External services are services that exist outside the VMware Tanzu Service Mesh (for example, third-party database services) but are made accessible by services within a global namespace of the VMware Tanzu Service Mesh. Services can run on virtual machines, external Kubernetes clusters, Tanzu Application Service environments, lambda functions or even on bare metal, and can be accessed over TCP, TLS, HTTP, or HTTPS.
As an example, a service in a global namespace of Tanzu Service Mesh requires access to an external database or web service that is running outside the mesh. When the internal service attempts to communicate with the external service, the communication flows through the envoy proxy as a sidecar, which allows all traffic by default. Tanzu Service Mesh, on the other hand, defines service-layer policies, and these policies are transmitted to the envoy proxy, which allows or denies egress traffic as necessary. Tanzu Service Mesh also automates the creation of routing rules, destination rules, and gateway configuration for these external services.

To connect to an external service in Tanzu Service Mesh, you need to describe its configuration in the global namespace. Currently, the external services can be accessed over protocols such as HTTP, HTTPS, TCP, and TLS.
Note:
The following steps explain how to configure an external service from the Tanzu Service Mesh UI:
Prerequisites
Create a global namespace to which you can add the external service. For information about creating a global namespace and adding services to it, see Connect Services Across Clusters with a Global Namespace.
If you want to use an HTTPS or TLS protocol to connect to the external service, add a TLS certificate. The certificate must match the domain you specify for the external service. This certificate will be used to encrypt incoming and outgoing traffic for the service. Private Keys are optional, and only Public Keys are mandatory when adding a certificate to External Services. For more information, see Manage Certificates.
Note:
Adding a TLS certificate is not mandatory. For external sites like google.com and amazon.com that use HTTPS, public certificates are already trusted by the client, so it is not necessary to add certificates. For
Procedure
- On the Home page, on the GNS Overview tab, in the card for the global namespace that contains the external service, click the name or topology of the global namespace.
