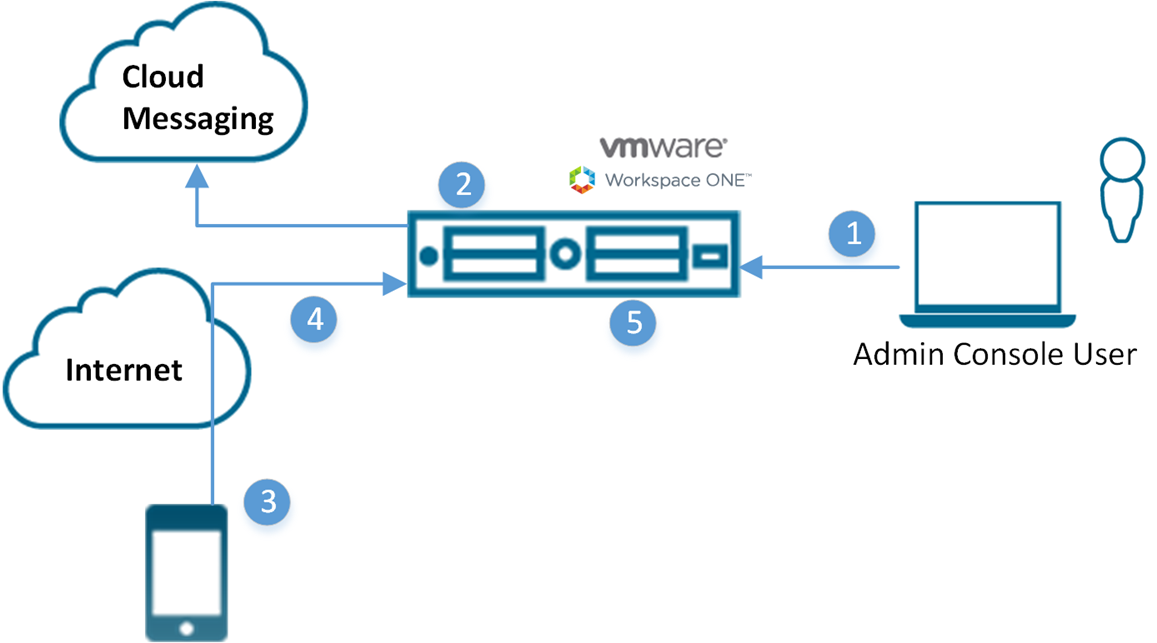
- Administrator authorizes user device registration.
- Single use token generated and sent to user from Workspace ONE UEM.
- User receives a token and navigates to enrollment URL. User receives prompts for token and optionally two-factor authentication.
- Device enrollment process.
- Workspace ONE UEM marks token as expired.
Note: SaaS deployments include SMTP.
Enable Security Types for Enrollment
After Workspace ONE UEM integrates with a selected user security type and before enrollment, enable each authentication mode you allow.
- Navigate to Devices > Device Settings > Devices & Users > General > Enrollment in the Authentication tab.
-
Select the appropriate check boxes for the Authentication Mode setting.
Setting Description Add Email Domain This button is used for setting up the Auto-Discovery Service to register email domains to your environment. Authentication Mode(s) Select the allowed authentication types, which include:
* Basic – Basic user accounts (ones you create manually in the UEM console) can enroll.
* Directory – Directory user accounts (ones that you have imported or allowed using directory service integration) can enroll. Workspace ONE Direct Enrollment supports Directory users with or without SAML.
* Authentication Proxy – Allows users to enroll using Authentication Proxy user accounts. Users authenticate to a web endpoint. Enter Authentication Proxy URL, Authentication Proxy URL Backup, and Authentication Method Type (choose between HTTP Basic and Exchange ActiveSync).Source of Authentication for Intelligent Hub Select the system the Intelligent Hub service uses as its source for users and authentication policies.
* Workspace ONE UEM – Select this setting if you want Hub Services to use Workspace ONE UEM as the source of users and auth policies. When you configure the Hub Configuration page for Hub Services, enter the Hub Services tenant URL.
* Workspace ONE Access – Select this setting if you want Hub Services to use Workspace ONE Access as the source of users and auth policies.
When you configure the Hub Configuration page for Hub Services, enter the Workspace ONE Access tenant URL.
Note: If you enable Workspace ONE Access as the source of authentication for Intelligent Hub, and you use a command line to enroll for staging purposes, then this configuration is bypassed in favor of the credentials supplied in the command line.
For details about Workspace ONE Intelligent Hub, see the VMware Workspace ONE Hub Services Documentation.
