To connect to Tanzu Kubernetes Grid 2.0 clusters on Supervisor using the Tanzu CLI, register your OIDC provider with Supervisor.
Prerequisites
- Enable Workload Management and deploy a Supervisor instance. See Running TKG 2.0 Clusters on Supervisor.
- Configure an external OpenID Connect identity provider with the Supervisor callback URL. See Configure an External IDP for Use with TKG Service Clusters.
- Get the Client ID, Client Secret, and Issuer URL from the external IDP. See Configure an External IDP for Use with TKG Service Clusters.
Register an External IDP with Supervisor
Supervisor runs as pods the Pinniped Supervisor and the Pinniped Concierge components. Tanzu Kubernetes Grid clusters run as pods the Pinniped Concierge component only. For more information about these components and how they interact, refer to the Pinniped authentication service documentation.
Once you register an external identity provider with Supervisor, the system updates the Pinniped Supervisor and Pinniped Concierge pods on Supervisor and the Pinniped Concierge pods on Tanzu Kubernetes Grid clusters. All Tanzu Kubernetes Grid clusters running on that Supervisor instance are automatically configured with that same external identity provider.
To register an external ODIC provider with Supervisor, complete the following procedure:
- Log in to the vCenter Server using the vSphere Client.
- Select .
- Click the plus sign to begin the registration process.
- Configure the provider. See OIDC Provider Configuration.
Figure 1. OIDC Provider Configuration 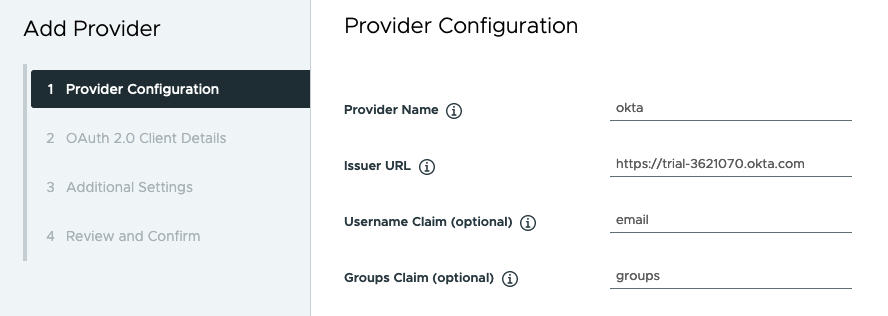
- Configure OAuth 2.0 client details. See OAuth 2.0 Client Details.
Figure 2. OAuth 2.0 Client Details 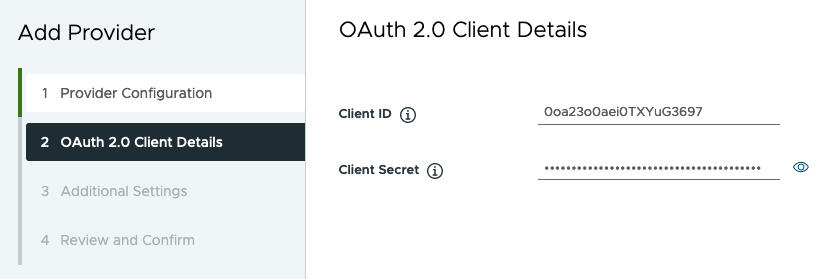
- Configure additional settings. See Additional Settings.
- Confirm provider settings.
