This section describes the configuration of the Avi Load Balancer for Workspace ONE (WS1) access.
VMware Identity Manager combines applications and desktops in a single, aggregated workspace. Employees can then access the desktops and applications regardless of where they are based. With fewer management points and flexible access, Identity Manager reduces the complexity of IT administration.
There are five Workspace ONE Access services in scope for load balancing:
Horizon IDM Service – This is the primary service powering the catalog and all the Access settings.
CertProxy – Android SSO using TLS mutual authentication.
KDC – iOS SSO using Kerberos pk-init authentication.
CertAuth Service – Pure TLS mutual authentication.
Integrated Windows Auth/Connector – Domain joined Kerberos authentication.
In this section, we are covering configuration steps for all these five services. It is not mandatory to have all these in place, so check the requirement to understand which services need to be configured. It is assumed that services 1 to 4 are running on the same backend servers on different ports.
Prerequisites
Ensure the new FQDN for Identity Manager is in DNS with both forward and reverse records and points to the virtual server IP address on the Avi Load Balancer that will be used for load balancing the Identity Manager appliances.
Note:VMware recommends using certificates that support Subject Alternate Names (SANs) defining each of the node FQDNs (public or internal) within the load-balanced VIP FQDN.
Wildcard certificates can be used, but due to wildcard certificate formats, SAN support is typically not available with wildcards from public CAs - and public CAs can complain about supplying an internal FQDN as a SAN value even if they do support SAN values. Additionally, some VMware Identity Manager features may not be usable with wildcard certificates when SAN support is not defined.
For information on the pre-requisites and deployment instructions for Workspace ONE Access, see System and Network Configuration Requirements.
During the deployment of theVMware Identity Manager machine, you enter the VMware Identity Manager FQDN and port number. These values must point to the host name that you want end users to access. The VMware Identity Manager machine always runs on port 443. You can use a different port number for the load balancer. If you use a different port number, you must specify it during deployment. Do not use 8443 as the port number, as this port number is the VMware identity Manager administrative port and is unique for each machine in a cluster.
vIDM Connectors are required to implement Kerberos AuthN for domain joined workstations.
For information on Load Balancer recommendations, see Using a Load Balancer or Reverse Proxy to Enable External Access to VMware Identity Manager.
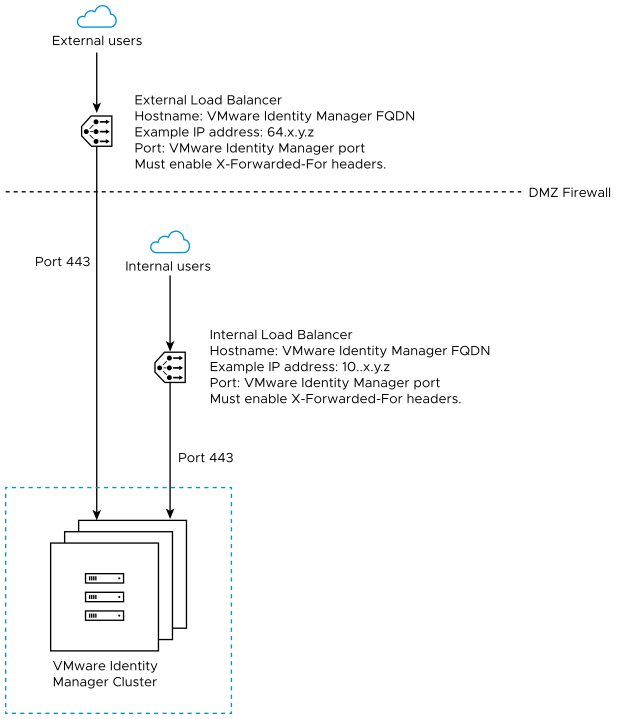
External Load Balancer Proxy with Virtual Machines
During deployment, theVMware Identity Manager instance is set up inside the internal network. If you want to provide access to the service for users connecting from outside networks, you must install a load balancer in DMZ. If you do not use a load balancer or reverse proxy, you cannot expand the number of VMware Identity Manager instances later. You might need to add more instances to provide redundancy and load balancing.