- Click Edit Configuration, go to the External Services page by clicking Next on the General Details page and then on the Namespace Mapping page.
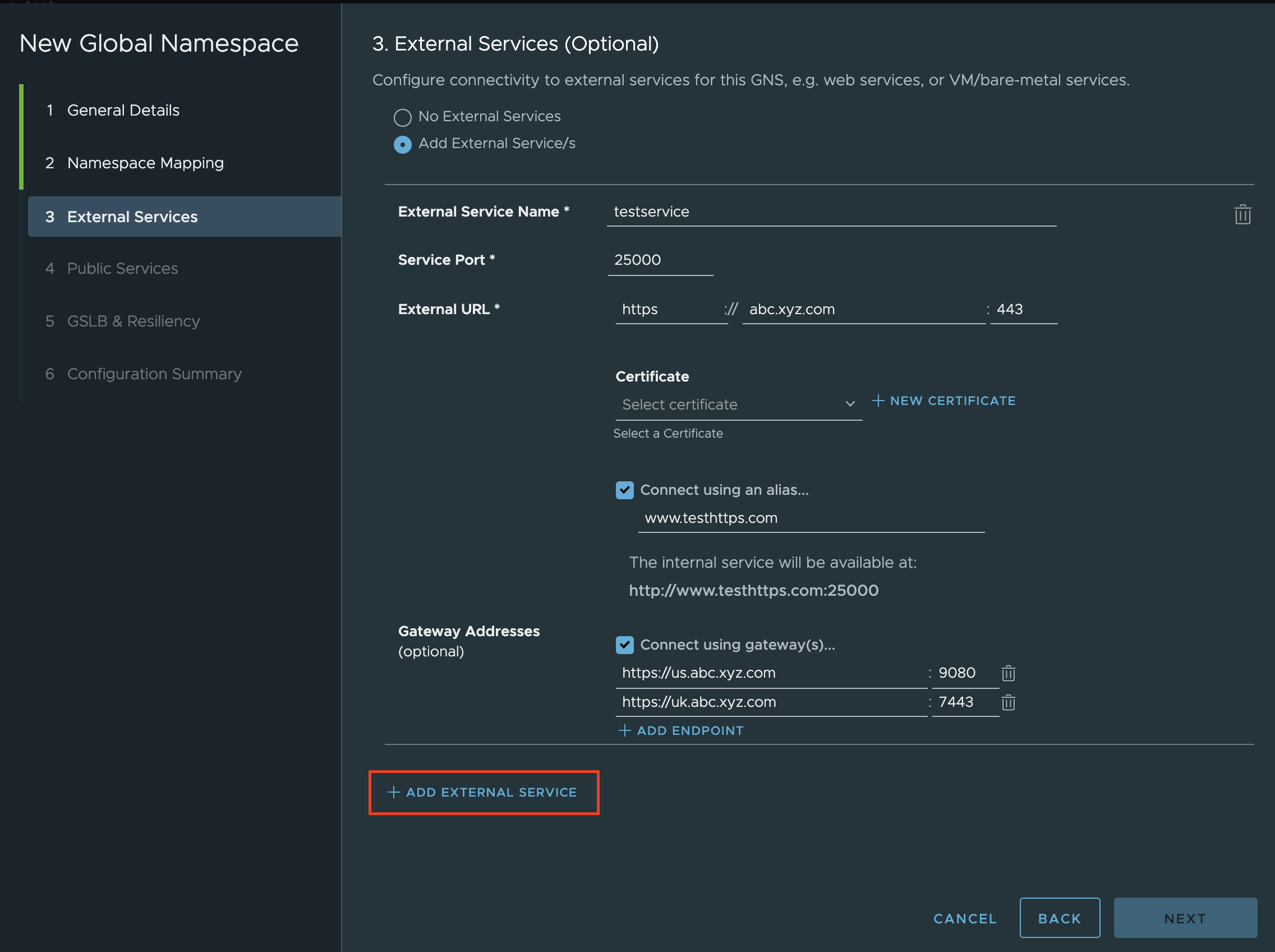
- On the External Services page, click Add External Service(s) and perform these steps:
- In External Service Name, enter a unique name for the external service you are connecting to so that it can be identified. Once created, the external service name cannot be edited.
- In Service Port, specify the port through which the service can be accessed.
- Next to External URL, specify the parts of the URL at which the service will be accessible: the protocol, domain, and port number {protocol + FQDN hostname + monolith port number}.
Attention:
When using HTTPS or TLS protocols, the Service port and the Port for the External URL shouldn't be the same.
- (Optional) If you specify HTTPS or TLS in Protocol, you can select the name of the certificate that you want to use for the service. You can select from the certificates that your administrator has defined. For more information, see Add Custom Certificate.
Important:
For a TLS or HTTPS external service, the service port must not match any of the endpoints or external URL ports.
A service inside a Tanzu Service Mesh global namespace can only access TLS external service via TCP (even though the external server is using TLS).
A service inside a Tanzu Service Mesh global namespace can only access HTTPS external Service through HTTP protocol (even though the external server is HTTPS).
Table 1.
Custom TLS Version Support
TLS version |
TLS version option |
TLS version 1.0 |
TLSV1_0 |
TLS version 1.1 |
TLSV1_1 |
TLS version 1.2 |
TLSV1_2 |
TLS version 1.3 |
TLSV1_3 |
TLS versions 1.2 and 1.3 are enabled by default. Envoy filter can be edited to enable the other two TLS versions if desired.
- (Optional) To define an internal URL to access the external service, click Connect using an alias and enter the domain name. The host name would be used if there is no alias provided.
Note:
It is important that the alias name is a Fully Qualified Domain Name (FQDN).
- (Optional) In Gateway Addresses, select Connect using gateway(s) , click Add Endpoint, and provide the endpoint (IP address or domain name) if you wish to connect the external service using a gateway to manage the egress traffic.
Attention:
Multiple Endpoint Support
You can specify multiple endpoints and load balance between them. Tanzu Service Mesh supports load-balancing for multiple endpoints in all four protocols, including HTTPS, HTTP, TLS, and TCP.