Figure 3. Confirm Provider Settings 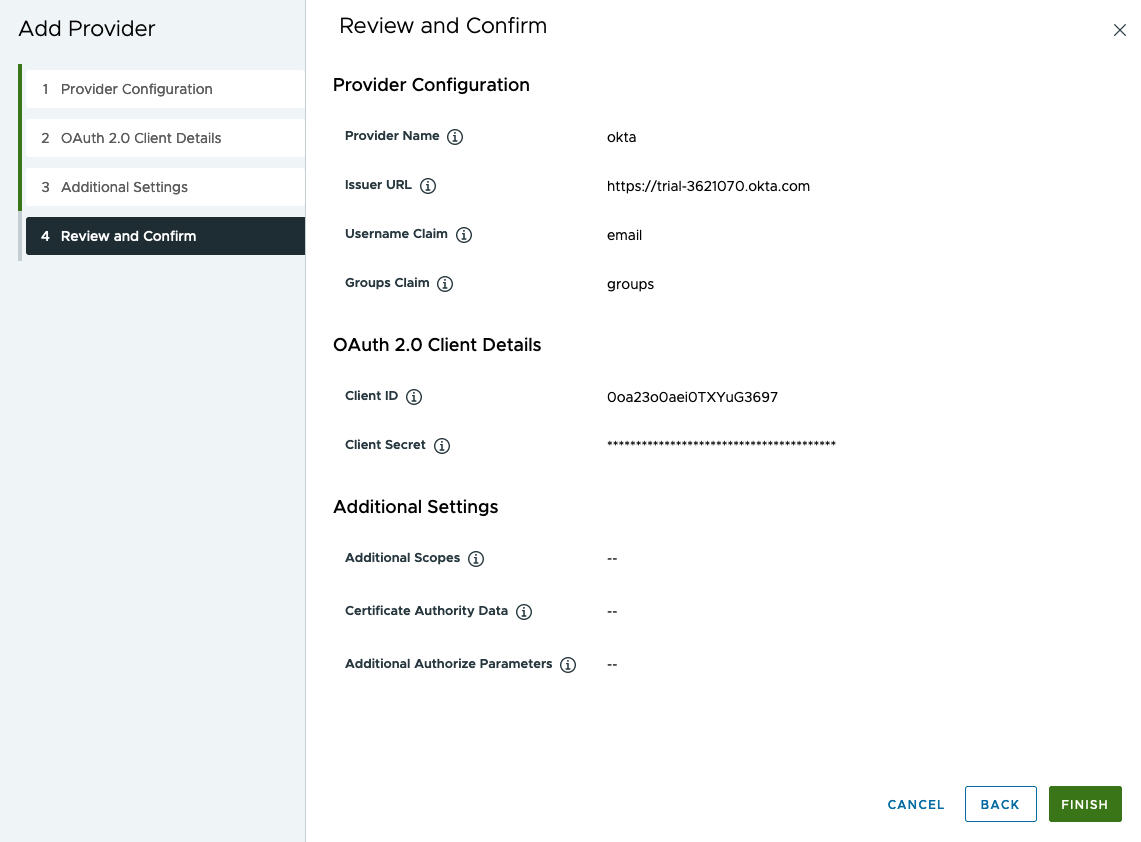
- Click Finish to complete the OIDC provider registration.
OIDC Provider Configuration
Refer to the following provider configuration details when registering an external OIDC provider with Supervisor.
| Field | Importance | Description |
|---|---|---|
| Provider Name |
Required |
User-defined name for the external identity provider. |
| Issuer URL |
Required |
The URL to the identity provider issuing tokens. The OIDC discovery URL is derived from the issuer URL. For example, the Okta Issuer URL may look like the following and can be obtained from the Admin console: https://trial-4359939-admin.okta.com. |
| Username Claim |
Optional |
The claim from the upstream identity provider ID token or user info endpoint to inspect to obtain the user name for the given user. If you leave this field empty, the upstream issuer URL is concatenated with the "sub" claim to generate the user name to be used with Kubernetes. This field specifies what Pinniped should look at from the upstream ID token to determine to authenticate. If not provided, the user identity will be formatted as https://IDP-ISSUER?sub=UUID. |
| Groups Claim |
Optional |
The claim from the upstream identity provider ID token or user info endpoint to inspect to obtain the groups for the given user. If you leave this field empty, no groups are used from the upstream identity provider. The Group Claims field tells Pinniped what to look at from the upstream ID token to authenticate user identity. |
OAuth 2.0 Client Details
Refer to the following provider OAuth 2.0 client details when registering an external OIDC provider with Supervisor.
| OAuth 2.0 Client Details | Importance | Description |
|---|---|---|
| Client ID |
Required |
Client ID from the external IDP |
| Client Secret |
Required |
Client Secret from the external IDP |
Additional Settings
Refer to the following additional settings when registering an external OIDC provider with Supervisor.
| Setting | Importance | Description |
|---|---|---|
| Additional Scopes |
Optional |
Additional scopes to be requested in tokens |
| Certificate Authority Data |
Optional |
TLS certificate authority data for secure external IDP connection |
| Additional Authorize Parameters |
Optional |
Additional parameters during the OAuth2 Authorization request |