The following diagram shows the basic deployment architecture that you can use to enable external access.
Avi Load Balancer Configuration Entities
Application and TCP/UDP Profile
Service/Component |
Application Profile |
TCP/UDP Type |
TCP Timeout(in seconds) |
|---|---|---|---|
IDM Horizon |
HTTP Profile |
TCP-Proxy |
3600 |
Cet Proxy |
System-L4-Application |
TCP-Proxy or TCP-Fast Path |
1800 |
Cert Auth |
System-L4-Application |
TCP-Proxy or TCP-Fast Path |
1800 |
KDC-TCP |
System-L4-Application |
TCP-Proxy or TCP-Fast Path |
1800 |
KDC-UDP |
System-L4-Application |
UDP-Proxy or UDP-Fast Path |
1800 |
Connector/IWA |
HTTP Profile |
TCP-Proxy |
3600 |
Monitors
Service/Component |
Monitor Type |
Health Monitor Recommendation |
Health HTTP Response Code |
|---|---|---|---|
IDM Horizon |
HTTPS:443 |
GET /SAAS/API/1.0/REST/system/health/heartbeat |
200 OK |
Cet Proxy |
HTTPS:5262 |
GET /system/health |
200 OK |
Cert Auth |
HTTPS:7443 |
GET /SAAS/API/1.0/REST/system/health/heartbeat |
200 OK |
KDC |
TCP:88 |
NA |
NA |
Connector/IWA |
HTTPS:443 |
GET /hc/API/1.0/REST/system/health/allOk |
200 OK |
Persistence Profile
Service/Component |
Persistence Type |
Persistence Timeout |
|---|---|---|
IDM Horizon |
Cookie |
Session Cookie |
Cet Proxy |
Source IP |
3600 seconds |
Cert Auth |
Source IP |
3600 seconds |
KDC |
Source IP |
3600 seconds |
Connector/IWA |
No |
N/A |
Client SSL Profile
There is no recommended profile as such. However, if you have iOS users, then Apple iOS App Transport Security requirements apply to the Workspace ONE app on iOS. To enable users to use the Workspace ONE app on iOS, the load balancer must have ciphers with forward secrecy. The following ciphers meet this requirement: ECDHE_ECDSA_AES and ECDHE_RSA_AES in GCM or CBC mode as stated in the iOS 11 iOS Security document.
Server SSL profile
There is no recommended profile as such. However, if you have iOS users, then Apple iOS App Transport Security requirements apply to the Workspace ONE app on iOS. To enable users to use the Workspace ONE app on iOS, the load balancer must have ciphers with forward secrecy. The following ciphers meet this requirement: ECDHE_ECDSA_AES and ECDHE_RSA_AES in GCM or CBC mode as stated in the iOS 11 iOS Security document.
Pool
Service/Component |
Port |
Load Balancing Algorithm |
Persistence |
SSL Profile |
|---|---|---|---|---|
IDM Horizon |
443 |
Least Connection |
Cookie |
WS1-access-ServerSSL |
Cet Proxy |
5262 |
Least Connection |
Source IP Address |
WS1-access-ServerSSL |
Cert Auth |
7443 |
Least Connection |
Source IP Address |
WS1-access-ServerSSL |
KDC |
88 |
Least Connection |
Source IP Address |
N/A |
Connector/IWA |
443 |
Least Connection |
No |
WS1-access-ServerSSL |
Virtual Service
Service/Component |
VIP:Port |
Virtual Service Type |
Pool |
|---|---|---|---|
IDM Horizon |
IP1:443 |
L7:HTTPS |
IDM Horizon-Pool |
Cet Proxy |
IP1:5262 |
L4:TCP |
CertProxy-Pool |
Cert Auth |
IP1:7443 |
L4:TCP |
CertAuth-Pool |
KDC |
IP1:88 |
|
KDC-Pool |
Connector/IWA |
IP2:443 |
L7-HTTPS |
Connection IWA-Pool |