Considerations:
Make sure you configure endpoints of the same protocol only, for example, you shouldn't configure HTTP and HTTPS endpoints under the same external service.
You can either create a new external service with multiple endpoints or edit an existing external service with an extra endpoint.
Run the same server on multiple endpoints.
Configuration:
In Gateway Addresses section, configure multiple external service endpoints.
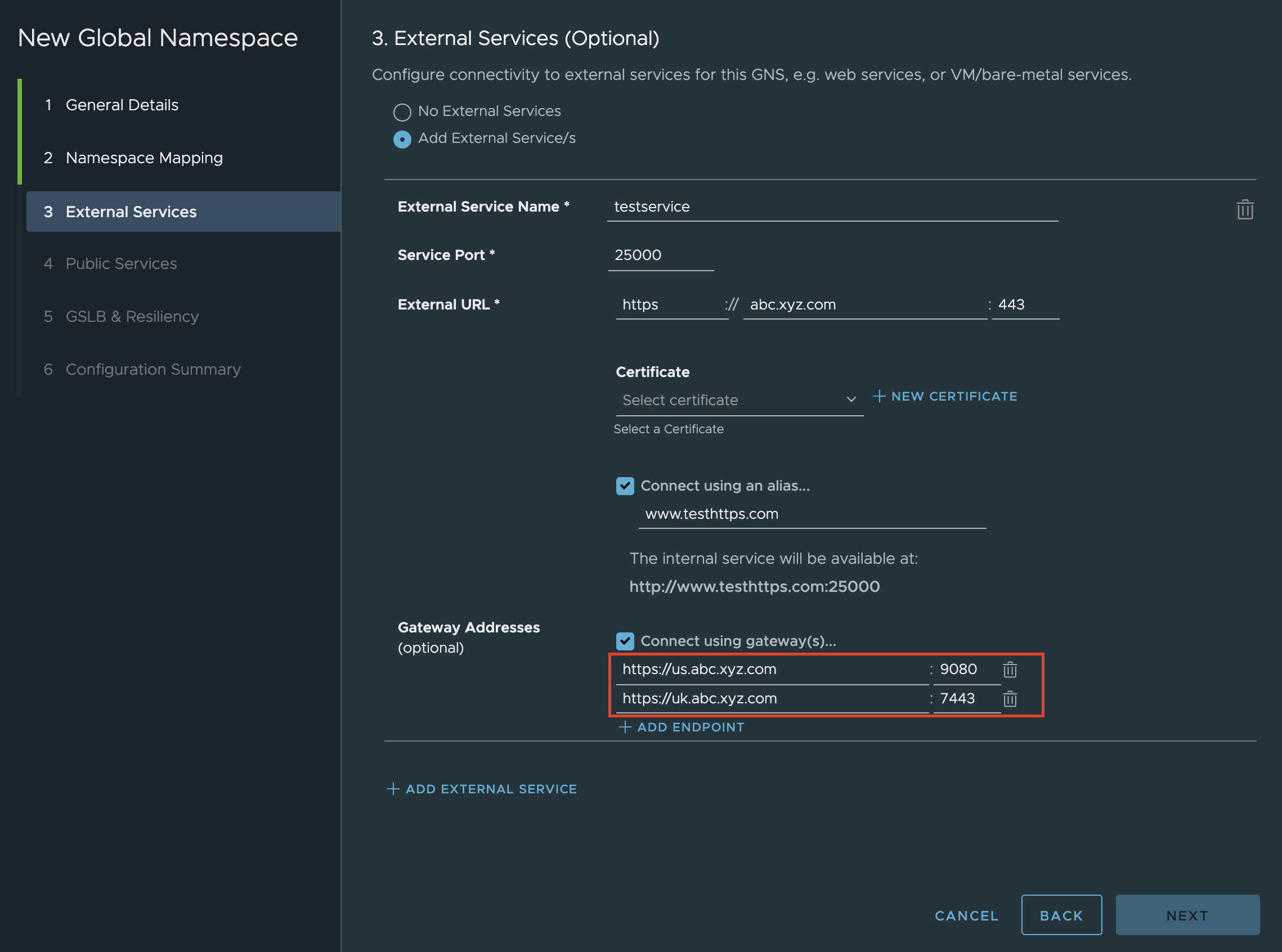
Once you enter multiple endpoints under gateway addresses in the UI, round-robin will be set as the default load-balancing scheme. You do not need to configure global load balancing (GSLB) for the external services. It is possible to check the traffic being load balanced between two servers as follows:
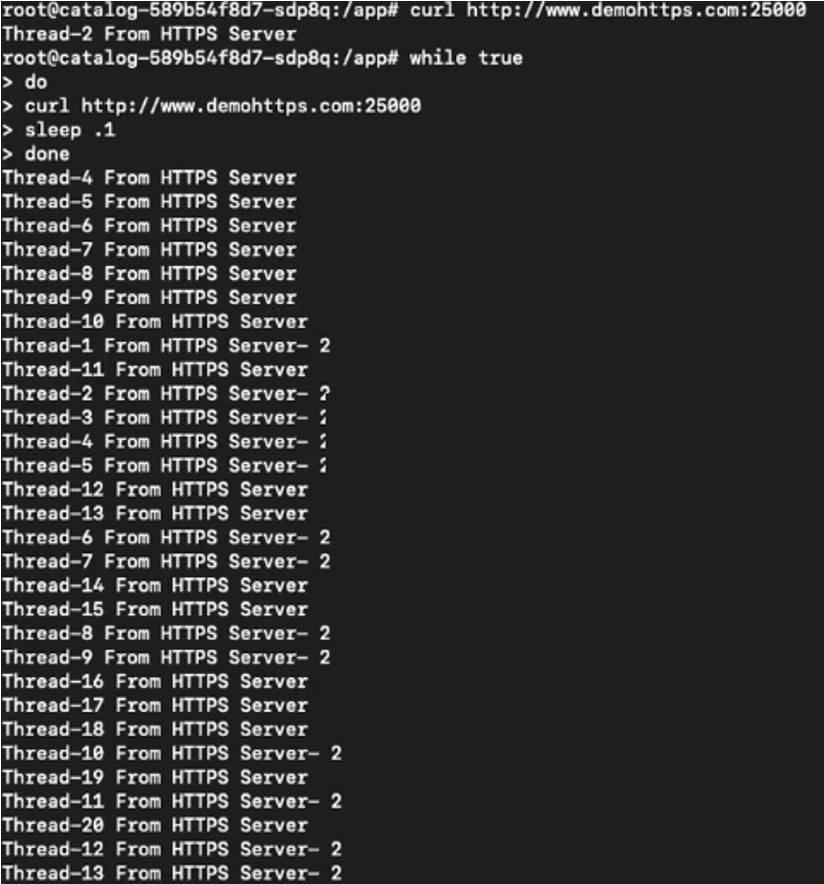
Warning:
For multiple service endpoint configurations, the service port and the gateway port must be different.
- To configure additional external service in the global namespace, click Add External Service and repeat steps a–f.
- Click Next.
- To save the external services you have configured in the global namespace, click Finish.
The External Services page displays the names of the configured external services, external URL at which each service is accessible, and other details. To access this page:
On the Home page, click the GNS Overview tab.
In the card for the global namespace in which the external service is configured, click the name of the global namespace.
Select the External Services tab.
(Optional) To view the names of the configured external services, the URL and port at which each service is accessible, click Configuration tab on the same page.
Results
The external service has been configured successfully. To edit the configuration of an external service or configure additional external services in the global namespace, perform steps 1 –5 of this procedure.
Note:
With future enhancements, users will be able to define traffic management and access control policies for external services.
What to do next
For information about editing the configuration of an external service, see Edit an External Service Configuration.
For information about how to monitor the performance of external services with metric charts and view its details, see Monitor the Performance of External Services.