A secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. It is often used to authenticate users or services to control access to sensitive information or external services. Secret management is an essential tool to help control and enforce the distribution of secrets across workloads. This section describes how to detect and prevent statically defined secrets that are deployed in Kubernetes environments.
Carbon Black Cloud secret management can help you detect and prevent static secrets that are injected into the workload. You can use a policy rule to detect and prevent secrets.
Data regarding secrets is available on the following pages in the Carbon Black Cloud console:
Roles
The following roles can use Carbon Black Cloud secret management.
DevOps and DevSecOps
- Detect and prevent statically defined secrets in containers at the image build phase.
- Inspect image information to help detect potential security or compliance violations.
- Inspect workload information to help detect potential security compliance violations.
- Deny workloads that use images with static secrets through policy to help enforce security and compliance.
- Explore and mitigate static secret policy violations.
- Include secrets in the existing explore, prioritize, and mitigate risk process.
- Detect files that contain statically defined secrets.
- Scan all deployed images for secrets.
DevOps and Developer
- Inspect image information to help detect potential security compliance violations.
- Explore and mitigate static secret policy violations.
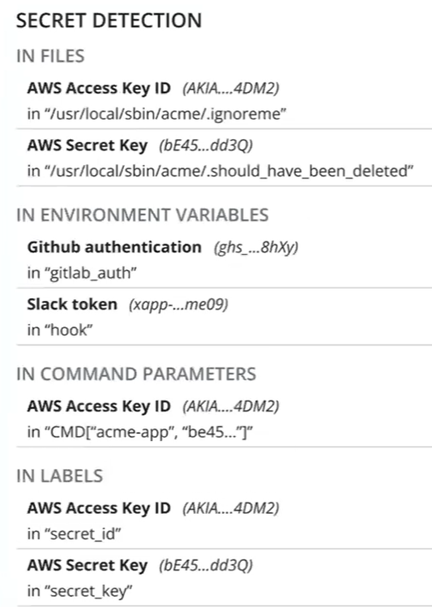
Secret Detection
Secrets are detected in the following ways:
Data Types
The following table provides an example of the captured secret data types.
| Source | Category | Secret Type | Secret Key | Secret Value |
|---|---|---|---|---|
| /.aws | FILE | Keyword Detector | aws_access_key_id | JKSN...3E3Q |
RUN /bin/sh -c eco hi --password "pddj...f837" # buildkit |
COMMAND | Keyword Detector | password | pdhj...f837 |
| azure | LABEL | Azure Storage Account access key | azure | abcd...uv== |
| GITHUB_KEY | ENVIRONMENT_VARIABLE | Github authentication | GITHUB_KEY | ghu_...UKpr |
Secret Types
The following table lists the types of secrets that Carbon Black Cloud detects.
| Azure Storage Account access key |
JFrog Artifactory credentials |
AWS Client ID |
| AWS Secret Key | Amazon Marketplace Web Service (MWS) Key |
HTTP Bearer Authentication |
| URL with password |
Github authentication | JSON Web Token |
| Mailchimp API Key |
npm auth token |
Private Key |
| Sendgrid API key |
Slack token |
Square authentication |
| Stripe API key |
Twilio authentication |