For details about Workspace ONE Access, see the VMware Workspace ONE Access Documentation.Devices Enrollment Mode Select the preferred device enrollment mode, which includes:
* Open Enrollment – Essentially allows anyone meeting the other enrollment criteria (authentication mode, restrictions, and so on) to enroll. Workspace ONE Direct Enrollment supports open enrollment.
* Registered Devices Only – Only allowed users to enroll using devices you or they have registered. Device registration is the process of adding corporate devices to the UEM console before they are enrolled. Workspace ONE Direct Enrollment supports allowing only registered devices to enroll but only if registration tokens are not required.Require Registration Token Visible only when Registered Devices Only is selected.
If you restrict enrollment to registered devices only, you also have the option of requiring a registration token to be used for enrollment. This increases security by confirming that a particular user is authorized to enroll. You can send an email or SMS message with the enrollment token attached to users with Workspace ONE UEM accounts.Require Intelligent Hub Enrollment for iOS Select this check box to require iOS device users to download and install the Workspace ONE Intelligent Hub before they can enroll. If deactivated, Web Enrollment is available. Require Intelligent Hub Enrollment for macOS Select this check box to require macOS device users to download and install the Workspace ONE Intelligent Hub before they can enroll. If deactivated, Web Enrollment is available. -
Select Save.
Basic User Authentication
You can use Basic Authentication to identify users in the Workspace ONE UEM architecture but this method offers no integration to existing corporate user accounts.
PROS
- Compatible with any deployment method.
- Requires no technical integration.
- Requires no enterprise infrastructure.
CONS
- Incompatible with Auto Discovery.
- Credentials only exist in Workspace ONE UEM and do not necessarily match existing corporate credentials.
- Offers no federated security or single sign-on.
- Workspace ONE UEM stores all user name and passwords.
- Incompatible with Workspace ONE Direct Enrollment.
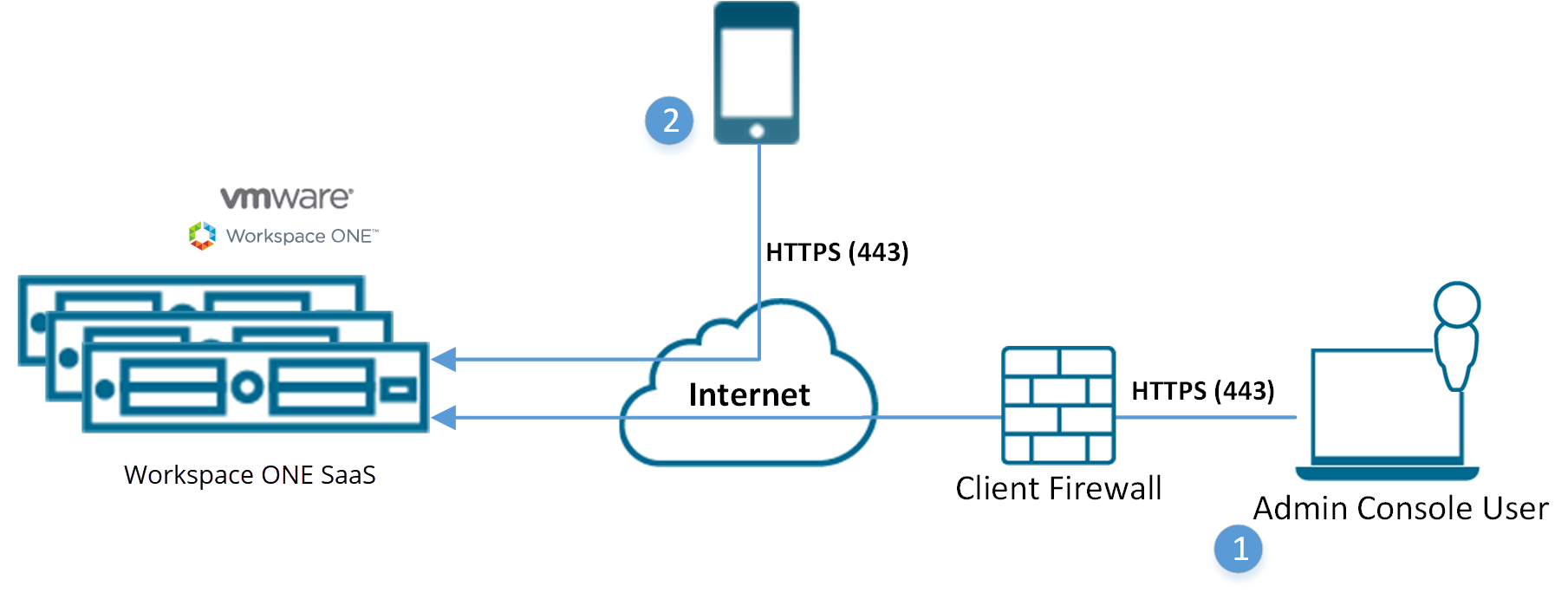
- Console user logs in to Workspace ONE UEM SaaS using local account for authentication (Basic Authentication).
