As a platform operator, you can use Tanzu Mission Control to create and manage secrets for use in your clusters.
Tanzu Mission Control allows you to create image pull secrets in a namespace that allow namespaces in managed clusters to authenticate to private registries, including registries that store Tanzu Application Platform components.
You can also make a secret created in one namespace available for use by other namespaces in your cluster, providing a single place to manage secrets for the cluster. The secret is a Tanzu Mission Control resource.
About secret generation and exporting
Tanzu Mission Control leverages secretgen-controller to manage the export of secrets to all other namespaces in the cluster. This does not copy the secret into other namespaces, but allows other namespaces to request access to, and use that secret.
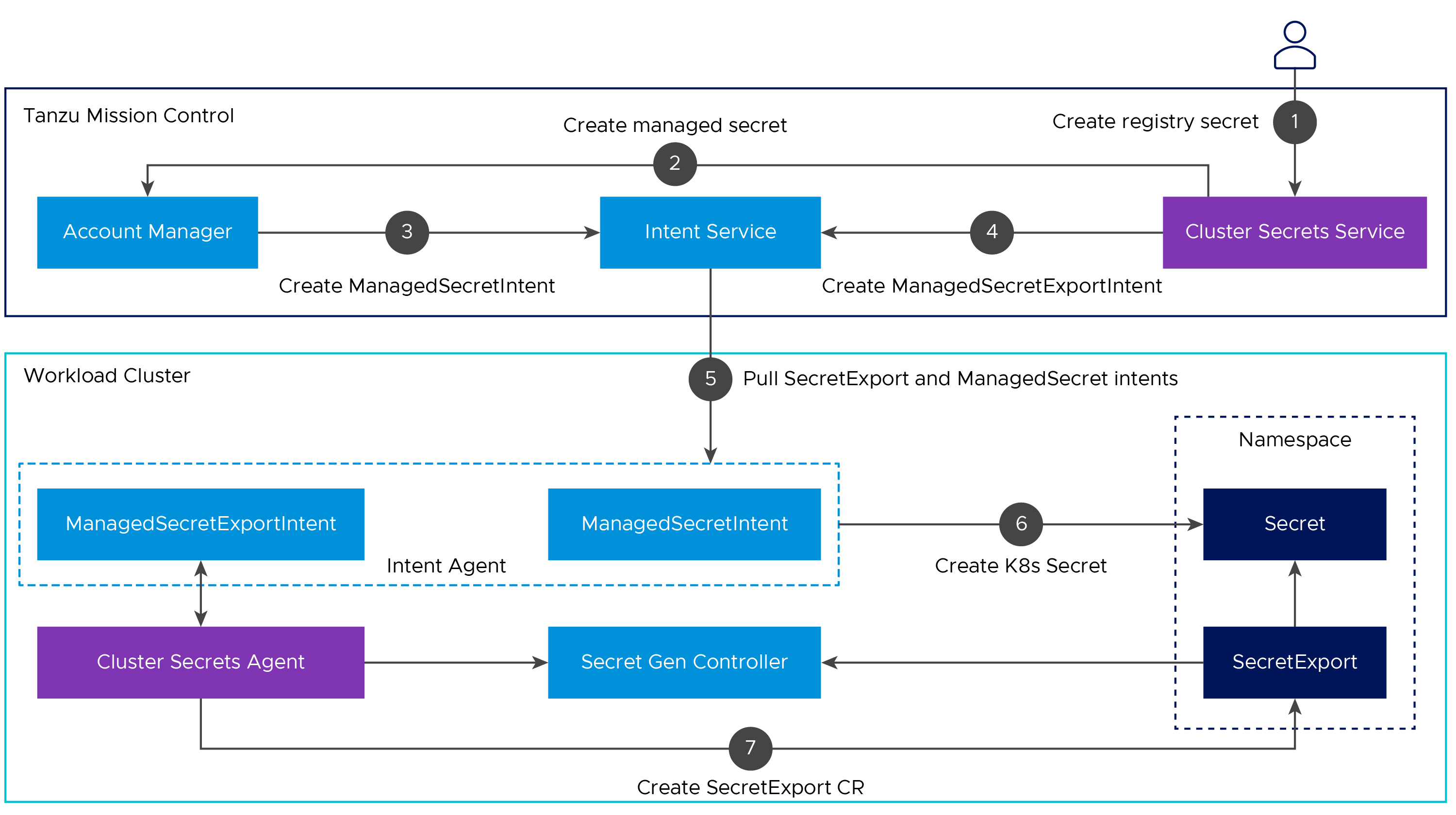
As shown in the architecture diagram below, Tanzu Mission Control creates and exports secrets using the cluster secret service. When a secret is created and exported to all namespaces through this service, Tanzu Mission Control stores the secret using the account manager service and uses the secure channel with the in-cluster intent agent to provision the secret to the cluster and to send the secret export intent to the cluster secret agent, a new in-cluster agent.
The cluster secret agent is responsible for deploying secretgen-controller, and for creating secret export CRs that are picked up by secretgen-controller.
As a best practice, export only credentials that allow read-only access to the registry.
For more information about secretgen-controller, see secretgen-controller in the Carvel documentation on GitHub.