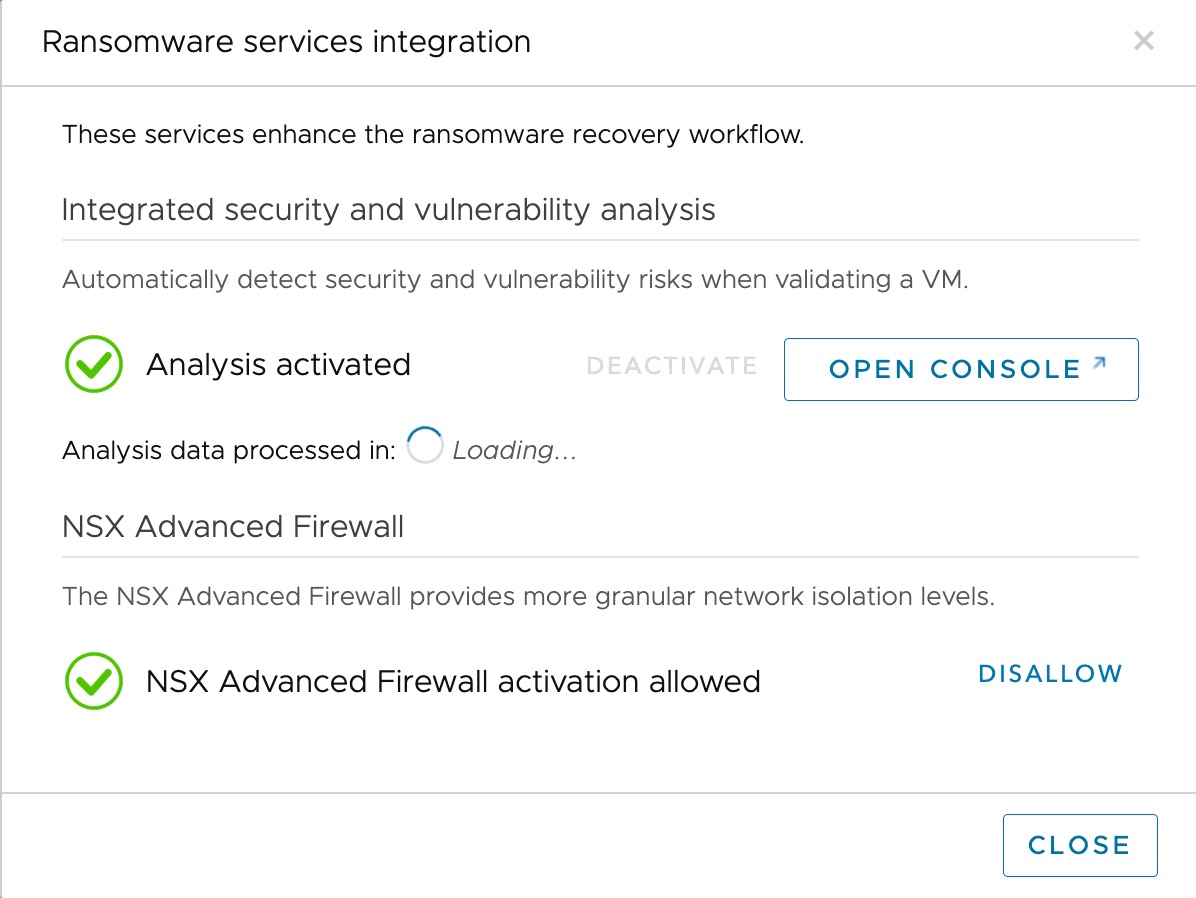
To use ransomware recovery with integrated security and vulnerability analysis, you first must enable the services.
Enable integrated security and vulnerability analysis in your recovery plans to recover from a ransomware attack (or to test one). When you run a recovery plan for ransomware recovery, integrated vulnerability and behavioral analysis and malware signature scanning begins.
Allowing Activation of NSX Advanced Firewall
VMware NSX Advanced Firewall for VMware Cloud on AWS is required to enable advanced network isolation levels, including the useful 'quarantine isolation' with Carbon Black Cloud access.
NSX Advanced Firewall activates a full range of network isolation levels when performing validation on the recovery SDDC. You can authorize VMware Live Cyber Recovery to automatically activate the advanced firewall only during ransomware recovery or testing.
When you activate NSX Advanced Firewall and run a ransomware recovery plan, VMs in validation are started in the Quarantined+Analysis network isolation level.
For more information, see NSX Advanced Firewall for VMware Cloud on AWS.
Activating ransomware recovery services requires the following user roles: Organization Owner, Global Console Admin, and Orchestrator Admin.
Procedure
What to do next
Once you have activated ransomware recovery services, you can create a protection group and a recovery plan. Then you can recover VMs if you experience a ransomware attack. If you want to change the country selected for data analysis, see Change Country for Ransomware Data Analysis.