- Credentials encrypt during transport.
- (for example, user name: [email protected], password: Abcd).
- Device user enrolls device using local Workspace ONE UEM account (Basic Authentication) credentials.
- Credentials encrypt during transport.
- (for example, user name: jdoe2, password 2557).
Active Directory with LDAP Authentication
Active Directory (AD) with Lightweight Directory Access Protocol (LDAP) authentication is used to integrate user and admin accounts of Workspace ONE UEM with existing corporate accounts.
PROS
- End users now authenticate with existing corporate credentials.
- Secure method of integrating with LDAP / AD.
- Standard integration practice.
- Compatible with Workspace ONE Direct Enrollment.
CONS
- AD or other LDAP server required.
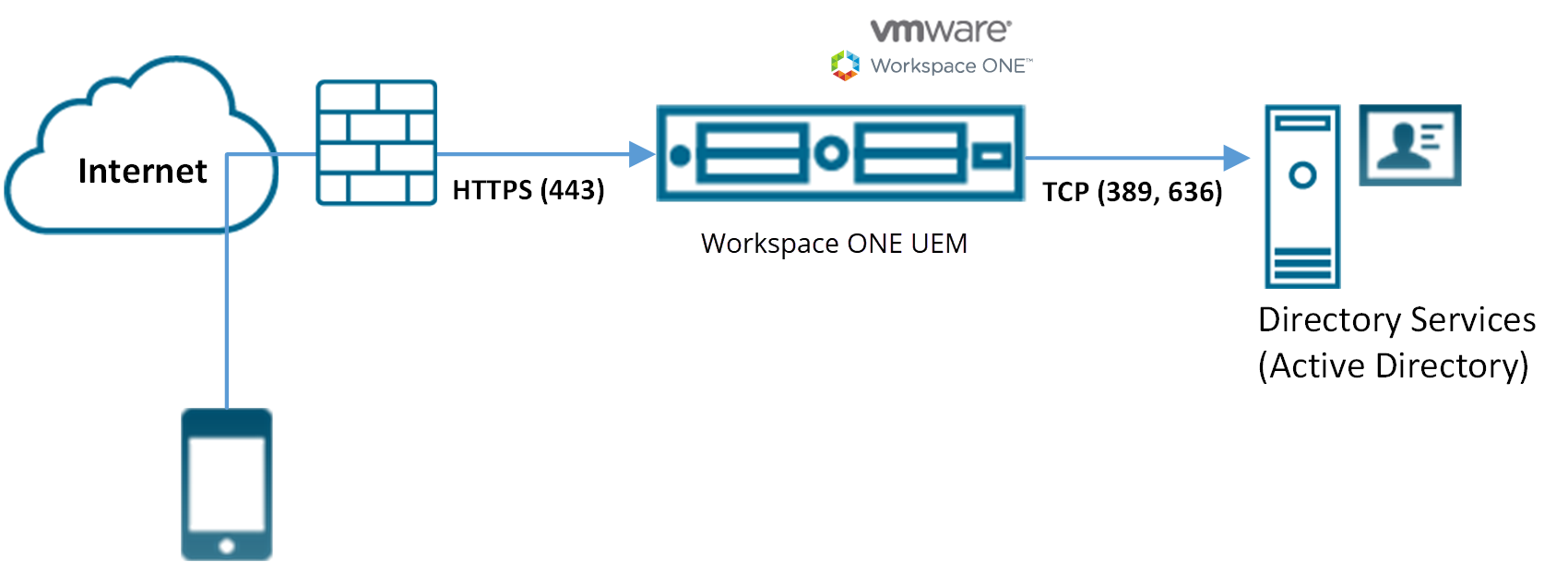
- Device connects to Workspace ONE UEM to enroll device. User enters their directory services user name and password.
- User name and password encrypt during transport.
- Workspace ONE UEM does not store the user’s directory services password.
- Workspace ONE UEM queries directory services through a secure LDAP protocol over the Internet using a service account for authentication.
- The user’s credentials validate against the corporate directory service.
- If the user credentials are valid, the Workspace ONE UEM server enrolls the device.